Network segmentation must be baked into industrial operations for unified security
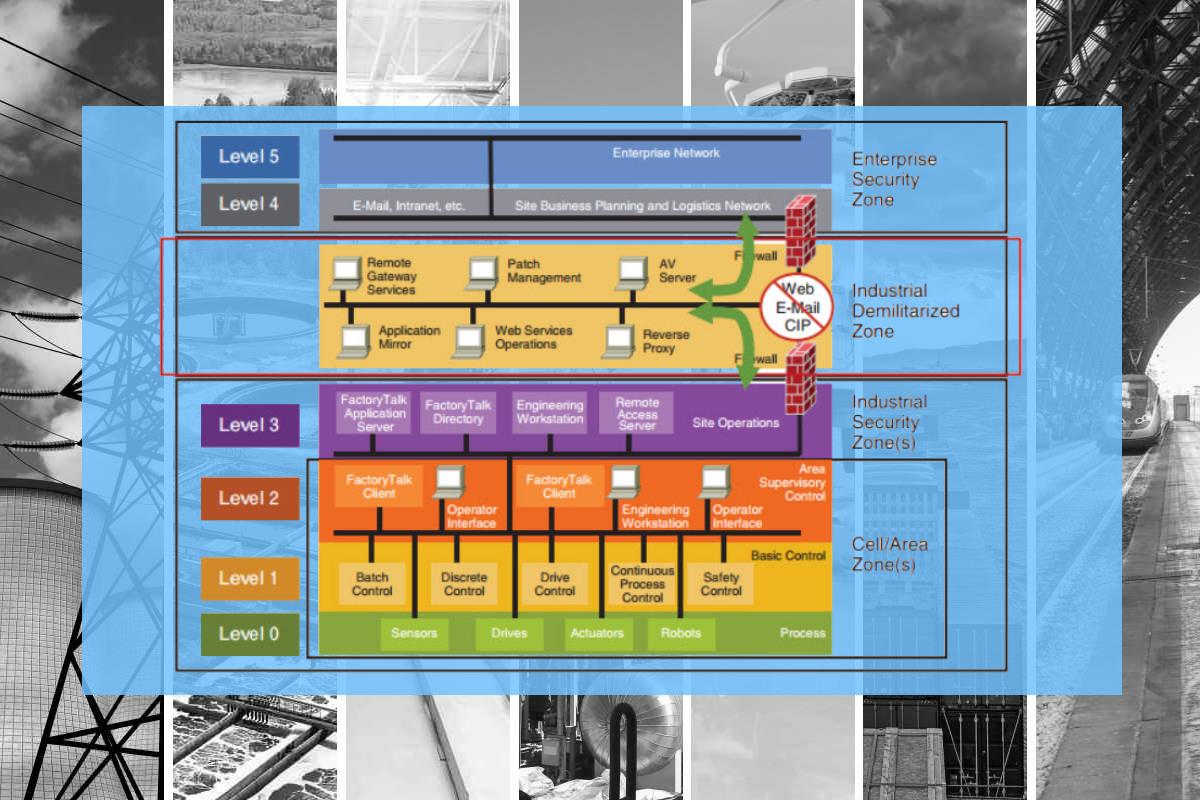
Industrial and manufacturing enterprises are looking to secure their environments from the rising number and sophistication of cybersecurity attacks on their core operations, and network segmentation has emerged as one of the “go-to” approaches.
As a practical consideration in defining a security domain, network segmentation aims to minimize access to sensitive information for those systems and people who don’t need it, while ensuring that the rest of the organization can continue to operate effectively. Effective network segmentation will partition critical ICS (industrial control systems), and create secure baselines that conform with industry best practices.
By placing tabs on the amount of communications traffic that crosses the domain boundary, organizations can partition every layer of the network into various zones, effectively creating a demilitarized zone (DMZ) network architecture with firewalls to prevent network traffic from passing directly between the corporate IT and ICS networks. Network segmentation enables network administrators to control the flow of traffic between subnets based on granular policies and construct a micro-perimeter around the protection surface, forming another line of defense.
The National Institute of Standards and Technology (NIST) defines network segmentation as “splitting a network into sub-networks, for example, by creating separate areas on the network which are protected by firewalls configured to reject unnecessary traffic. Network segmentation minimizes the harm of malware and other threats by isolating it to a limited part of the network.”
Network segmentation establishes security domains, or enclaves, which have been clearly defined as being managed by the same authority, enforcing similar policies while delivering a uniform level of trust. It can minimize the method and level of access to sensitive information, ICS communication and equipment configuration, making it increasingly more difficult for a malicious cyber adversary, and containing the effects of non-malicious errors and accidents. ICS networks and corporate networks can be sorted out in such a way that cybersecurity can be enhanced using different architectures.
