Following critical authentication bypass breach in Fortinet products, Cyble finds hackers selling access over the darkweb
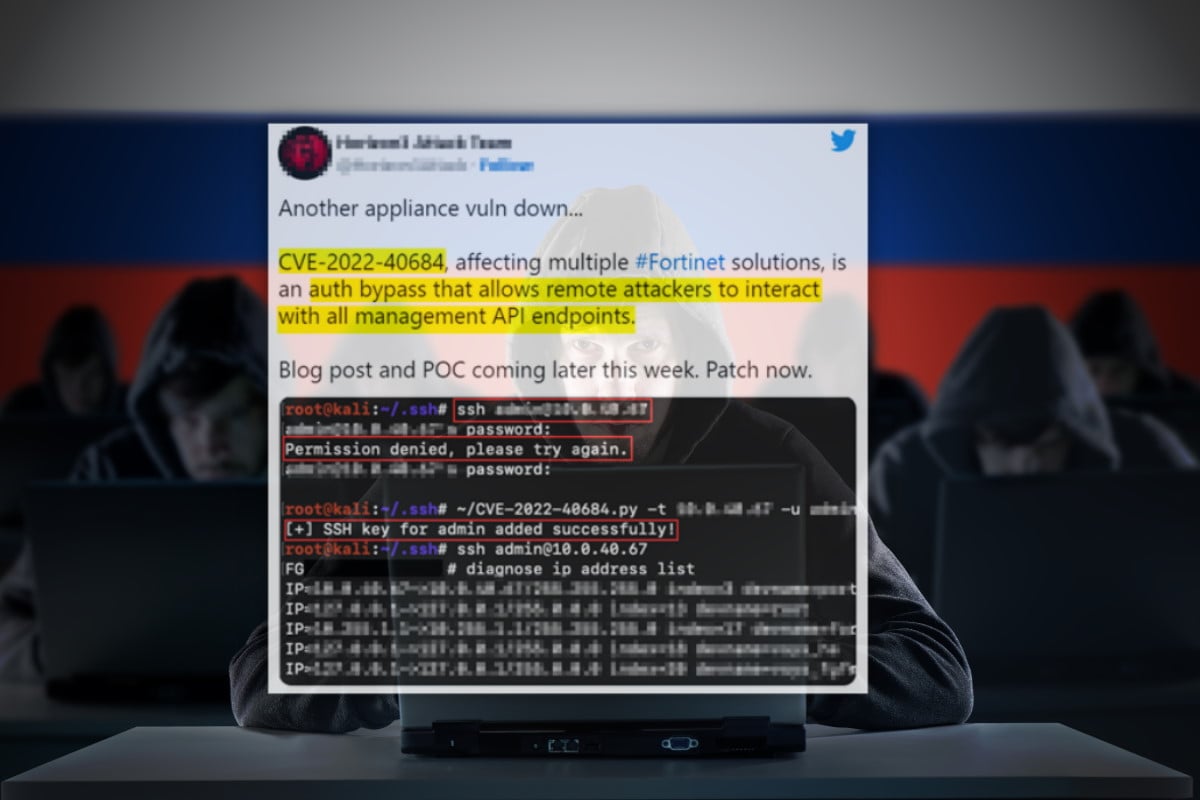
Cyble researchers said that multiple versions of Fortinet products have been affected by an authentication bypass using an alternate path or channel vulnerability in FortiOS, FortiProxy, and FortiSwitchManager. While during routine monitoring, researchers at Cyble observed a hacker distributing multiple unauthorized Fortinet VPN access over one of the Russian cybercrime forums.
“While analyzing the access, it was found that the attacker was attempting to add their own public key to the admin user’s account,” the researchers wrote in a blog post on Thursday. “As per intelligence gathered from sources, the victim organizations were using outdated FortiOS. Hence, with high confidence, we conclude that the Threat Actor behind this sale exploited CVE-2022-40684.”
Tracked as CVE-2022-40684, the security vulnerability allows for an authentication bypass that uses an alternate path or channel in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0. The loophole allows an unauthenticated attacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
The Cyble researchers disclosed that while targeting affected versions of Fortinet products, “an attacker takes advantage of a controlling mechanism in a function responsible for evaluating the affected devices’ access to the REST API functionality. While exploiting this vulnerability, the attacker adds an SSH key to the admin user, enabling access to SSH into the affected system as admin,” the post added.
An attacker can update or add a valid public SSH key to a targeted account on a system and can then typically gain complete access to that system. Additionally, the hacker could launch other attacks against the rest of the IT environment with the foothold and knowledge gained through exploiting this vulnerability.
“One of the online scanners shows that there are over 100 thousand FortiGate firewalls exposed over the internet that are likely under the scope of attackers and are vulnerable to CVE-2022-40684 if not patched yet,” the Cyble researchers added.
A malicious attacker might utilize the vulnerability to compromise a system further by modifying the admin users’ SSH keys to enable the attacker to log in to the compromised system, adding new local users, and update networking configurations to reroute traffic. They can also download the system configuration, initiate packet captures to capture other sensitive system information, while sensitive system information, system configurations, and network details might be further distributed over the darkweb.
The researchers said that the distribution of initial access has played a vital role in some of the recent major ransomware attacks across the globe. “Cybercriminals have been improving their tactics and acquiring sophisticated cybercrime tools and techniques to remain ahead of the LEA and cybersecurity community. Cyble has observed Initial Access Brokers (IABs) playing a notorious role in the organized cybercrime ecosystem,” they added.
Cybercriminals, including ransomware groups, have created this convenient arrangement to monetize their efforts, thereby reducing their risks and adding further layers of anonymity. IABs are a significant threat to enterprises, and monitoring such threats to avert business, financial and reputational loss is imperative.
Publicly distributed proof of concepts (POCs) and automation tools have made it more convenient for attackers to target victim organizations within a few days of the announcement of the new CVE, the researchers said. “If security teams within the organization do not implement the patches and workarounds released by an official vendor, the risk of a successful cyber-attack increases exponentially.”
Hackers are actively distributing access and leaks over the darkweb and cybercrime forums by exploiting the known, and new vulnerabilities, the initial access distributed over the darkweb has been key behind some of the major attacks recently, the researchers added. Darkweb and cybercrime forum monitoring can be considered critical pillars within an organization’s security posture.
The post suggests that organizations update affected products with the latest patch released by the official vendor, implement proper network segmentation to prevent attackers from performing lateral movement and minimize exposure of critical assets over the internet, and keep critical assets behind properly configured and updated firewalls.
Additionally, organizations must continuously monitor, and logging can help in detecting network anomalies early, and implement proper access controls within the IT environment, with regular audits, vulnerability, and pentesting exercises emerging are key in finding security loopholes that attackers may exploit. Further, enterprises must implement secure backup, archiving, and recovery processes within the organization, apart from carrying out cybersecurity awareness training programs for employees within the organization.
In August, researchers at the Cyble Global Sensor Intelligence team detected an increase in attempts to exploit VNC (virtual network computing). The data comes as about 9,000 exposed VNCs can be accessed and used without authentication, sometimes with authentication disabled, providing hackers with easy access to internal networks across critical infrastructure installations.










