Microsoft reveals increase in Iranian cyberattacks and influence operations following Hamas attack on Israel
Following the October 2023 attack by Hamas on Israel, Microsoft disclosed that there has been a noticeable increase in cyberattacks and influence operations carried out by Iranian government-aligned actors. The objective of these activities is to support Hamas and undermine Israel, as well as its political allies and business partners. While some of Iran’s initial operations were disorganized and rushed, suggesting a lack of coordination with Hamas, they have nonetheless experienced a growing level of success.
The research identified four findings, including a 42 percent increase in traffic, in the first week of the war, to news sites run by or affiliated to the Iranian state. Even three weeks later, this traffic was still 28 percent above pre-war levels. Despite early Iranian claims, many ‘attacks’ in the early days of the war were either ‘leaking’ old material, using pre-existing access to networks, or were false.
Additionally, Iran’s activity quickly grew from nine Microsoft-tracked groups active in Israel during the first week of the war to 14, two weeks into the war. Cyber-enabled influence operations went from roughly one operation every other month in 2021 to 11 in October 2023 alone. As the war progressed, Iranian hackers expanded their geographic scope to include attacks on Albania, Bahrain, and the U.S. They also increased their collaboration, enabling greater specialization and effectiveness.
“Contrary to some claims of Iranian state media, Iranian cyber and IO actors were reactive in the initial phase of the Israel-Hamas war,” wrote Clint Watts – General Manager, Microsoft Threat Analysis Center in a Microsoft blog. “MTAC observed Iranian state media issuing misleading details of claimed attacks and Iranian groups re-using dated material from historical operations and exaggerating the overall scope and impact of claimed cyberattacks. Three months on, the preponderance of data suggests Iranian cyber actors were reactive, quickly surging their cyber and influence operations after the Hamas attacks to counter Israel.
Microsoft’s AI for Good Lab’s Iranian Propaganda Index (IPI) monitors the proportion of traffic visiting Iranian state and state-affiliated news outlets and amplifiers compared to overall traffic on the internet. In the first week of the conflict, the post said that it observed a 42 percent increase. That surge was particularly pronounced in the U.S. and its English-speaking allies (UK, Canada, Australia, and New Zealand), which indicates Iran’s ability to reach Western audiences with its reporting on Middle East conflicts.
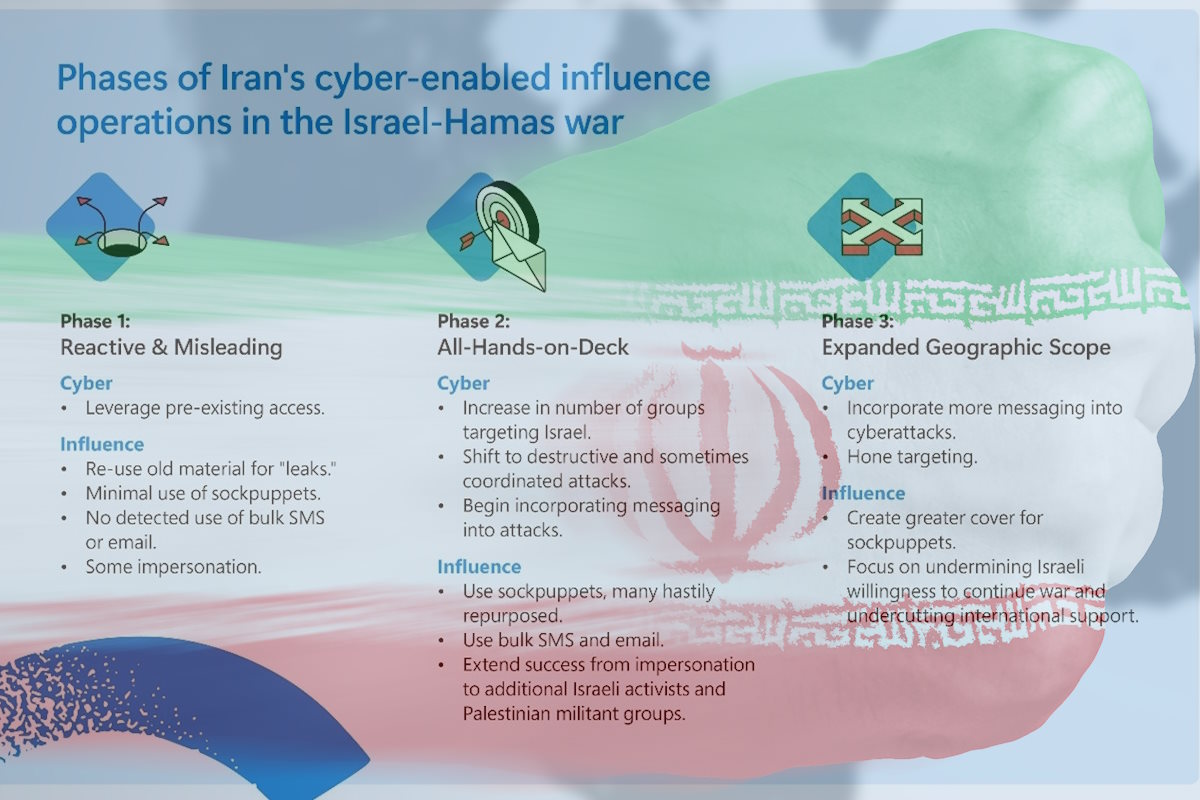
Watts detailed that Iran’s cyber-enabled operations in the Israel-Hamas war have moved through three phases since October 7.
