The Industrial Supply Chain Cyber Security Conundrum

Supply chain cyber security is becoming critical as the risk of vulnerabilities threatens integrity. Supply chains of industrial vendors are growing longer, making it easier for malicious actors to implant threats that are increasingly harder to detect. While industrial companies postulate that the products they procure from vendors are secure and safe for their use, it is possible for cyber threats to have entered from an unanticipated direction completely unbeknownst to the organization.
According to security experts, threats to the supply chain exist throughout the life cycle of products and services, from the gathering of source materials and development of components, including hardware, software, data, and algorithms, to the modifications and upgrades that are done by and for customers. In some instances, these threats could mean that OT systems can be compromised or even held to ransom.
If equipment is compromised in the supply process and users are not able to detect the threats in time, then the vendors and the industrial companies both must face the consequences. Cyber threats that go undetected could later cause huge issues for the industrial organization and all vendors who had used the systems where the threats were present.
Threats can then go on to disrupt the customers production networks or even the network of others who use that finished product. Unfortunately, cyber threats can sneak in at any point along the supply chain and can make its way into the finished product without being detected.
Security experts have said that increasing operational length of the ICT/OT life cycle could pose innumerable additional challenges to sustaining the integrity of the supply chain. The cyber security of any organization within a supply chain is potentially only as strong as that of the weakest member of the same chain. A determined aggressor will make use of this by identifying the organization with the weakest cyber security within the supply chain, and using these vulnerabilities present in their systems to gain access to other members of the supply chain. Whilst not always the case, it is often the smaller organizations within a supply chain who, due to more limited resources, have the weakest cyber security arrangements.
[optin-monster-shortcode id=”dv4jqlr9fih8giagcylw”]
Supply chain cyber security refers to efforts to enhance cyber security within the supply chain. It is a subset of supply chain security and is focused on the management of cyber security requirements for information technology systems, software and networks, which are driven by threats such as cyber-terrorism, malware, data theft and APTs. This is usually done by using best practices and industry compliant methods.
Some typical supply chain cyber security activities for minimizing risks include buying only from trusted vendors, disconnecting critical machines from outside networks, and educating end users on cyber threats and protective measures they can take.
There are many ways cyber threats can disrupt companies, similarly there are also ways cyber threats can sneak into places where they are not expected. Some of the common ways cyber threats have arrived through the supply chain are from networks or computer hardware that comes pre-installed with malware. Similarly, malware can be inserted into both hardware and software at vendor’s plants and other locations by various means. Other ways could be by discovering vulnerabilities in software apps and network systems within the supply chain by hackers. This could be possible if some of the vendors involved in that particular supply chain are at vulnerable locations. There have also been instances of malware or other threats being installed in counterfeit computer hardware which companies have received.
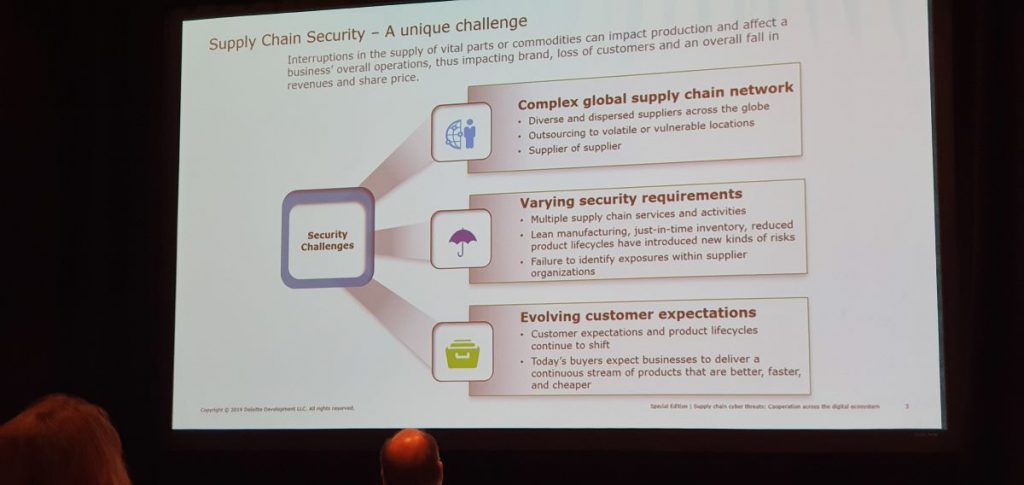
Since industrial companies are now dealing with multiple supply chain services and activities due to their leaner manufacturing and reduced life of products, they don’t get the required time to inspect inventory for cyber threats.
