GuidePoint latest data reveals alarming trends across industries, as ransomware activities surge
Researchers at GuidePoint Research and Intelligence Team (GRIT) published its latest quarterly ransomware analysis report highlighting a nearly 15 percent increase in ransomware activity since the second quarter. The researchers partly attributed this to the rise in the number of groups operating in the ransomware space, as there is a direct correlation to the number of public victims of ransomware. Additionally, the rise comes due to an increased number of ransomware groups, including 10 new emerging groups tracked during the third quarter, the largest number of new groups observed in a single quarter across GRIT’s data set.
“Q3 of 2023 marked the largest volume of public ransomware victims that GRIT has observed since we began tracking the ransomware ecosystem for the last 2 plus years,” Drew Schmitt, practice lead at GRIT, said in a Thursday media statement. “The ransomware ecosystem, as a whole, is on pace to nearly double its number of publicly posted victims year over year despite a lesser increase in the number of threat actors. This suggests that many of the groups we are tracking are continuing to increase their operational tempo, but also may be the result of many organizations not being willing to pay the ransom demand.”
During the third quarter, GRIT tracked 1,353 publicly posted ransomware victims claimed by 46 different threat groups. Through the first three quarters of 2023, GRIT has tracked a total of 3,385 publicly posted ransomware victims claimed by 57 different threat groups, representing an 83 percent year-on-year increase. The report is based on data obtained from publicly available resources, including threat groups themselves, and insight into the ransomware threat landscape.
Other notable third-quarter events include Clop’s MOVEit campaign, LockBit’s return to a high operational tempo, and Bianlian’s sustained capabilities despite moving to an exfiltration-only model, which have contributed to this quarter’s rise in ransomware activity.
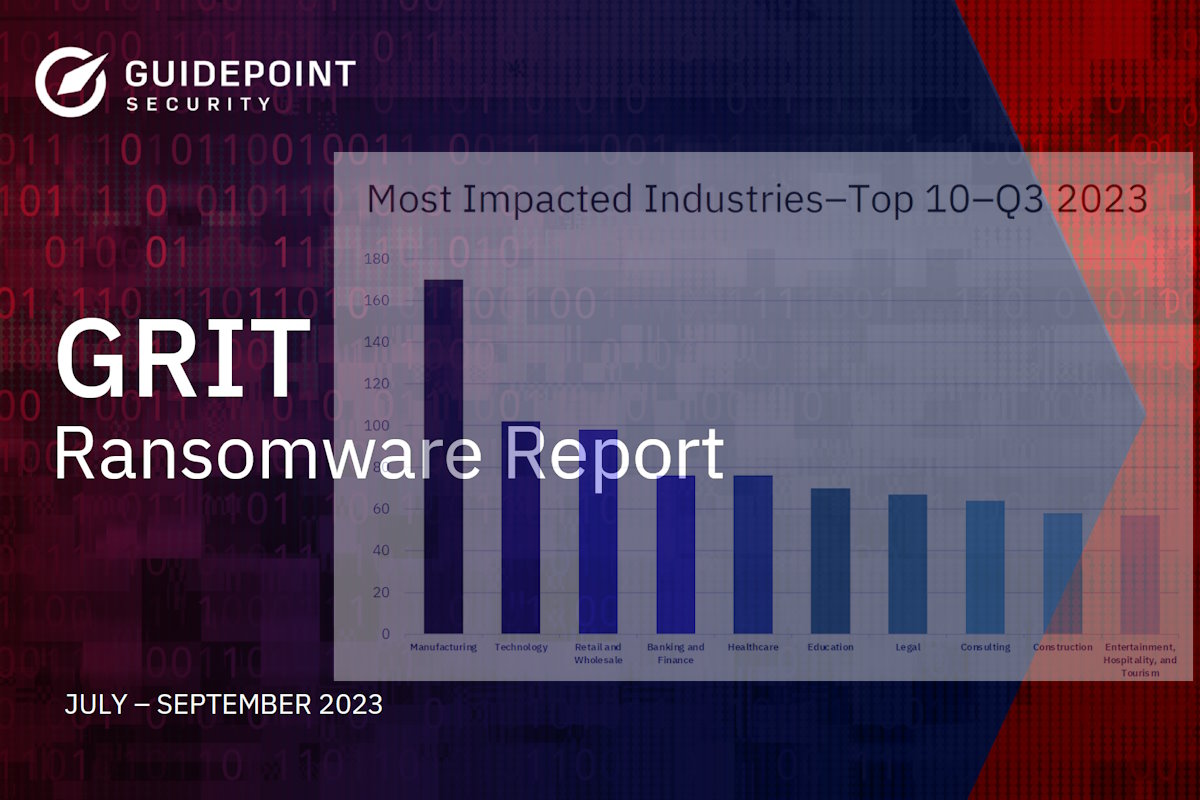
The manufacturing and technology industries were the first and second most impacted by ransomware, followed by retail and wholesale as the third most impacted. The retail and wholesale vertical has experienced a steady quarterly climb in observed victims throughout the year, jumping from ninth place with 38 victims in the first quarter, to its current spot in the top three with 98 victims.
