New GRIT data continues to observe ransomware group exploitation of viable vulnerabilities
The GuidePoint Research and Intelligence Team (GRIT) Ransomware Report disclosed that November closed with an increase in posted ransomware victims relative to a quieter October, but in keeping with an overall higher rate of victims consistent since March. While total observed victims increased 29 percent month-over-month from 336 to 433, November’s victims exceeded the calendar year 2023 average by 16 percent and the rolling average since March this year by 6 percent, indicating a relatively consistent pace of operations since the second quarter.
Data revealed an outsized impact on Chinese organizations in November, with nearly a quarter of 2023’s ransomware attacks against China taking place this month, Jason Baker wrote in a Thursday blog post. “November’s ransomware attacks in China impacted victims in the energy, automotive, legal, and pharmaceutical industries, a departure from the most frequently impacted manufacturing industry, further complicating this potential anomaly,” he added.
The various groups conducting November’s attacks on China-based organizations may indicate exploration by ransomware groups into targets that have historically escaped largely unscathed by ransomware despite containing lucrative potential victims. China has historically aligned itself with the Eastern European nations where many ransomware actors are thought to reside, but shifting geopolitical relations between those Eastern European countries could open the door to additional future operations.
“GRIT continues to observe ransomware group exploitation of viable vulnerabilities, as demonstrated by the widespread exploitation of the Citrix Bleed vulnerability and Clop’s return to scaled exploitation with SysAid,” according to Baker. “As organizations continue to increase the resilience of their security against ransomware, exploitation of vulnerabilities, particularly in VPNs and storage services, will likely remain a high priority for ransomware groups.”
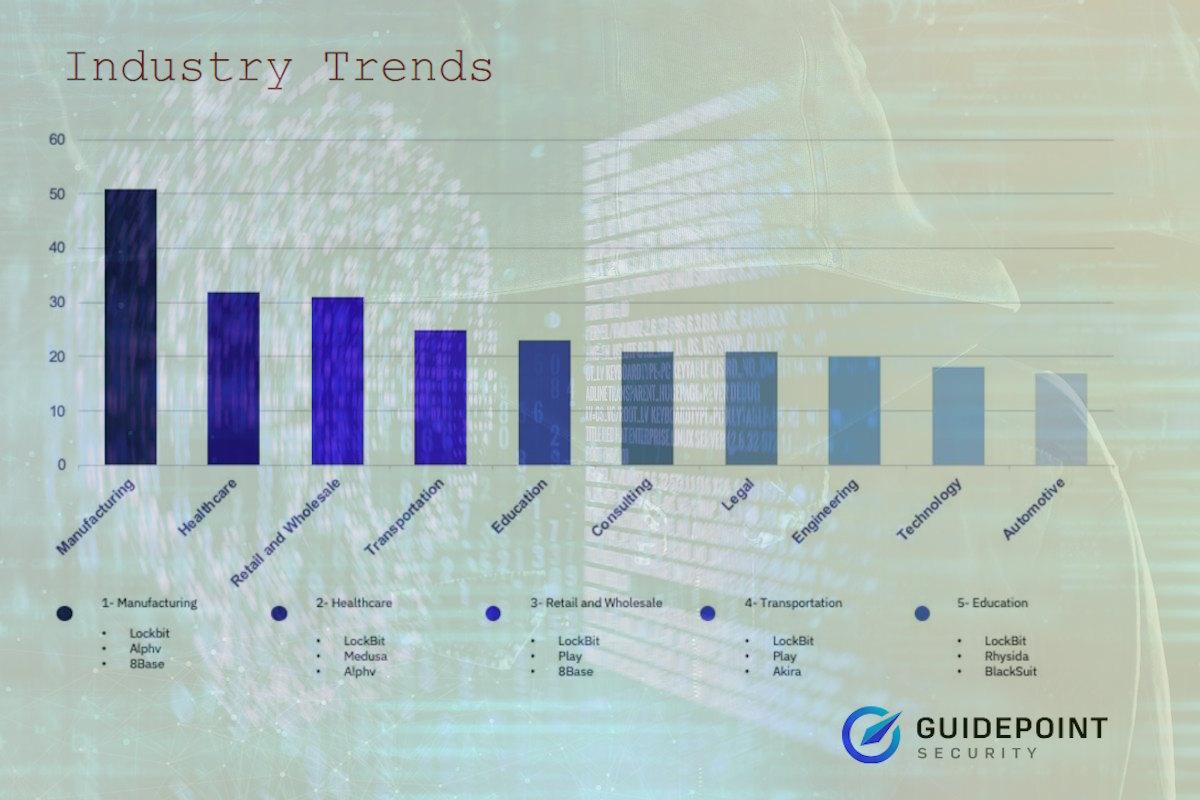
The team also observed a marginal decrease in the number of observed active ransomware groups, though this was influenced by the arrival and drop-off of several smaller emerging groups. The most prolific established ransomware groups, including LockBit, Alphv, and Play continue to account for the highest percentage of observed ransomware victims, and 82 percent of observed victims were attributed to ransomware groups that have operated for at least six months.