According to experts, building a connected high-quality final product can include many stages like the initial ones including design and procurement then manufacturing and shipping and the final stages like installation and service or customer service. This means that several vendors and suppliers will be involved in the supply chain from the conceptualization to the actual delivery of the product.
Security experts have said that threat actors can introduce compromised components into a system, unintentionally or by design, at any point of a system’s life cycle. Some common entry points from the supply chain could include malware, ransomware, viruses and watering holes.
To deal with supply chain cyber security threats, it is important to know the regulatory mandated requirements and industry-developed recommendations. It is essential to be aware of both since they may not be the same, according to Rob Garry, VP – Product Cyber, Chief Engineer – Power, GE and Steve Batson, Senior Manager, Cyber Risk, Deloitte & Touche .
In a presentation at the 2019 ICS Cyber Security Conference, they also spoke about how it is important to align expectations with stakeholders and know customers well. “Vendors should understand their customers’ regulatory environment,” they said.
Having a framework to achieve security by design and controls to define access and limits could also help keep cyber threats at bay. Similarly, threat intelligence and monitoring to isolate potential risks while having open vendor-customer communication, transparency, and collaboration could make it possible to keep track of potential scenarios.
These, in addition to mechanisms that will help adapt to change and proactively engaging with customers directly or through industry forums will help facilitate the transition and enable companies to collaborate with industry on the direction it takes. Since recent advanced and unexpected threats to supply chains have exposed new cyber-terrorism, malware, and data theft. Organizations, their suppliers, and regulators are taking many steps to counter these threats.
Companies are taking initiatives to identify, minimize, and mitigate supply chain cyber risks while also incorporating good practices from leading industries with advanced cyber supply chain risk management programs.
Industrial companies need a systematic way to approach supply chain security. Transparency and open communications between all vendors, suppliers and customer is essential. Complexity and the need to follow the supply chain could be critical for OT security.
The U.S. National Institute of Standards and Technology has said cybersecurity in the supply chain cannot be viewed as an IT problem only. Cyber supply chain risks touch sourcing, vendor management, supply chain continuity and quality, transportation security and many other functions across the enterprise and require a coordinated effort to address successfully.
It is also important for organizations to develop defenses based on the principle that their systems will be breached. Some of the best practices in the sphere should be implemented to ensure protection of all networks and hardware and not just the most vulnerable devices. For example, security requirements should be included in every proposal and contract and after a vendor is accepted in the formal supply chain, a security team should work with them on-site to address any vulnerabilities and security gaps.
The U.S. National Institute of Standards and Technology has said that having a “One strike and you’re out” policy with respect to vendor products that are either counterfeit or do not match specification should be the norm. Similarly, device and network component purchases must be tightly controlled and component purchases from approved vendors must be prequalified. Parts purchased from other vendors should be unpacked, inspected, and x-rayed before being accepted.
They also recommend that Secure Software Lifecycle Development Programs and training for all engineers in the life cycle of the supply chain are established and source code is obtained for all purchased software.
Similarly, by reducing human intervention in the supply chain systems it could be possible to keep threats at bay to an extent. For example, in many organizations, secure booting processes look for authentication codes and the system will not boot if codes are not recognized. Automation of manufacturing and testing regimes reduces the risk of human intervention reducing the ways in which threats could develop.