Analyst firm Gartner in recent research pointed out that recent events like the Colonial Pipeline ransomware attack have highlighted the need to have properly segmented networks for IT and OT environments. It called for OT networks to be physically or/and logically separated from any other network both internally and externally. All network traffic between an OT and any other part of the network must go through a secure gateway solution like a DMZ, while interactive sessions to OT must use multi-factor authentication to authenticate at the gateway, Gartner advised.
With the rise in cybersecurity incidents, network segmentation alone cannot be counted on to respond to attacks in time. Response time is a more extensive process factor, typically with human intervention, John Adams, Mission Secure’s CEO told Industrial Cyber.

John Adams, Co-Founder & CEO, Mission Secure
“For example, if you have a security system installed in your home but never arm it, the security system isn’t the issue; the user is,” Adams said. “Network segmentation is one tool – although very important – to achieve security, but it alone will not protect operations. It merely slows down the attack or minimizes its impact. Alerts, processes, policies, etc., need to be established around it to support real-time incident responses, among other actions,” he added.
Armis’ CTO for OT, Sachin Shah pointed out that ICS development paralleled the evolution of microprocessors, personal computers, and networking technologies during the 1980’s and 1990’s, and Internet-based technologies started making their way into ICS designs in the late 1990’s.
“These changes to ICSs exposed them to new types of threats and significantly increased the likelihood that ICSs could be compromised,” Shah told Industrial Cyber. “The rise in cyber intrusion does not default to network segmentation but more so that these systems were purpose-built for performance, availability and deterministic nature, and having resource constraints for real-time operating systems (RTOS) which were not built with security posture in mind. Security and protection were an afterthought,” he added.
“No, we don’t believe that the lack of network segmentation can be solely held responsible for failing to prevent or respond to attacks/incidents in a timely manner,” Obbe Knoop, WW VP, OT Security at Armis, said. “We believe the lack of overall visibility into the Industrial networks is the main culprit. If you don’t know what you have and don’t know what is happening in real-time in your industrial or manufacturing environment, you can’t really protect it or respond to incidents in a timely fashion. Network segmentation doesn’t really change that!”
Likewise, Chris Bihary, Garland Technology’s CEO / co-founder said that the challenges with segmented architecture are not necessarily the failure to respond to attacks or incidents. “The failing comes with not properly architecting packet visibility into these dispersed or separate systems so they can effectively monitor threats to have the chance to respond properly, without creating blindspots where hackers can thrive,” he added.
While deciding on network segmentation, organizations have two structures – flat networks, where all devices can connect to each other without going through any other hardware, with fast and reliable connectivity for all connected devices, and the more complex segmented network, which can greatly limit lateral movement once breached.
Organizations must scrutinize the traffic requirements of their operations, and only permit and monitor that traffic by the appropriate network devices. They also can deploy firewalls to filter traffic between defined network segments, thereby restricting and controlling access to sensitive data. In the case of a hack of classified data, it is easier to identify and isolate the source.
In practice, network segmentation is a range measured by the robustness deployed, according to Mission Secure’s Adams. “An operation could have two segments, and in that way, not technically be categorized as ‘flat,’ but neither is it secured. That’s where vendors and the larger supply chain ecosystem is,” he told Industrial Cyber.
“Whether an operation’s networks are flat or segmented likely doesn’t have a causal relationship on whether it is a target; that is just one of many factors adversaries can consider,” Adams told Industrial Cyber. “But the network’s segmentation definitely impacts the success of an attack. And today, we mostly see evidence of insufficient network segmentation – it’s not flat, but neither is it segmented enough to stop or mitigate damages,” he added.
Shah said that to achieve the deterministic and robustness requirements of an ICS, process control networks (PCN) are often configured in flat network structures with little or no boundary limits between the different components of an ICS. “This inherently flat network structure of the PCN makes it faster and easier to maintain. Critical infrastructure is often referred to as a ‘system of systems’ because of the interdependencies that exist between its various industrial sectors as well as interconnections between business partners,” he added.
“Critical infrastructures are highly interconnected and mutually dependent in complex ways, both physically and through a host of information and communications technologies. An incident in one infrastructure can, directly and indirectly, affect other infrastructures through cascading and escalating failures,” Shah added. 
Historically, vendors in the manufacturing industry have been utilizing flat networks to help simplify deployments and operations, according to Armis’ Knoop. “Over the last years, more focus has been placed on network segmentation and breaking up these flat networks, to minimize potential cyber threat exposures and prevent potential outages,” Knoop said.
Knoop does not believe that flat networks are the main reason for the increased cybersecurity incidents in these environments but believes that the main reason cyber hackers have started targeting industrial and manufacturing environments is the lack of basic security controls and measures being applied by companies to their industrial networks.
“Most companies don’t even know what exactly is deployed in their industrial networks, have old legacy systems that can’t be patched and a multitude of unmanaged/ unmonitored external vendor connections, which is easy prey for potential hackers,” Knoop added.
