Deep Defense

During a discussion on Prabh Nair’s Coffee with Prabh channel, I introduced the concept of Deep Defense, which explores the importance of implementing multiple layers of protection in manufacturing processes. In my upcoming book, I will delve further into this topic, examining the various layers of protection and discussing areas for improvement. While cyber security is crucial, it is not infallible given the evolving threat landscape. The concept of Deep Defense emphasizes the need to go beyond cyber security and consider additional protection mechanisms that can protect us when our cyber defenses fail. What are these additional protection layers?

Taking a risk-based approach, I distinguish three key risk domains that form the scope of Deep Defense:
- OT Technical Risk: This refers to the risk associated with the automated functions of the manufacturing installation. It results from the potential failures or malfunctions of the OT systems and equipment. These can be intentional failures like in the case of a cyber attack, or accidental failures.
- Cyber-Physical Risk: This risk stems from the failure of automation functions, which can be categorized as either Loss of Ability to Perform (similar to loss of availability) or Loss of Performance (affecting system integrity). Both types of failures can significantly impact the physical production process and its behavior.
- Socio-Technical Risk: This risk arises from regulatory, organizational, and human factors within the manufacturing environment. The effectiveness of protection measures is influenced by regulatory requirements, organizational structure, and the handling of human errors. Flaws in the organizational processes and human errors can manifest throughout the entire life cycle of the system, including the FEED, design, construction, commissioning, support, and procurement processes.
By taking a holistic approach to the protection of manufacturing installations and addressing risk factors in each of these domains, we can establish a robust and comprehensive defense strategy for safeguarding manufacturing processes, which I refer to as Deep Defense.
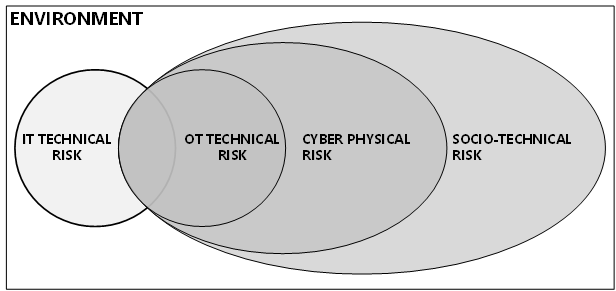
The above figure actually shows a 4th risk domain, the IT technical risk domain. It is an important risk domain to include because the organization typically sees these two domains as separate disciplines. If we look at these risk domains from a functional hierarchical perspective as described by ISA-95 we get the following diagram.
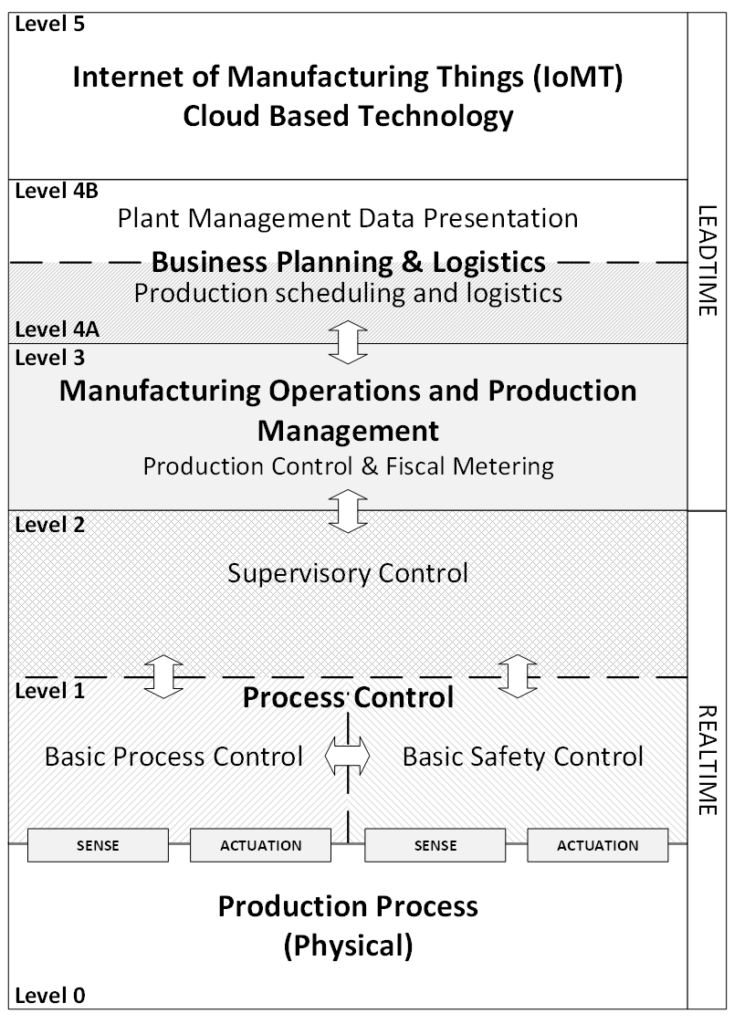
Here we see both Level 4A and Level 4B. Level 4A comprises functions that either provide data to the process automation functions or depend on data from the process automation functions. Flaws in the integrity of this exchanged data can have severe consequences for all functions in the overall installation independent of their level. So, the attack surface for a manufacturing installation is not limited to what we often call an Industrial Control System (ICS), there are more points of vulnerability in the installation or application that can be exploited by an attacker. For me, the attack surface represents all the potential avenues through which an attacker can gain unauthorized access, manipulate data, or disrupt manufacturing operations. While intentional failures can be one way in which an attacker can exploit vulnerabilities, for a holistic approach the attack surface should encompass all potential vulnerabilities, regardless of the cause of failure.
Throughout my 4+ decades of process automation and my 2+ decades of cyber security for these installations, I have observed that there are numerous low-hanging fruits we can harvest by analyzing all design, organizational, and operational processes of the installation and correcting these.
The reason for this is that when we discuss the protection of our manufacturing installations against cyber attacks we focus too much, in many cases prioritizing network security. However, the design of our process applications, the installation itself, and the organizational structure involving all stakeholders are equally vital for establishing a resilient and robust defense. This is why I introduce and advocate for the concept of Deep Defense.










