Fortinet
Founded - 2000; HQ - Sunnyvale, CA
Company
Products
Services
Fortinet continues to be a driving force in the evolution of cybersecurity and the convergence of networking and security. Fortinet provides protection across IT and OT networks against advanced threats and the expanding attack surface.
FortiGate, FortiSwitch, FortiAP, FortiManager, and FortiAnalyzer

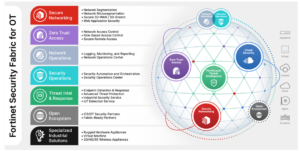
The Fortinet Security Fabric protects the digital attack surface of IT and OT networks. Deploying the Security Fabric is a journey to a desired state that provides visibility, integration, automation, resilience, and future proofing of the security environment. The Security Fabric can be deployed in stages that are aligned with organizational security priorities. It is important to consider incorporating these recommended best practices for OT security:
- Full network mapping and connectivity analysis. Understanding the physical and digital locations of all devices mapped within a network should be a primary concern of OT managers. For example, if a PLC is communicating with a different PLC due to an error or an intrusion, it is crucial for the manager to be able to discover this issue, as well as implement a mitigation strategy as soon as possible. This can only be accomplished if the connections of all assets are accurately mapped.
- Implementing a zero-trust framework. A zero-trust framework is built on the principle of “never trust, always verify.” Within this kind of system, every person, device, application, and network is presumed to be a threat. Therefore, each of these entities has the responsibility of proving its legitimacy before it is allowed to connect.
- Aligning the right remote access tools. Ensuring that the right people and systems have access to the operational technology is essential, especially because they may be pivotal to the flow of business. An OT system is often different from an IT system because it usually does not have a full selection of tools that can be granularly configured to enable remote access.