The geographic focus of ransomware remains primarily on the global north, with U.S.-based organizations as the primary victims followed by Western countries in Europe, Canada, and Australia, the team observed. “Impacted organizations in China typically belong to the manufacturing industry, whereas November resulted instead in multiple victims from the energy, automotive, legal, and pharmaceutical industries, further complicating this anomaly.
Data also revealed that Eastern Europe-based cybercrime actors, which make up much of the ransomware landscape, have traditionally appeared averse to targeting Chinese targets. “We will remain alert to continued spikes, which could indicate a shift to this approach,” it added.
While manufacturing remains the most impacted industry in the U.S., impact against healthcare organizations continues to increase, continuing a concerning trend of disregard for human life and disregard or softening of longstanding affiliate rules in some cases. The largest and most impactful of these attacks are often attributed to ransomware’s most prolific established actors, possibly reflecting an operational focus on this sector to extract high ransoms.
The U.S. continues to remain the most frequently impacted country by ransomware attacks. The share of observed attacks impacting US-based organizations remained consistent with the 2023 calendar year average of 49 percent, at 48 percent (207) of November’s victims.
The Netherlands has made the ‘Top Ten list’ of victims for the second time this year. November’s victims account for 21 percent (11) of the Netherland’s total victim count for 2023 (52). BlackBasta accounted for four of these victims, while the other six were each claimed by six other groups. Also, Canada experienced a decrease in victim volume and victim share relative to baseline, typically ranking in the three most impacted countries behind the U.S. and the U.K., but fell to sixth in November.
Baker identified that manufacturing retained its long-standing position as the most impacted industry in November, with a marginal increase from 49 to 51 observed victims, but decreasing in proportionate share from 14.58 percent to 11.78 percent. “While manufacturing more than doubled the number of victims from ‘runner-up’ industries in October, November brought a tighter concentration of highly impacted industries, with healthcare and the retail and wholesale industries each accounting for approximately 7% of observed victims as the second and third most impacted industries,” he added.
The data disclosed that November marks the third-most impactful month of the year for Healthcare, with 32 claimed victims, a 33 percent increase from its monthly industry average of 24; “this increase is consistent with our observation of greater impacts on the healthcare industry over at least the past 3 months. Finally, for the first time in 2023, the Automotive industry was observed as one of the most impacted industries, with the industry accounting for 17 victims, more than twice its monthly industry average of 8,” it added.
Another interesting data that the GRIT team identified was that November closed as LockBit’s most active month since August, retaining its dominance in the ransomware ecosystem with over 25 percent of observed victim posts. LockBit continues to impact healthcare organizations, with two-thirds of its impacted healthcare organizations in 2023 being victimized in November.
“Following a dip in posted victims in October, Alphv returns to the ‘Top Three’ with 46 victims, a 30% increase over its average of 35 monthly victims,” Baker added. “Like LockBit before it, Alphv continues to impact healthcare organizations and release attention-seeking media statements, likely in an attempt to shame its victims and discourage non-compliance from future targets.”
Play continues its upward trend of victim volume with 44 victims, nearly doubling its average daily rate for the second month in a row. Play has disproportionately impacted the retail and wholesale sectors, matched only by LockBit.
In his conclusion, Baker said that the increased impacts on Chinese industries will remain a point of collection for GRIT going forward, particularly given the potential profitability of Chinese victims and dependent on the law enforcement response received. “While November holds the potential to present as an anomalous month in terms of Chinese organizational victims, it could also mark the opening of a new market segment for financially motivated cybercrime.”
As the year comes to a close, the GRIT team anticipates a continuation or increase in operations and opportunities to exploit undiscovered vulnerabilities or defensive teams with staff out on holiday leave. “GRIT observed this behavior in a surge of observed victims in December 2023, and the cybersecurity community is well-tuned to the frequency of ‘holiday drops’ in the form of last-minute vulnerabilities. GRIT will continue to monitor for increases in ransomware activity and wishes our fellow defenders a peaceful and uneventful holiday season,” they added.










