Resource Center
Filter
SBOMS
Webinar
Video
Zero trust for OT
IoT/IIoT
IT/OT
Product, Solutions & Services
Market Updates
Industry Focus
Threats and vulnerabilities
Vendor
Govt & Regulations
Guides & frameworks
Clear Filters

Govt & Regulations
2023 Cyber Trends and Insights in The Marine Environment (CGCYBER)
This report summarizes U.S. Coast Guard Cyber Command’s (CGCYBER) findings from calendar year 2023 and the associated mitigation recommendations. CGCYBER continues to expand its presence and navigate an increasingly interconnected marine environment. As we witness a surge in technological advancements, the organizations that facilitate the exchange of goods face evolving cyber threats, demanding our unwavering attention and concerted action.

Guides & frameworks
APT44: Unearthing Sandworm (Mandiant)
In its third year, Russia's war in Ukraine sees Sandworm as a significant cyber threat, increasingly integrated with Russia’s conventional forces and central to the military efforts. Beyond Ukraine, Sandworm operates globally, impacting key areas for Russia. With many expected to vote in 2024's elections, Sandworm’s potential for disrupting democracy is concerning. Consequently, Mandiant has classified it as APT44 due to its continuous global threat.

Guides & frameworks
Industrial Cybersecurity Technology, Solutions & Services – Buyer’s Guide 2024
Welcome to the sixth annual edition of the Industrial Cybersecurity Technology, Solutions, and Services Buyers’ Guide. As we celebrate another year, our goal remains to clarify the complex cybersecurity landscape for industrial organizations, aiding them in enhancing their operational safety and security. Once again, this is the time for industrial cybersecurity to perform and shine. So put on your hard hats and strap in.

Guides & frameworks
H2 2023 – a brief overview of main incidents in industrial cybersecurity (Kaspersky ICS)
In this overview, we discuss cybercriminal and hacktivist attacks on industrial organizations. This overview includes information on incidents confirmed by either the affected organization or responsible government officials publicly. Compromise reports and claims made by cybercriminal groups alone are not discussed.

Threats and vulnerabilities
Connect:fun Detailing an exploitation campaign targeting FortiClient EMS
This report details an incident targeting a media company using CVE-2023-48788 and how a threat actor used it to download ScreenConnect and the Metasploit’s Powerfun script for post-exploitation activity – for our first ever named threat campaign. Due to the use of ScreenConnect and Metasploit’s Powerfun for post-exploitation, we are dubbing this campaign Connect:fun.
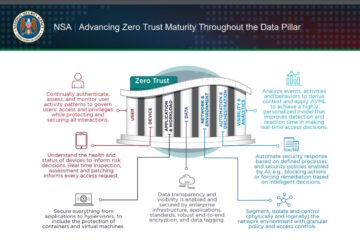
Govt & Regulations
Advancing Zero Trust Maturity Throughout the Data Pillar (NSA)
This cybersecurity information sheet (CSI) provides recommendations for maturing data security and enforcing access to data at rest and in transit, ensuring that only those with authorization can access the data. It further discusses how these capabilities integrate into a comprehensive Zero Trust (ZT) framework.

Guides & frameworks
Xage Security
State of Zero Trust in the Industrial Enterprise
The Takepoint Research report indicates a significant shift towards adopting the Zero Trust model in OT, with 72% of professionals integrating it to boost security and efficiency. It highlights secure remote access as a key application, aligning with goals to reduce risk and enhance operations. Moreover, it points out the need for collaborative efforts across organizational roles to implement Zero Trust effectively, aiming to improve productivity and security.

Review of the Summer 2023 Microsoft Exchange Online Intrusion
In mid-2023, Storm-0558, linked to China for espionage, breached Microsoft Exchange Online, affecting 22 organizations and over 500 people globally. They exploited 2016-signed tokens to access emails of key US figures like Commerce Secretary Gina Raimondo, Ambassador R. Nicholas Burns, and Congressman Don Bacon, impacting national security.

Govt & Regulations
GridEx VII Lessons Learned Report (NERC & E-ISAC)
This report summarizes the recommendations and observations identified through each exercise. The recommendations are intended to help electric utilities, government partners, the E-ISAC, and other stakeholders prepare for and respond to security incidents that affect the North American electricity system.