There are still a lot of companies in industrial and manufacturing, even in the financial sector, that still utilizes a flat network architecture, according to Bihary. “A lot of the ransomware breaches we are seeing are exposing flat networks because once a bad actor has accessed the network, they are able to easily move laterally,” he added.
Shah sees the need for network and device segmentation to be part of the defense-in-depth security strategy for critical ICS environments.
“It provides a much more robust security posture than simple perimeter-only defense. With perimeter-only protection, once an adversary gains access, nothing prevents them from traversing the network unchallenged. Segmentation and micro-segmentation stop unbridled access in IT environments and should be doing the same in ICS environments,” he added.
Network segmentation should definitely be considered a component, according to Mission Secure’s Adams. “It really comes down to deploying a zero-trust approach to security. That’s the philosophy operations need to take, and segmentation is a core component. A zero-trust approach addresses numerous challenges for industrial and manufacturing operations. Asset diversity, patch management, third-party access – segmentation gives operations a realistic medium to achieve these challenges,” he added.

Chris Bihary CEO Garland Technology
To Garland’s Bihary, network segmentation is effective architecture, but there are a couple of components OT teams should consider when deploying proper asset inventory and threat detection solutions.
“One is instrumenting proper packet visibility to those security tools is critical. If you cannot see everything crossing the network, you are not going to be able to protect it. I cannot stress this enough. Understanding network TAP technology and how it can be used to solve this is fundamental in today’s ICS systems. And two, when you have segmented architecture, utilizing Data Diode TAP technology to ensure you are sending unidirectional data across locations to your security solution, so it not only performs with optimal data but that you also have a secured air-gapped segment is very important,” according to Bihary.
Recent cybersecurity attacks have led to a need for stronger ICS security and segmentation, and Garland’s Bihary is seeing this every day. “Especially in the face of mounting pressure from the government setting guidelines and requirements to catch the industry upon cybersecurity strategies. But these companies face a big challenge upgrading legacy and distributed systems that have been in place for decades,” he added.
Interactions with customers and potential customers have been significantly more substantive in nature than in the past, according to Adams.
“ICS networks have been targeted for years; for years, operations took the ‘not me’ mindset. The change we’ve seen recently is the interconnectedness of sectors and operations,” according to Adams. “Today, organizations realize they aren’t just worried about the security of their own operations but also their vendors, supply chains, customers, etc. And on the flip side, companies that rely on them are worried about their security. So, the pressure and visibility have escalated significantly, and hopefully, that leads to tangible change and action across sectors,” he added.
Armis’ Knoop sees the recent cybersecurity attacks as an opportunity that organizations use to start focusing on improving the overall security posture of their industrial environments and not just network segmentation.
“Most companies are still struggling to try to understand what has really been deployed in their industrial networks, what network connections exist, and what vulnerabilities they might have. Without that information, network segmentation is basically impossible to properly deploy, and is somewhat of an impossible exercise,” Knoop added.
Bihary expects the trend for IT and OT integration on the shop floor to continue, as companies look to improve their efficiency. “Instrumenting proper packet visibility into both IT and OT systems will ensure security tools can properly protect how they were designed. This is a critical yet often overlooked component. Blindspots in either of your IT or OT systems is where vulnerabilities surface and breaches happen,” Bihary added.
Mission Secure says that it depends on the operation, but regardless of the level of IT and OT integration in the current shopfloor, there are no signs of slowing down. “The gains from sharing data are significant for operations. For example, sharing real-time data on coil production with inventory, purchasing, shipping, etc., allows each function to measure and pivot, if necessary, in real-time. This boosts efficiency, minimizes dwell time, lowers inventory costs, etc,” according to Adams.
Notably, a continuous exchange of information is not mutually exclusive to security. “This is another example where segmentation can mitigate risk while facilitating this digital transformation,” Adams said. “The processes are known, so creating zones around each with communication flows (uni/bi-directional), baselining (anomaly detection), access control, etc., can allow these data flows to exist securely,” he added.

Sachin Shah, Chief Technology Officer, OT at Armis
The converged ICS/OT and IT infrastructure ensure that communication is no longer based on proprietary network communication protocols, Shah said. “Instead, the converged ICS/OT and IT network relies on a combination of complex proprietary and open standard communication protocols that are inherently vulnerable to various attacks. This expands the network’s attack surface and makes traditional security controls, such as VLANs, insufficient for ICS, especially as OT and IT networks converge,” Armis’ Shah added.
“Although defining zones and conduits and segmenting networks into levels are essential for ICS/OT and IT convergence, it doesn’t entirely address network security challenges within a converged infrastructure. VLANs are not sufficient to prevent sophisticated network attacks,” he added.










