Researchers detail Dead Man’s PLC approach that works towards viable cyber extortion for OT cybersecurity
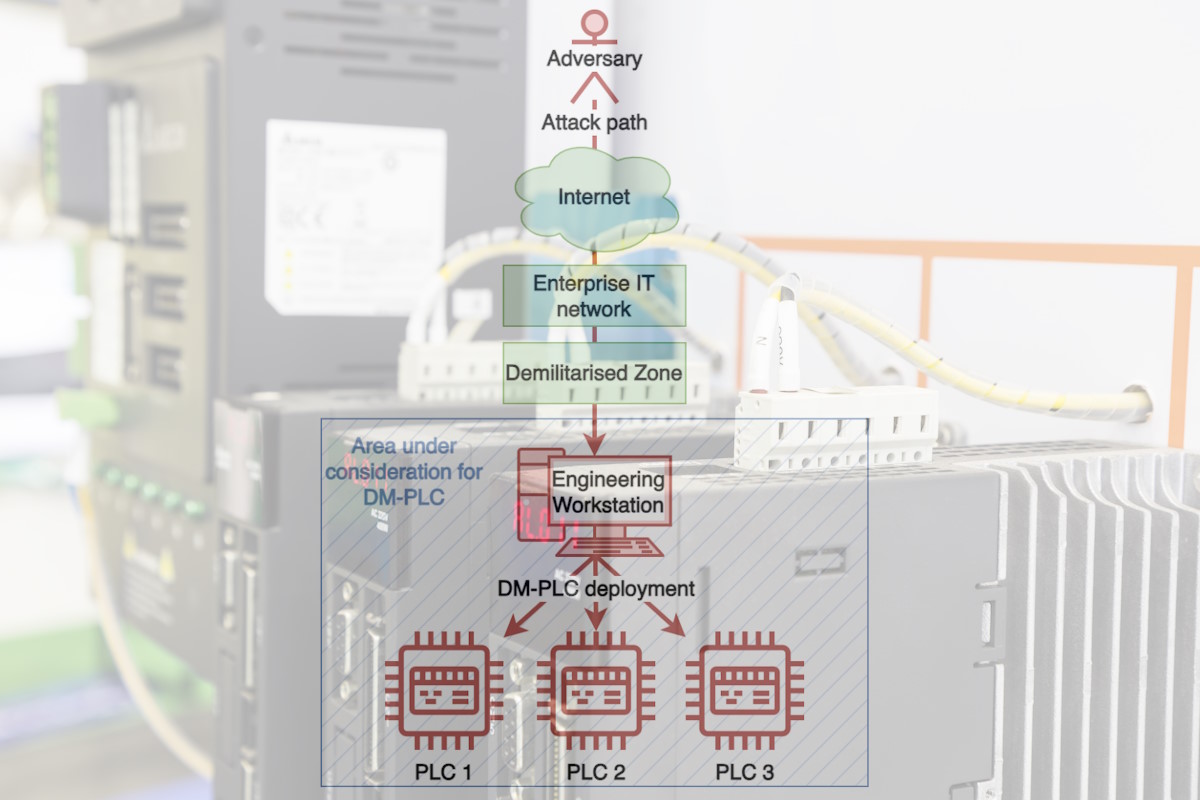
New research has identified that as the demographics of cyber adversaries shift, there is likely to be a corresponding shift in attack goals. These goals are expected to change from clandestine process degradation and espionage to overt cyber extortion (Cy-X). The consensus from OT cybersecurity practitioners suggests that even if encryption-based Cy-X techniques were launched against OT (operational technology) assets, typical recovery practices designed for engineering processes would provide adequate resilience. In response, the research paper introduces Dead Man’s PLC (DM-PLC), a pragmatic step towards viable OT Cy-X that acknowledges and weaponizes the resilience processes typically encountered.
“Using only existing functionality, DM-PLC considers an entire environment as the entity under ransom, whereby all assets constantly poll one another to ensure the attack remains untampered, treating any deviations as a detonation trigger akin to a Dead Man’s switch,” Richard Derbyshire, Benjamin Green, Charl van der Walt, and David Hutchison, wrote in their research paper, published last week on Cornell University’s curated research-sharing platform arXiv. “A proof of concept of DM-PLC is implemented and evaluated on an academically peer-reviewed and industry validated OT testbed to demonstrate its malicious efficacy.”
The DM-PLC is a pragmatic first-step approach towards a viable Cy-X technique that directly targets OT devices while circumventing the resilience of existing response and recovery tactics. DM-PLC utilizes existing functionality within an OT environment to simultaneously create a covert monitoring network of programmable logic controllers (PLCs) and engineering workstations (EWs) that constantly poll one another, monitor for any deviations from the attack’s behavior, and deny configuration access to the victim.
