New white paper addresses challenges faced in federal facility control system cybersecurity
A National Academies of Sciences white paper revealed that control systems have no cybersecurity, and some are intentionally built to be open for ease of remote access. The paper said that in effect control systems can be an open door into otherwise well-protected IP networks. They can also be hacked and their data signals compromised. This situation can leave entire facilities vulnerable to devastating attacks even if they have rigorous cybersecurity in place, demonstrated by multiple recent cyber incidents that have left various corporations completely incapacitated.
Authored by Joseph Weiss, managing partner at Applied Control Solutions, the white paper titled ‘Challenges in Federal Facility Control System Cyber Security, Including Level 0 and 1 Devices’ addresses changes to improve cybersecurity, productivity, process safety, predictive maintenance, and resilience, while also breaking down cultural and organizational barriers. It also highlights the presence of critical flaws in current cybersecurity approaches for all physical infrastructures, including federal facilities. It assesses that cybersecurity for Level 0,1 devices, which include sensors and the Industrial Internet of Things (IIoT), is underdeveloped.
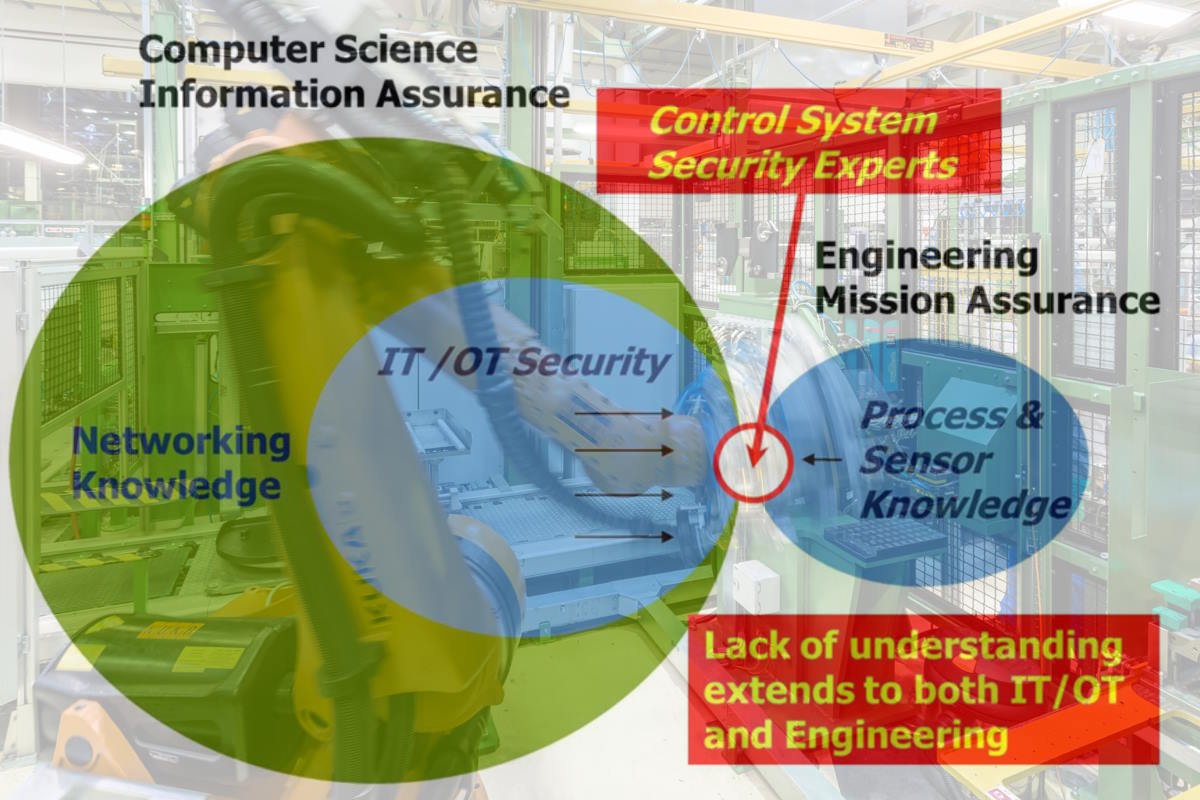
The white paper presents a paradigm change for control system cybersecurity to move from a primarily network-based approach to an engineering issue that will result in improved process reliability, process safety, predictive maintenance, improved productivity and product quality, resilience, and cybersecurity. It also outlines significant cultural gaps between the IT and control systems communities, despite many efforts to bring them together.
Control systems include various component systems, including distributed control systems (DCS), supervisory control and data acquisition (SCADA) systems, programmable logic controllers (PLCs), remote terminal units (RTUs), intelligent electronic devices (IEDs), process sensors, actuators, drives, power supplies, chemical analyzers, and building control units.
Weiss added that cybersecurity for Level 0 and Level 1 devices operating on a time scale ranging from milliseconds to seconds, is ‘particularly underdeveloped.’ “Addressing this gap requires fundamental changes in cybersecurity education, funding and implementation, and integration between departments that are currently operating separately, as well as a significant paradigm shift to monitoring process sensors in real-time. Movement in these areas would result in improved cybersecurity, productivity, process safety, predictive maintenance, and resilience, while also breaking down cultural and organizational barriers,” he added.
Weiss said that networking and control systems engineering organizations and the corresponding educational curricula fail to overlap, yet control systems security sits at the intersection of these two fields. “The good news is that the educational gap between these two disciplines is being explored by Brad Sims at Capital University, Glenn Dietrich at the University of Texas-San Antonio, George Markowsky at the University of Missouri Science and Technology, Sean McBride at Idaho State University, and faculty at Everett Community College.”
