Industrial Cyber Experts
Continuous need to face challenges, build strategies across industrial cybersecurity amidst evolving threats
Rising cyber threats and attacks against critical infrastructure installations have led to the constant adaptation of the changing...
Read full story
Comprehensive Guide to Integrated Operations (Part 4)
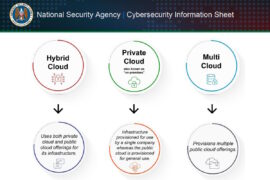
Network and OT Cyber Security Requirements: ICT for Integrated Operations In Integrated Operations, where Information and Communication Technology...
Read full story
Addressing complexities of zero trust implementation in OT/ICS environments to bolster cybersecurity
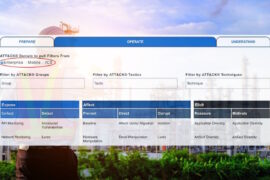
Incorporating a zero-trust framework into OT (operational technology) and ICS (industrial control system) environments becomes imperative in addressing...
Read full story
Navigating industrial cyber threats with SBOMs, VEX, CSAF for enhanced supply chain resilience
A significant rise in cybersecurity threats and attacks, particularly targeting software supply chains, has led to heightened scrutiny...
Read full story