The large-scale ransomware attacks against MGM Resorts and Caesars Entertainment highlight possible seasonal targeting of the Entertainment, Hospitality, and Tourism (EHT) industry, according to GuidePoint. “Based on our research, the EHT industry was the fifth most impacted industry, it’s highest position since GRIT began tracking ransomware activity. GRIT assesses that the increases in impacted organizations from this industry are a result of deliberate targeting, owing to increased seasonal holiday travel and the victims representing attractive financial targets.”
Other notable industry trends include continued attacks on the healthcare industry, as groups like Alphv continue to claim healthcare victims at a significant rate. In Q3, one out of every five victim posts to Alphv’s leak site were healthcare organizations, suggesting that all Ransomware as a Service (RaaS) groups are concerned with the potential law enforcement attention that healthcare victims could bring.
Furthermore, established groups continue to maintain the highest market share and victim volume in the ransomware ecosystem, and long-time leader LockBit continues to operate without significant challengers, even amongst other Established groups, the report said. “We note that some Emerging and Developing groups continue to claim high rates of victims that would rival the performance of Established groups such as Alphv and Bianlian.”
Data revealed that the U.S. still accounts for 48 percent of publicly posted ransomware victims but saw a 3.3 percent reduction in total U.S. victims from the second to the third quarter. “Meanwhile, GRIT observed other consistently impacted countries have an increase in activity including the United Kingdom, which saw a 40% increase in their total number of public victims. Additionally, there was an almost 3% rise in “non-top ten” countries impacted by ransomware in Q3, highlighting a potential new trend in group’s impacting historically less targeted countries,” it added.
Revealing an evident expansion of ransomware’s reach beyond the typically affected Western nations, the data illustrates a notable surge in victim counts across ‘non-top 10’ countries. Despite their exclusion from the current analysis, these countries witnessed a marked rise from contributing 24.1 percent of the second quarter total to 26.8 percent in the third quarter, signifying an increase of 79 victims.
GuidePoint research evaluates that the ransomware ecosystem as a whole is on pace to nearly double its number of publicly posted victims year over year despite a much less significant increase in the number of actors, suggesting increased victim volume attributed to the most established and operationally mature groups.
“The increase in reported victims can be partially attributed to the large scale of Clop’s mass exploitation campaigns, but the data also echoes sentiments from around the industry that fewer companies are willing to pay a ransom, potentially contributing to increased victim posts on ransomware group blogs,” the report identified. “Another recurring trend is the positive correlation between the number of active groups and the number of victims posted at any given time. While seemingly obvious, this indicates that newer Emerging groups are able to find their own victims without reducing the victim volume of Established groups.”
It added that LockBit maintains its hold on the number one spot, posting 770 victims this year to date. “Comparatively, LockBit was responsible for 670 victims in the first three quarters of 2022, showing that the largest Ransomware-as-a-Service operation continues to increase its victim volume. Through its successful mass exploitation attacks, Clop has surged to the number two spot. At this point in 2022, the group had only 38 posted victims, highlighting the significance of Clop’s shift to mass exploitation tactics.”
Despite not operating publicly until Q2, new groups Akira and 8Base rose to long-term spots on the top 10 list with operations that have rapidly scaled, GuidePoint reported. “Royal remains on the top 10 list despite having not posted since July 19th, a testament to its impact in the first half of the year. All indications suggest that the once Established group is no longer operational, possibly as the result of splintering or intentional rebranding.”
Looking forward to the fourth quarter, GRIT assesses that there will be continued upward trends in data-only exfiltration by groups that have been impacted by the release of public decryptors, or groups without the resources to develop and maintain their own encryption capabilities. “Standalone ransomware groups, including Bianlian, may choose to continue this trend as part of their long-term operations, while Ransomware-as-a-Service groups such as Akira may pursue data-only exfiltration as a stop-gap while developing new encryptors or pursuing Rebrands,” it added.
As current emerging and developing groups continue to hone their skills and refine their processes, GRIT assesses that the number of publicly posted ransomware victims is likely to increase through the fourth quarter, resulting in significant annual growth in ransomware victims from 2022 to 2023 and setting up 2023 to be ransomware’s most impactful year to date.
“Ransomware groups continue to find methods of adapting to a changing ecosystem, whether through Emerging and Developing groups adapting unique niches in the ransomware community, as observed with Ransomed; or through Established groups, including Alphv, consistently impacting sensitive industries and newsworthy victims,” the report identified. “GRIT stands firm in our belief that community and law enforcement intelligence sharing remains key to identifying and limiting the effectiveness of ransomware groups. As 2023 begins to come to a close, GRIT is continuing to monitor the ransomware landscape and sharing relevant trends, TTPs, and IOCs to identify and slow ransomware activity.”