“Should the victim make an attempt to alter the environment under adversary control or not pay their ransom in time, DM-PLC will activate a trigger akin to a Dead Man’s switch, causing all PLCs to set their outputs to an ‘ON’ state, resulting in chaos within the victim’s physical environment,” according to the researchers. “DM-PLC brings OT-targeted attacks in line with the modus operandi of the emerging demographic of adversaries in the area, i.e., cybercriminals, and reflects the shift from encryption-based Cy-X techniques to more creative ways to conduct ransom attacks. In doing so, this work highlights the fact that an adversary does not require significant investment, experience, or sophisticated root-level access to PLCs to conduct such an OT-targeted cyber attack.”
Rather, DM-PLC demonstrates that an adversary may hold an entire OT environment to ransom by simply using existing communications and security features against the victim.
The work outlines a proposal for a technique to perform a Cy-X attack on OT devices, utilizing only existing functionality, and circumventing resilience encountered in current best practices. A practical implementation of DM-PLC is demonstrated as a proof of concept on two PLCs and an EW. DM-PLC is then scaled up and evaluated on an academically peer-reviewed and industry-validated testbed, identifying its strengths and limitations. Mitigation techniques are proposed for OT asset owners to protect themselves against such attacks in the future.
The DM-PLC is focused on the existing intercommunication between OT assets, predominantly EWs and PLCs. However, it could be extended to additional OT assets such as remote terminal units (RTUs) and human machine interfaces (HMIs) should the adversary choose.
The researchers identified that from a technical perspective, EWs are generally Windows-based devices complete with the typical vulnerabilities encountered in enterprise IT assets. The key aspect of an EW is that it is enhanced with industrial configuration software, which allows it to communicate via industrial protocols and configure embedded OT devices such as PLCs that can have a variety of architectures. These devices typically have minimal operating systems, such as modified versions of Linux or even bespoke implementations, that are inaccessible to both the operators and potential adversaries.
“However, at the level which is accessible to the operator, there is a wealth of functionality available such as ICMP, SNMP servers, and HTTPS servers,” according to the researchers. “PLCs are programmed by the industrial configuration software on an EW, using the industrial protocols that are enabled by the software. The program, pushed to the PLC by the EW, controls what the PLC does and how it senses and controls the physical process. It can be written in a variety of languages such as ladder logic and can be entirely bespoke; however, default library functions provided by the PLC vendor are commonly used.”
The researchers also detailed the DM-PLC attack scenario where modern adversaries do not appear to be encountering challenges when navigating to the OT environments of their victims, and no value or novelty can be derived from describing that process. Therefore, this paper does not concern itself with initial access or lateral movement prior to deploying DM-PLC. It is instead assumed that the adversary has completed these tactics and is already in position.
The physical and logical layout of an OT environment can vary significantly between organizations, and this variation can be further exacerbated between sectors, the research revealed.
Taking existing work as both inspiration and lessons to be learned, DM-PLC seeks to further develop the existing notion of OT Cy-X through the employment of legitimate, vendor-provided PLC functionality. The key feature of DM-PLC is circumventing the current resilience of best practice response and recovery, such that removing affected PLCs is not an option without consequence for the victim. This also means that DM-PLC must not negatively impact the operational process unless it is tampered with or its ransom timer has expired; immediately experiencing negative consequences may dissuade the victim from paying in lieu of replacing the affected devices.
The target set of high-level DM-PLC requirements is deployable with minimal prerequisites from an EW; runs in parallel to existing operational code; does not impact existing operational code; and is resilient to tampering/response and recovery processes. The research also includes tamper detection; can enact undesirable wide-spread operational impact; requires a key to relinquish control back to system owners; and can be tested prior to being armed.
In conclusion, the research identified that DM-PLC creates a covert monitoring network of PLCs and EWs that constantly poll one another, and should any asset under adversary control deviate from the attack or the payment timeout window expire, an alert will be triggered akin to a Dead Man’s switch, which will propagate throughout the covert monitoring network and turn all outputs to an ‘ON’ state. This is achieved by using only existing legitimate functionality, demonstrating that adversaries do not need to develop complex exploits against OT, therefore significantly reducing the potential cost of an OT cyber attack.
“The approach presented in this paper should clearly serve as a warning to OT owners and operators that such an attack is feasible and needs special attention to defend against it,” the researchers added. “Finally, further work in the area should focus on OT being secure by design such that existing functionality cannot be weaponised, rather than perpetuating existing practices of relying on re-appropriated IT security concepts.”