“The first phase saw misleading claims from Iranian state media. One example was IRGC-affiliated Tasnim News Agency claiming that a group called ‘Cyber Avengers’ had conducted cyberattacks against an Israeli power plant ‘at the same time’ as the Hamas attacks,” he added. “Cyber Avengers itself (also likely run by the IRGC) claimed to have attacked an Israeli electric company the evening before the Hamas attacks. However, its evidence was only some weeks-old press reporting of power outages ‘in recent years’ and a screenshot of an undated disruption to the company’s website.”
By mid to late October, the second phase was emerging, Watts identified. “This saw the number of Microsoft-tracked groups active in Israel rise from nine in the first days to 14 by day 15. Sometimes, multiple Iranian groups were targeting the same organization or military base in Israel with cyber or influence activity. This suggests coordination, common objectives set in Tehran, or both.”
Furthermore, Watts added that the use of cyber-enabled influence operations against Israel significantly accelerated. Iran showed its preference for such attacks in 2022 when it increased the pace of such operations from roughly every other month to multiple operations a month.
“In late November 2023, Iranian groups began expanding their cyber-enabled influence beyond Israel, targeting countries Iran perceives are supporting Israel. This aligned with the Iran-backed Houthis starting their attacks on international shipping,” according to Watts. “On November 20, the MOIS-aligned cyber persona ‘Homeland Justice’ warned of forthcoming cyberattacks on Albania. They later claimed credit for attacks on a range of Albanian organizations and institutions on Christmas day.”
On November 21, Watts said that the cyber persona ‘al-Toufan’ targeted the Bahraini government and financial organizations to normalize ties with Israel. “By November 22, IRGC-affiliated groups began targeting Israeli-made programmable logic controllers (PLCs) in the United States, including taking one offline at a water authority in Pennsylvania on November 25. PLCs are industrial computers adapted for the control of manufacturing processes, such as assembly lines, machines, and robotic devices.”
Watts assessed that the progression shown so far in the three phases of war will continue. “Amid the rising potential of a widening war, we expect Iranian influence operations and cyberattacks will continue to be more targeted, more collaborative, and more destructive as the Israel-Hamas conflict drags on. Iran will continue to test redlines, as they have done with an attack on an Israeli hospital and U.S. water systems in late November.”
He also wrote that Iran’s efforts to undermine Israel and its supporters across the internet and social media, causing general confusion and a loss of trust are driven by four underlying objectives, including destabilization through polarization, retaliation, intimidation, and undermining international support for Israel.
Watts said that impersonation is not new, but Iranian threat actors are now not just masquerading as their enemies but also their friends. “Recent operations from Iranian groups have used the name and logo of Hamas’s military wing, the al-Qassam Brigades, to spread false messaging and threaten IDF personnel. It is unclear whether Iran is acting with Hamas’s consent,” he added.
He also pointed out “that the increased collaboration we have observed between different Iranian threat actors will pose greater threats in 2024 for election defenders who can no longer take solace in only tracking a few groups. Rather, a growing number of access agents, influence groups, and cyber actors makes for a more complex and intertwined threat environment.”
Commenting on the Microsoft post, Christopher Warner, senior security consultant for OT governance and risk at GuidePoint Security, told Industrial Cyber that “the conflict in the Middle East is teaching us that a reactive approach to any security is a losing battle for business today, so why are we not solving this? The resource allocations from business owners, large and small, the board of directors, and the C-suite need advisory resources to help validate what some call the New World War.”
In the early stages of the conflict, Iranian cyber and information operations (IO), Warner added that “they appeared to be more reactive than proactive. Evidence accumulated as the conflict continued over three months, indicating a shift in Iranian tactics. This shift saw a significant increase in both cyber and influence operations aimed at opposing Israel, suggesting a move from a primarily reactive posture to a more engaged and active strategy in the cyber domain, aligning their efforts more closely with the ongoing conflict dynamics.”
Earlier this month, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed sanctions on six officials from the Iranian Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC). The Iranian government organization has been involved in carrying out malicious cyber activities targeting critical infrastructure in the U.S. and other countries. The U.S. has taken this action in response to recent cyber operations conducted by IRGC-affiliated cyber actors.










