Industrial Cyber Experts
Addressing complexities of zero trust implementation in OT/ICS environments to bolster cybersecurity
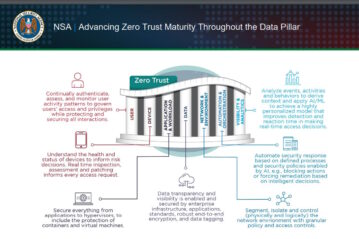
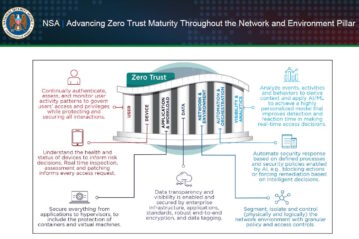
Incorporating a zero-trust framework into OT (operational technology) and ICS (industrial control system) environments becomes imperative in addressing...
Read full story
Cybersecurity Strategies and Best Practices for Manufacturing
Hello there, and a very Happy New Year 2024 to all of you! Welcome back to our article...
Read full story