Australian CIRMP rules come into force, set to uplift core security practices of critical infrastructure assets
The Australian government announced Friday that its CIRMP (Critical Infrastructure Risk Management Program) rules have now been registered under the Security of Critical Infrastructure Act 2018 (SOCI Act). The move calls upon specified responsible entities to develop and maintain the written program that identifies and manages ‘material risks’ of ‘hazards’ that could have a ‘relevant impact’ on a critical infrastructure asset.
The Cyber and Infrastructure Security Centre (CISC) wants the CIRMP obligation to complement and where relevant, enhance existing practices. Organizations have a six-month grace period after the commencement of the rules until Aug.17, 2023, the Fact Sheet outlined. The final day for a CIRMP to adopt and comply with the cyber and information security hazards framework will be Aug. 17, 2024, which is 18 months from the guidelines’ start date.
Additionally, Sept. 28 annually will be the last day to submit an annual report for the preceding Australian financial year (i.e. ending Jul. 1 to Jun. 30). As part of the ongoing process, organizations must comply with, regularly review and if required update the CIRMP.
The Fact Sheet added that if a responsible entity’s asset becomes a critical infrastructure asset after the rules commence. The responsible entity must meet CIRMP requirements within six months of the day the asset became a critical infrastructure asset and must meet the cyber and information security hazards framework within 18 months of that day.
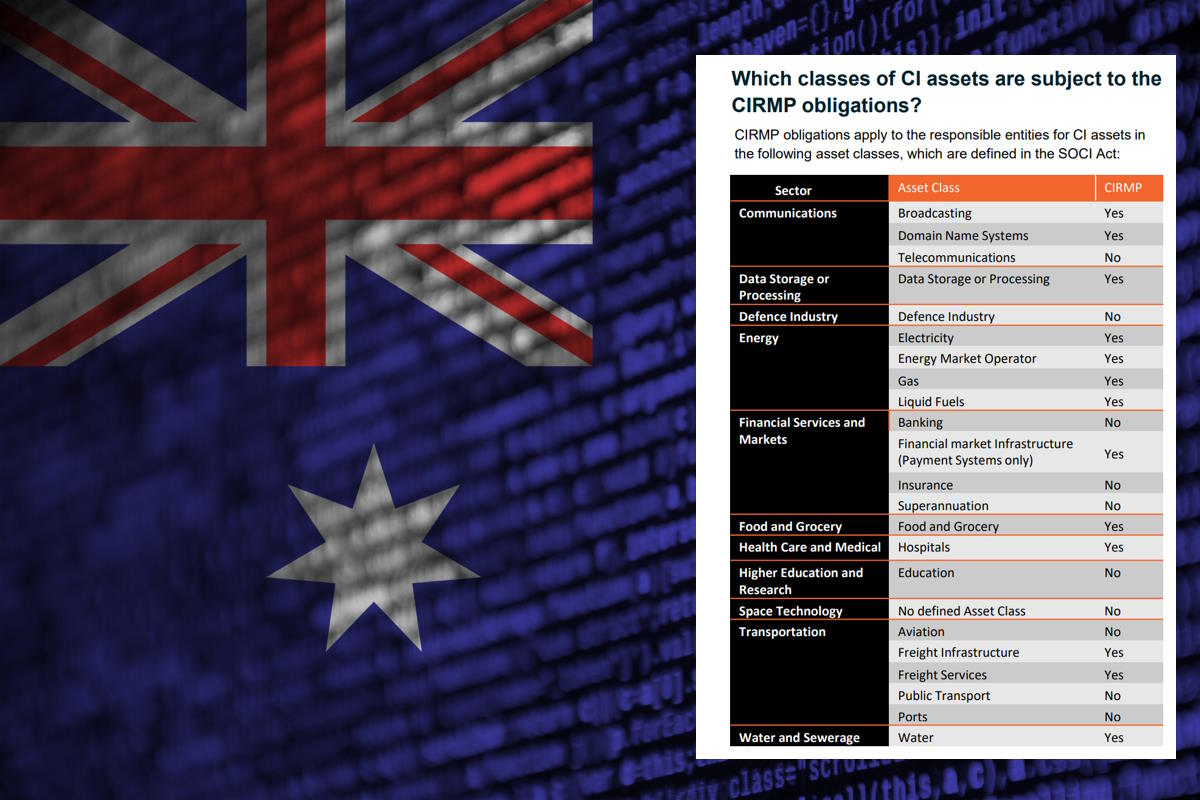
The CIRMP obligations will apply to a critical broadcasting asset; critical domain name system; critical data storage or processing asset; critical electricity asset; critical energy market operator asset; critical gas asset; designated hospital; critical food and grocery asset; critical freight infrastructure asset; critical freight services asset; critical liquid fuel asset; critical financial market infrastructure asset mentioned in paragraph 12D(1)(i) of the Act; and critical water asset.
