New SPARTA v1.3 framework offers significant updates covering space cyber threats
The Aerospace Corporation released last week v1.3 of its Space Attack Research and Tactic Analysis (SPARTA) framework, providing a general information page, SPARTA navigator, and SPARTA Matrix Updates. The latest version also delivers 14 new countermeasures (CMs) and includes SPARTA Countermeasure Mapper. The SPARTA matrix is the first publicly available cybersecurity threat identification and response matrix dedicated to helping spacecraft developers, owners, and operators outpace space-cyber threats.
“As SPARTA usage expands, papers/presentations/etc. will be published. To aggregate relevant information, a General Information page was created to maintain a centralized list of resources. There are already a handful of links to articles, blogs, podcasts, and presentations posted,” Brandon Bailey and Brad Roeher, wrote in a Medium post for the Aerospace Corporation. “In v1.3, a new presentation from CySat 2023 has been posted under the presentations banner. Additionally, there now is an area on the Aero TechBlog for Space Cyber for SPARTA posts. Since the v1.2 release of SPARTA, SPARTA Countermeasures has been added.”
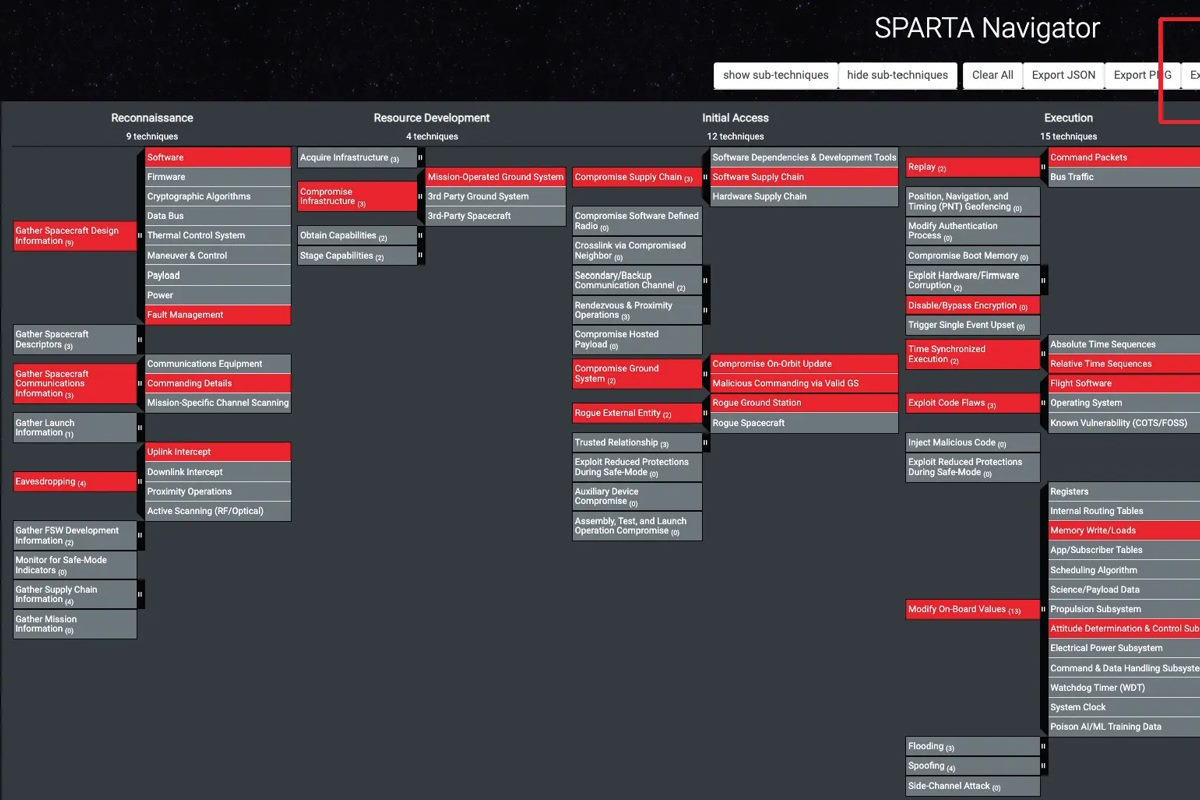
Similar to the ATT&CK Navigator, “SPARTA now offers a navigator feature, a web-based tool for creating SPARTA attack chains or highlighting TTPs. It can visualize countermeasure coverage, red/blue team planning, and more. Users can create their own layers in JSON and load them at a later time to visualize attack chains, coverage maps, etc,” the Medium post disclosed.
