Industrial environments emerge to become more tempting to cyber attackers, Positive Technologies says
Recent data released by Positive Technologies reveals that the industrial sector has become increasingly attractive to hackers in recent years. Attacks are getting more successful and their scenarios more complex, while organizations often cannot detect a targeted cyberattack on their own. They may remain under the illusion of security for years on end, considering the likelihood of cyber risk actuation to be minimal.
The situation is exacerbated when such companies have blind faith in the reliability of security automation tools and do not put infrastructure robustness to the test, according to data released by Positive Technologies. Unfortunately, security assessments prove that attackers can easily gain access to such systems.
Positive Technologies provides enterprise security solutions for vulnerability and compliance management, incident and threat analysis, and application protection. It offers insights on industrial control systems, banking, telecom, web application, and ERP security, supported by recognition from the analyst community.
While industrial companies attract criminals due to their size, the importance of business processes, and their impact on the world and people’s lives, cyberattacks on industrial companies with such serious consequences are just isolated cases, as they require a higher level of attacker qualification, Positive Technologies said in its data analysis.
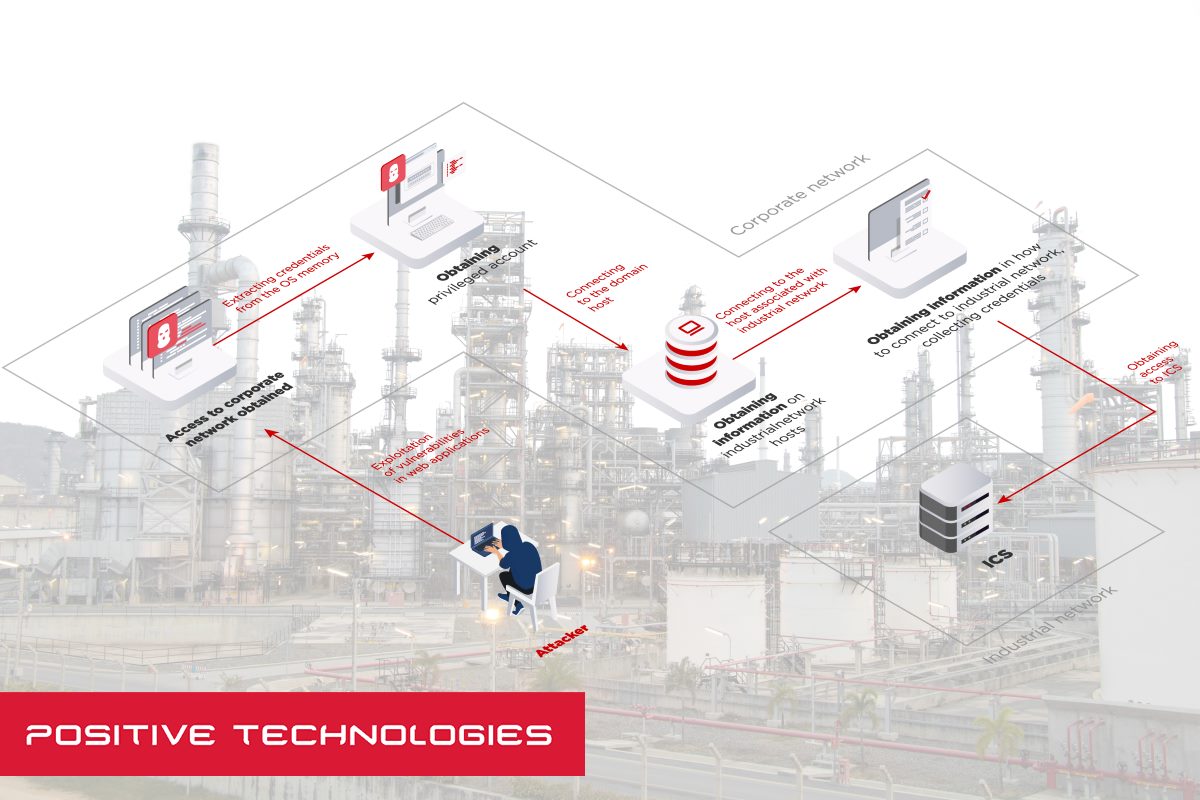
Positive Technologies revealed that security assessments conducted in 2020 revealed that in 91 percent of industrial organizations, an external attacker can penetrate the corporate network. Once inside the internal network, attackers can obtain user credentials and gain complete control over the infrastructure in 100 percent of cases, and in 69 percent of cases, they can steal sensitive data, including information about partners and company employees, email correspondence, and internal documentation.
At about three-fourths of industrial companies, experts from Positive Technologies managed to gain access to the technological segment of the network. This allowed criminals to obtain access to industrial control systems in 56 percent of cases.
The PT NAD pilot projects conducted by the firm revealed numerous suspicious events in the internal network of each industrial company, it added. PT NAD is a deep network traffic analysis system used to detect attacks on the perimeter and in the network. PT NAD knows everything that is going on in the network, detects malicious activity even in encrypted traffic, and facilitates incident investigation, according to Positive Technologies.
Positive Technologies said that most industrial companies have a very low level of protection against attacks. Common vulnerabilities identified include a low level of protection of the external network perimeter accessible from the Internet, a low level of protection against hackers penetrating the industrial network, device misconfiguration, flaws in network segmentation and traffic filtering, dictionary passwords, and the use of outdated software.
Industrial companies often use outdated software. An industrial cybersecurity firm, Claroty revealed earlier this year that the number of vulnerabilities in ICS components has grown steadily in recent years. In 2020, security experts detected 25 percent more vulnerabilities than in 2019, mostly affecting the energy sector, manufacturing, and water treatment plants. The problem is that to update industrial equipment, a special ‘maintenance window’ is required, which is only allowed a few hours a week or even a month.
In May this year, networks at fuel pipeline company Colonial Pipeline were affected by the DarkSide ransomware, which led the company to take certain systems offline to contain the threat. Colonial had a temporary halt of all pipeline operations with some of its IT systems also affected, and currently in the process of restoring.
Last June, the corporate network of automaker Honda was struck by a ransomware attack, which led the company to halt production at several plants for a full day. After such an attack, it takes a lot of effort for the company to return to normal operations, restore the complete functionality of technological and business systems, and prevent a recurrence of such incidents in the future.
“It is much harder to update and protect ICS software which use obscure protocols. The key is segmenting the IT and OT/ICS networks and focus on reducing the chances of someone penetrating the IT network and especially the computers on the IT side that control the OT/ICS network,” Saumitra Das, CTO and co-founder at Blue Hexagon wrote in an emailed statement. “It is common for the IT and OT air gap to be compromised for convenience in such organizations so do not assume the air gap exists in a way that will thwart attackers completely. “
“Detecting attacks on the OT/ICS side is also good but is usually very late and risky. It is like detecting ransomware that has begun to encrypt already. You want to detect and mitigate the foothold infection rather than wait for the final payload,” Das added.










