MITRE releases D3FEND framework as a complement to its existing ATT&CK structure
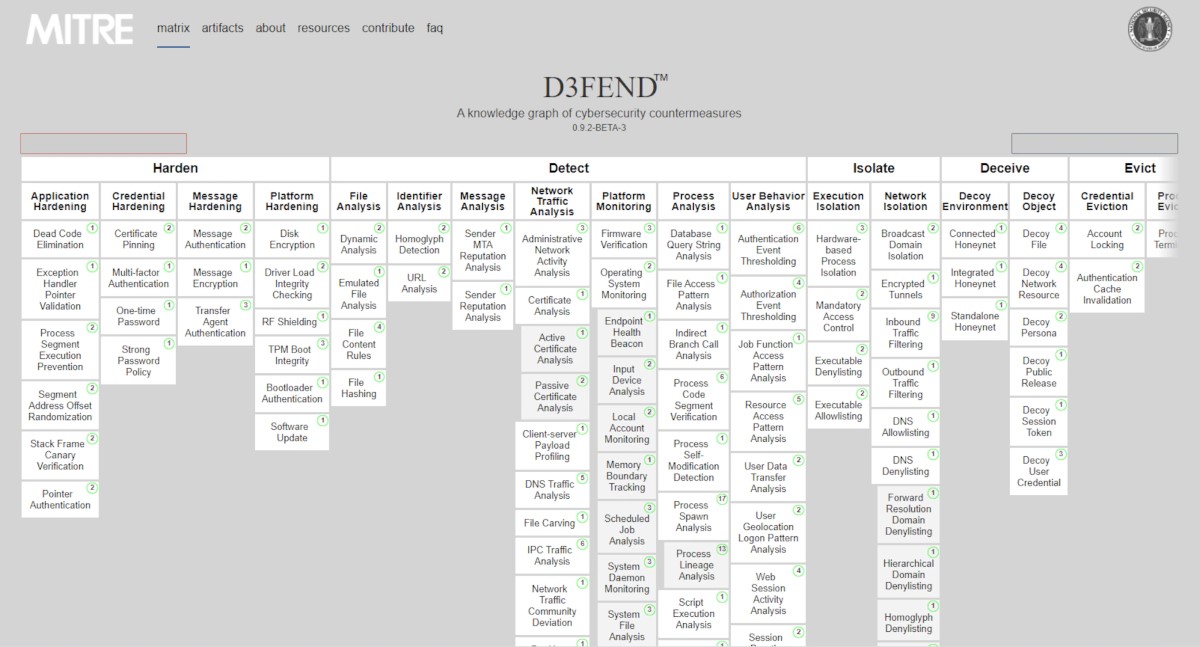
The National Security Agency (NSA) announced Tuesday that the MITRE project has released the D3FEND framework, funded by the agency. The new framework aims to improve the cybersecurity of national security systems, the Department of Defense, and the defense industrial base, in addition to adding defensive cybersecurity techniques to the existing ATT&CK framework.
The D3FEND framework is a free, globally accessible knowledge base of cyber adversary tactics and techniques based on real-world observations. Industry and government use ATT&CK as a foundation to develop specific cyber threat models and methodologies. It consists of a technical knowledge base of defensive countermeasures for common offensive techniques and supplements the MITRE ATT&CK.
MITRE is a not-for-profit organization working with federal, state and local governments, as well as industry and academia, to bring ideas into existence in various areas, including artificial intelligence, intuitive data science, cyber threat sharing, and cyber resilience. The ATT&CK framework consists of a knowledge base of cyber adversary behavior and taxonomy for adversarial actions across their lifecycle.
“Frameworks such as ATT&CK and D3FEND provide mission-agnostic tools for industry and government to conduct analyses and communicate findings,” the NSA said in its press statement. “Whether categorizing adversary behavior or detailing how defensive capabilities mitigate threats, frameworks provide common descriptions that empower information sharing and operational collaboration for an ever-evolving cyber landscape,” it added.
The knowledge base of the D3FEND framework estimates operational applicability, identifies strengths and weaknesses and develops enterprise solutions comprising multiple capabilities, based on the fact that it is necessary that practitioners know not only what threats a capability claims to address, but, specifically how those threats are addressed from an engineering perspective, and under what circumstances the solution would work
D3FEND is primarily concerned with abstract and generic semantics versus vendor-specific terminology or technical jargon. However, analysis of technical jargon is usually required to select effective semantics, and in some cases create or define useful new semantics. To address this recurring need in the near term, MITRE created D3FEND framework, in which it can encode a countermeasure knowledge base, but more specifically, a knowledge graph. The graph contains semantically rigorous types and relations that define both the key concepts in the cybersecurity countermeasure domain and the relations necessary to link those concepts to each other, according to a technical resource.
“The D3FEND framework is at an early stage and the initial release is not considered comprehensive. The defensive to offensive technique mappings (which are inferentially generated) are considered fundamental generalizations. However, expert cybersecurity knowledge is often, at its essence, the application of fundamental computer system knowledge. We aim to codify this knowledge in our knowledge graph and expect improvement over time as the graph builds on itself,” the MITRE Corporation said in an FAQ.
The D3FEND framework has multiple audiences, with the most immediate being security systems architecture experts and technical executives making an acquisition or investment decisions. It can be used to compare the claimed functionality in multiple product solution sets with a common defensive technique taxonomy, making it possible to identify product differences and product gaps relative to desired functionality in a more precise, consistent, and repeatable manner.
It also suggests a potential testing scope for defensive techniques in terms of relevant offensive techniques. The research team developed the model in a bottom-up fashion, linking each countermeasure through specific citations to the literature, and integrating those into higher-level abstractions while using patents, existing knowledge bases, and other data sources.