An entity’s CIRMP must identify each hazard where there is a material risk that the occurrence of that hazard could have a relevant impact on the asset. As far as, it is reasonably practicable to do so, minimize or eliminate any material risk of such a hazard occurring. Additionally, as far as it is reasonably practicable to do so, mitigate the relevant impact of such a hazard on the asset, and comply with any other requirements set out in the rules.
Disruptions to critical infrastructure can have serious implications for businesses, governments, and the community, affecting the security of resources, supply and service continuity, and damaging economic growth. Putting in place a robust risk management program will help organizations continue to provide essential services, and recover more quickly from incidents that impact the critical infrastructure asset, while also protecting business reputation and financial viability.
CIRMPs are intended to uplift core security practices that relate to the management of critical infrastructure assets. They ensure responsible entities take a holistic and proactive approach toward identifying, preventing and mitigating material risks from all hazards. Responsible entities are best placed to develop a risk process that suits their assets, noting many organizations have existing risk management practices in place.
To develop CIRMP and comply with the rules, organizations must Identify hazards applicable and material risks to their critical infrastructure asset. For each material risk, be sure to consider the impact on your assets if the risk was to eventuate. Also, organizations must implement mitigations or eliminate material risks as far as is reasonably practicable, understand the requirements of the rules, and identify activities required to comply with the rules to mitigate material risks from all hazards, and specified hazards prescribed in the rules.
There is no prescribed format for a CIRMP, nor are the rules intended to supplant existing risk management processes. Rather, responsible entities are encouraged to incorporate existing risk management frameworks and processes into the CIRMP.
The Fact Sheet also covered that organizations must submit an Annual Report approved by the entity’s board, council, or other governing body, in the approved form, to the relevant regulator within 90 days of the end of the relevant Australian financial year. Also, the Centre may review a sample of CIRMPs following the grace period.
These annual reports will be used by the CISC to better understand the threat environment in each sector. This move enables the CISC to provide meaningful assistance to the industry when subject to a hazard and advise entities on ways to further enhance the security and resilience of critical infrastructure assets.
The Fact Sheet said that the report must be submitted within 90 days after the end of each Australian financial year if the entity had a CIRMP in place. “Due to the CIRMP grace period, responsible entities are not obligated to provide an annual report for the 2022-2023 Australian financial year. The first annual report required under the Rules is for the 2023-2024 Australian financial year,” it added.
As entities have 90 days after the end of the financial year to submit this annual report to the relevant regulator, the first report must be submitted between June. 30 2024 and Sept. 28, 2024, the Fact Sheet said. “For the 2022-23 Australian financial year, the CISC strongly encourages entities to submit an annual report voluntarily, as a pulse check on how you are implementing the CIRMP. This report does not need to be overly detailed and should be viewed as an opportunity to provide assurance that entities are taking steps to enhance risk management procedures,” it added.
Further guidance on annual reporting requirements and the approved form will be released over the coming months. At a minimum, a CIRMP should be reviewed once every 12 months to ensure it is current.
The Australian government announced last October that it has begun consulting on the Risk Management Program Rule under Part 2A of the Security of Critical Infrastructure Act 2018. The initiative works towards a strong and effective government-industry partnership that is central to achieving the government’s vision for critical infrastructure security and resilience.
Last month, CI-ISAC, a new Australian cybersecurity not-for-profit organization that works on a membership basis, launched to provide a framework for monitoring and preventing cyber-attacks on behalf of its members. It will serve an especially important function for organizations falling within the Australian government-legislated critical infrastructure sectors and asset classes.