The most important feature of the SPARTA Navigator is the ability to export information into Excel, according to the post. “Users can select TTPs and export a custom dataset for attack chains, including countermeasure(s), associated TTPs/threats, and even NIST 800–53 rev5 control mappings.”
The SPARTA team was focused primarily on capturing as many cyber-specific TTPs as possible for the initial launch of the tool. However, cyber is not explicitly called out within the name ‘Space Attack Research & Tactic Analysis.’ It was always expected the knowledge base would expand to include TTPs related to more traditional attacks against spacecraft.
The Medium post added that with v1.3, the SPARTA team reviewed much of the publicly available literature on traditional counterspace and electronic warfare TTPs, as well as the known counterspace capabilities of various nation-states. “This is by no means a comprehensive catalog of the information but the SPARTA Team hopes it will spark additional content submissions from the community. The initial analysis culminated in 23 new techniques and sub-techniques being added to SPARTA,” it added.
Apart from these 23 techniques and sub-techniques, SPARTA v1.3 brings in 11 new cyber-specific techniques and sub-techniques, the Medium post disclosed. “In total, 44 new TTPs were added in v1.3. Certain technique titles and/or descriptions were also updated in cases where the SPARTA team felt the language could be improved.”
In addition to the semantic updates, the SPARTA team spent substantial time reviewing NIST 800–53 rev5 to ensure proper mapping of countermeasures to NIST controls. This resulted in several new mappings to countermeasures, and this work will continue to evolve as the space community attempts to translate NIST controls to the space domain.
SPARTA v13 also includes 14 countermeasures that address the broad nature of the capabilities captured in the new counterspace TTPs. The Medium post added that “no additional CMs were created to address the new cyber-specific techniques and sub-techniques. They were adequately addressed by existing CMs and the associated mappings are reflected.”
Building upon the SPARTA Navigator feature, the SPARTA team developed a Countermeasure Mapper GUI. This tool enables users to select countermeasure(s) using the defense-in-depth view and visually determine their coverage of SPARTA techniques/sub-techniques.
“This feature is particularly useful when chaining together countermeasures to build a security architecture for the spacecraft. Before selecting any countermeasures, all the techniques/sub-techniques will appear in red,” the Medium post identified. “As the user selects a countermeasure, the techniques/sub-techniques turn green indicating some level of coverage and risk reduction. It is important to understand that a single countermeasure typically cannot fully prevent a TTP but does aid in risk reduction for the spacecraft.”
When selecting countermeasures, the user can export the TTP graphic. More importantly, the user can export the data to Excel. The exported Excel workbook will report the selected countermeasures, the TTPs covered as well as the gaps in TTP coverage in respective tabs of the workbook. From a security engineering perspective, this will ensure system designers can better understand where their gaps and potential risk resides.
The initial SPARTA version 1.0 was released on Oct. 19, last year. By Oct. 28, v1.1 was released containing a few User Interface (UI) enhancements, but mostly updated reference material within many of the techniques/sub-techniques. On Dec. 8, v1.2 was released and contained several noteworthy updates.
The SPARTA matrix will enhance the likelihood of mission success by offering unclassified space-cyber threat information to the U.S. government and commercial space actors to better inform defense-in-depth engineering, threat readiness, and response. SPARTA is an additional matrix to existing ones, but it concentrates on spacecraft instead of other terrestrial technology fields as the others do.
Space system engineers/developers who build and defend the system-of-systems will ultimately have to understand multiple cybersecurity matrices and how threat actors can leverage TTPs, such as SPARTA, MITRE ATT&CK for Enterprise, ICS, Microsoft Kubernetes matrix, etc., depending on their design. Understanding the TTPs will help inform design decisions and where detection and/or countermeasures can be deployed within the system-of-system context.
The release of the SPARTA v13 comes as the U.S. Cyberspace Solarium Commission (CSC) 2.0 assessed last month that America’s adversaries recognize the importance of space systems to U.S. national security and economic prosperity and have tested capabilities to destroy them.
The CSC report recommended designating space systems as a critical infrastructure sector. It also suggests NASA as the SRMA for the space systems sector, creating two directed subgroups within the sector, not assigning the SRMA a regulatory role, articulating and offering the industry a clear value proposition, strengthening international norms and standards, and integrating the National Space Council into the governance of the space systems sector.
Last week, MITRE announced the release of its ATT&CK v13 which will provide analytics pseudocode, mobile-specific data sources, key website updates, ICS asset refactoring, and more cloud and Linux coverage. The biggest changes in ATT&CK v13 are the addition of detailed detection guidance to some Techniques in ATT&CK for Enterprise, mobile data sources, and two new types of changelogs to help identify more precisely what has changed in ATT&CK.










