Internet, removable media, email emerge as main threat sources in ICS computers
Kaspersky released data that showed a big rise in the percentage of attacked ICS computers during the first half of this year, with the internet emerging as the main source of threats causing these increases. Africa and Southeast, East and Central Asia are leading in the ranking of global regions based on the percentage of ICS computers on which malicious activity was prevented.
During the same period, the percentage of attacked ICS computers was 33.8 percent, higher than that recorded in the second half of 2020. The lowest percentage of ICS (industrial control systems) computers on which malicious objects were blocked was recorded in February and the highest percentage was recorded in March. Per country, the number varied from 58.4 percent in Algeria to 6.8 percent in Israel. When tracking regional numbers, Africa led with 46.1 percent, followed by Southeast Asia at 44.1 percent, East Asia at 43.1 percent, and Central Asia at 42.1 percent, Kaspersky said.
Titled, “Threat landscape for industrial automation systems Statistics for H1 2021,” the report was released by the Kaspersky Industrial Control Systems Cyber Emergency Response Team (Kaspersky ICS CERT). The security firm identified that the internet, removable media, and email continue to be the main sources of threats to computers in ICS environments. Threats from the internet were blocked on 18.2 percent of ICS computers.
During the first half of this year, Kaspersky said that indicators in all selected industries decreased, particularly in oil and gas, and building automation. Computers used in building automation systems often have the same attack surface as ordinary corporate systems, which is broader than the attack surface of ICS computers. Such computers can be connected to the corporate network and have access to various services, such as the internet, corporate email, and domain controller.
Building automation systems often belong to contractor organizations and are not always controlled by the corporate information security service, even when they have access to the company’s corporate network, it added.
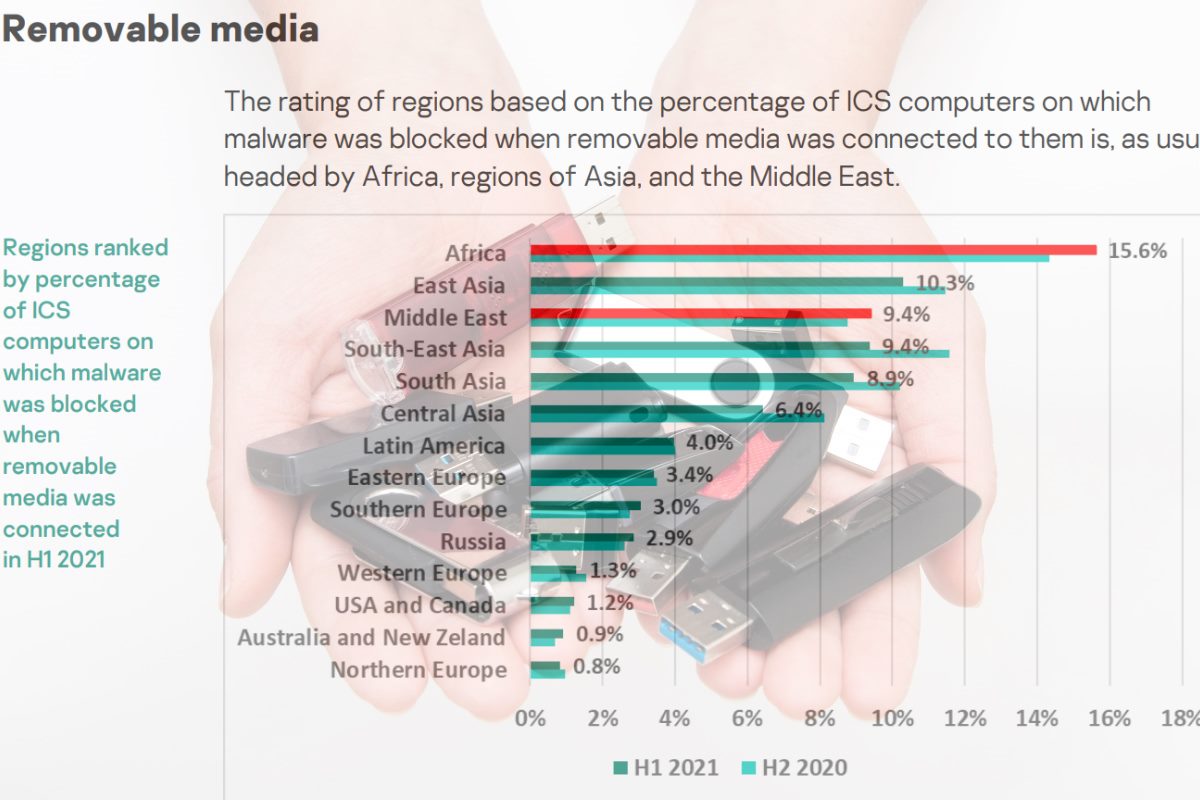
The security firm identified the largest increase in internet threats was observed in Belarus, Ukraine, and Russia. Russia headed this rating among regions with 27.6 percent and Belarus among individual countries with 32.8 percent. When accounting for the threats emerging from removable media connections, 5.2 percent of ICS computers were blocked, which continues a downward trend beginning in the second half of 2019, according to Kaspersky. When it came to threats coming through removable media, Africa noticeably leads amidst regional rankings with 15.6 percent, and Algeria leads among individual countries with 24 percent.
Kaspersky said in its report that during the first half of this year, the percentage of ICS computers on which threats were blocked when removable media were connected to them decreased in Asian regions.
Malicious email attachments were blocked on 3.4 percent of ICS computers. Southern Europe was the highest-ranked region for this indicator with 6.4 percent, while Bangladesh led among individual countries with 8.8 percent. The only region where the percentage increased was Australia and New Zealand, according to Kaspersky.
When recording the variety of malware detected in the first half of this year, data revealed that Kaspersky security solutions blocked over 20.1 thousand malware variants from 5,150 families in ICS environments. The number of malware families has slightly decreased in the first six months this year compared to the previous six months but remains higher than the numbers recorded in the previous eighteen months, Kaspersky said.
In addition, an analysis of malware samples found an established practice whereby attackers offer popular malware (particularly spyware), families, using the MaaS (malware-as-a-service) model. Rather than create ‘their own’ unique malware, attackers use ready-made malware that is often customized to meet their needs, which does not require them to have any software development skills, Kaspersky said. The increase in the number of unique malware samples is also due to attackers using malware obfuscation services on a massive scale to prevent the malware from being detected.
The ‘denylisted internet resources’ were the main threat source and subsequently blocked on 14 percent of ICS computers. Hackers use malicious scripts on various media resources and sites hosting pirated content. These scripts redirect users to websites that spread spyware and/or cryptocurrency miners. The percentage of computers where such threats have been blocked has been growing since 2020.
Malicious scripts and redirects (JS and HTML) were blocked on 8.8 percent of ICS computers, Kaspersky data found. Australia and New Zealand, as well as Russia, saw noticeable growth in the percentage of computers where malicious downloader scripts used for downloading spyware were blocked. Malicious scripts are used by hackers on various media resources and websites hosting pirated content to redirect users to sites that distribute spyware and/or malware designed to mine cryptocurrency without the user’s knowledge.
Kaspersky data reported that when it came to spyware – backdoors, Trojan spies, and keyloggers – 7.4 percent were blocked on ICS computers, with the highest recorded in East Asia at 14.3 percent, Africa at 13.4 percent, and Southeast Asia at 11.2 percent.
Kaspersky reported that ransomware was blocked on 0.40 percent of ICS computers, with the highest detected in East Asia with 0.82 percent. In the Middle East, the firm saw an increase in the percentage of computers on which worms and ransomware were blocked.