Recent developments in this area are encouraging, Weiss added. “A Level 0 or 1 process sensor monitoring project is being carried out at a large industrial facility for productivity and predictive maintenance (the identity of the company is intentionally not being disclosed). Cybersecurity is an important consideration, but not the primary motivation for the project, which is efficiency and productivity improvement.”
As a result, initially, some of the business and IT organizations that would be involved in cybersecurity table-top exercises, incident response, etc., were not involved, but they were, fortunately, included later.
Pointing out that IT and control system communities have different backgrounds and goals that occasionally conflict, Weiss added that despite the IT community’s focus on cybersecurity, cyber threats are still a concern even with the newest IT cybersecurity technologies, as seen in the SolarWinds cyberattack, where a reputable and competent cybersecurity company was hacked.
He also pointed to the presence of a culture gap between IT and control systems and OT security, a gap that sometimes leaves these communities with conflicting priorities. This culture gap is driven, in part, by the dearth of cybersecurity organizations that address Level 0 and Level 1 devices which results in open holes in otherwise well-protected IP networks and is also a result of the differing and sometimes conflicting priorities between the IT (preventing data loss) and OT operators and asset owners (ensuring safety, reliability, and productivity).
The white paper also said that currently, almost all cyber policy organizations are led by a Chief Information Security Officer (CISO), who is typically not an engineer, nor would they generally be aware of the operational needs of the facilities and engineering communities. Because few cyber policy organizations include senior representatives from engineering or facilities organizations, IT network security technologies, testing and updates have frequently negatively impacted control systems or plant operations.
Weiss also pointed out in the white paper that process sensors do not use COTS operating systems, and many have built-in backdoors for maintenance considerations. “Level 0 and 1 field devices use remote calibration and maintenance tools that have direct Internet connections and minimal cybersecurity capabilities. These maintenance backdoors cannot be bypassed. These maintenance backdoors cannot be disabled by asset owners.”
However, in some cases, asset owners can control access to these backdoors by using appropriate security controls, such as network firewall rules, Weiss said. “Valve motor operators do not use COTS operating systems either, thus precluding standard patching capabilities. These cybersecurity limitations of Level 0 and Level 1 devices may mean that IT and OT cybersecurity technologies cannot be employed for control systems; these limitations are situationally dependent.”
Level 0 and 1 devices are often the least understood part of control system cybersecurity, yet they can have some of the most significant impacts, Weiss underscores. Unfortunately, as is true more broadly with all control systems, there are no cybersecurity, authentication, cyber logging, or other tools that can help determine whether a sensor has been remotely compromised.
Experience has shown that sensors are not as accurate as assumed, not all sensor failure modes are understood, cybersecurity standards and government organizations have largely ignored process sensor cybersecurity and integrity, and instrument engineers and instrument technicians are not part of cybersecurity programs, have minimal training in cybersecurity, and continue to design cyber insecure sensors and sensor systems.
Weiss also pointed out in the white paper that sensor input is not authenticated. This makes it difficult to determine whether sensor outputs are coming from the sensors or spoofed signals. The actuators, drives, controllers, etc. receiving the sensor signals have no way to authenticate the signal origin, and they automatically accept the sensor and respond to the given commands. “To say the least, these processes are a far departure from the zero trust security model. Improving our cybersecurity necessitates the transformation of an intractable network monitoring approach into a tractable engineering program,” he added.
Addressing facility control systems cybersecurity, Weiss said that these systems use hardware, software, firmware, and communication protocols that mostly lack any cyber protection and are thus vulnerable to cyber incidents. “Facility control systems are used in modern buildings to manage the functions of a wide range of facilities. They control processes in manufacturing plants and public utilities (both production and distribution), as well as maintain environmental conditions in areas that are sensitive to variations.”
He added that facilities contain a variety of complex systems. “Every facility has water intake, distribution, and discharge systems, just like industrial facilities. Likewise, every facility has some form of a heating, ventilation, and air conditioning (HVAC) system, ranging from basic environmental control (e.g., humidity and temperature) to more complex systems that monitor particulates and regulate air pressure and the direction of airflow. Furthermore, every facility has some sort of lighting control system. The newer environmental and lighting control systems react to the presence of people in specific areas in order to optimize the use of power and other resources.”
“Similar to other industries, the facility OT networks are often subnets inside subnets with multiple organizational silos. Facilities can have multiple management platforms that have remote access, which can be a source of cyber vulnerabilities,” Weiss said. “The cybersecurity of facilities is currently addressed in industry organizations such as BacNet.org, with BACnet Secure (BACnet undated), and ISA111, Unified Automation for Buildings (ISA 2022b). However, these standards do not address the Level 0 and Level 1 devices, so parts of these systems remain vulnerable.”
Weiss points out that a paradigm change to monitoring sensor signals and conditions would have many advantages. The raw signals from process sensors would provide the ground truth about the physical operation of the process in question. A system to monitor these raw signals would detect anomalies regardless of the source rather than first ‘seeing’ the sensor inputs once they have entered the OT network.
As a result, it would not be susceptible to either unintentional or intentional IT or OT network compromises, including ransomware attacks and vulnerabilities from patches in the manner of the SolarWinds hack, he added. “This would provide a level of sensor signal authentication that otherwise would not exist. Because such a system would also provide sensor health monitoring capability, maintenance intervals could be lengthened rather than relying on scheduled maintenance. Such sensor monitoring systems would also provide risk reduction and reduce the impacts of cyber incidents.”
In conclusion, Weiss wrote that the critical flaw in facilities’ cybersecurity is the lack of cybersecurity, authentication, and cyber logging in process instrumentation. “If users cannot trust incoming measurements, they have no cybersecurity, safety, or resilience. This gap and the related organizational culture differences between IT personnel and facility engineers needs to be addressed in order to improve the confidence in and safety, performance, and resilience of facility control systems,” he added.










