VulnCheck detects remote command injection vulnerability in Contec SolarView series, affecting ICS hardware
Following a June Palo Alto Networks Unit 42’s blog that discusses the Mirai botnet variant, utilizing new CVEs for propagation and highlighting the latest IoT exploits, new details have emerged from VulnCheck about three vulnerabilities affecting a command injection vulnerability in the Contec SolarView series. With the new information, experts predict that hundreds of solar power monitoring systems are vulnerable to these critical remote code execution (RCE) vulnerabilities, with hackers and amateurs potentially exploiting the situation.
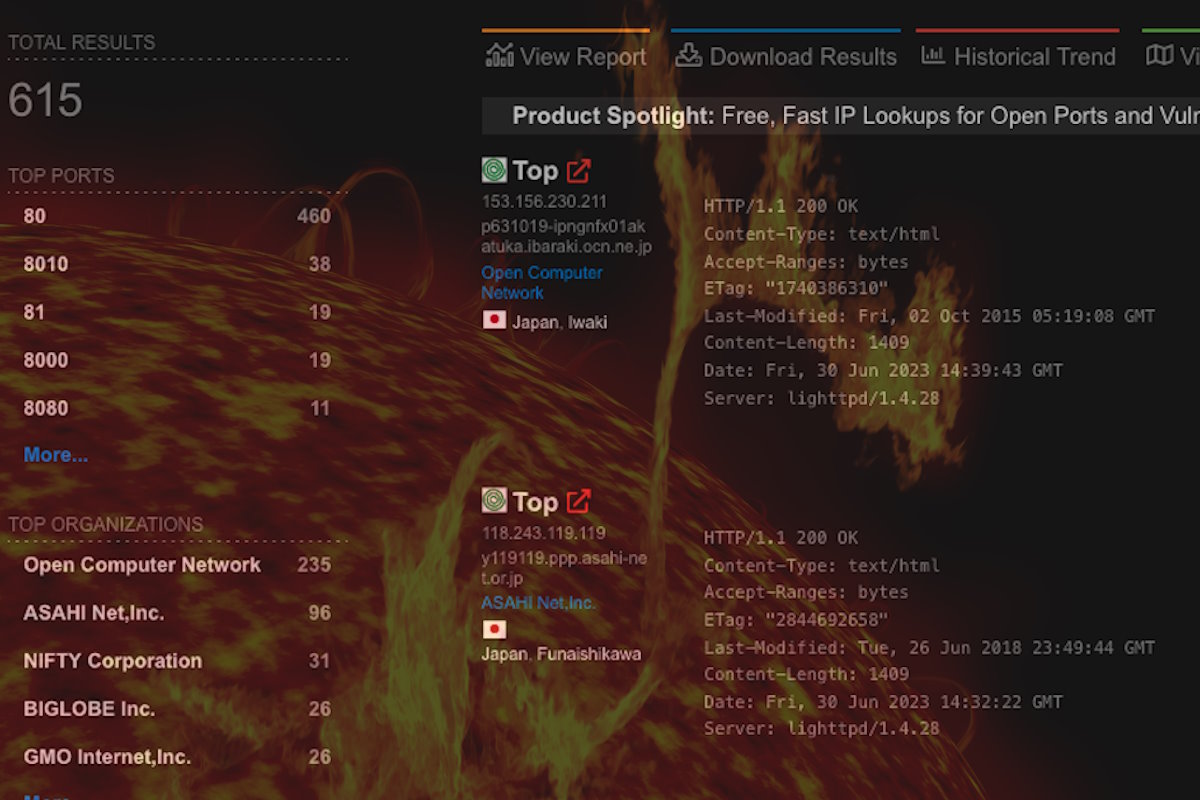
“CVE-2022-29303 is an unauthenticated and remote command injection vulnerability affecting the Contec SolarView Series. Since VulnCheck Exploit Intelligence has indexed a number of public exploits for SolarView, we decided to dig in and examine the potential scale and impact of this exploitation in the wild,” Jacob Baines, vulnerability researcher at VulnCheck, wrote in a company blog post this week.
Baines highlights the potential impact of Contec SolarView, which monitors and visualizes small to medium-scale solar power generation and storage. It highlights deployment scenarios for SolarView Air and Battery in commercial buildings and solar power plants. Contec SolarView is intended for ICS (industrial control systems) networks, so ‘you’d hope to never find one accessible over the internet.’ Furthermore, Shodan currently indexes more than 600 SolarView systems.
According to the CVE description of the CVE-2022-29303 vulnerability, the affected versions of SolarView are ‘ver.6.00,’ which was released in 2019, and SolarView Compact has seen four firmware releases since then (6.20 in 2019, 7.00 in 2021, 8.00 in 2022, and 8.10 in 2023). That suggests that only a small subset of internet-facing hosts are likely to be vulnerable.
However, Baines outlines that further examination of SolarView’s firmware revealed that this CVE description is inaccurate.
“CVE-2022-29303 affects the web server’s ‘conf_mail[dot]php’ endpoint, but version 6.20 (the version following the reportedly vulnerable 6.00) didn’t implement a fix for the issue. Not only was version 6.00 affected, but 6.20 as well. In fact, we found that the very straightforward command injection in ‘conf_mail[dot]php’ has existed since at least version 4.00,” according to Baines. “It wasn’t until version 8.00 that conf_mail[dot]php was added to the auth[dot]require list, and validation is added to the attacker-controlled $mail_address variable.”
Baines says that it suffices to say that “the range of affected systems is much wider than the CVE description lets on, and thanks to a copyright string on the landing page (and the sparse amount of releases over the years), we can easily fingerprint the affected internet-facing systems.”
He also added that it turns out that less than one-third of the internet-facing SolarView series systems are patched against CVE-2022-29303.
Baines also flagged that while CVE-2022-29303 garnered attention from some organizations like Unit 42 and GreyNoise, there are a couple of other unauthenticated RCEs affecting the systems that have not.
He also pointed out that for example, CVE-2023-23333 affects the SolarView series up to version 8.00 (despite the fact that the CVE description says ‘through 6.0’). “This vulnerability doesn’t have any Exploit-DB entries, but it has multiple exploits on GitHub. CVE-2023-23333 is a simple command injection affecting the downloader[dot]php endpoint, specifically the mishandling of user data in the zip case.”
Baines also wrote that the SolarView Series is also affected by CVE-2022-44354, a file upload vulnerability that allows an attacker to upload a PHP webshell to the system. “The CVE description says ‘Compact 4.0 and 5.0’ are affected, but there’s a duplicate CVE (CVE-2022-31374) that says Compact 6.0 is affected. Either way, we see no changes to /Solar_Image[dot]php (the affected component) until version 7.0,” he added.
Finally, he wrote that it’s worth noting that these issues are not isolated to the SolarView ‘Compact’ hardware version. The ‘Air is also affected (the code is nearly identical) and, likely, the ‘Battery hardware version is affected as well.
‘We’ve looked at a few critical CVEs that affect the SolarView series and determined that there are a few hundred internet-facing systems that remain affected by these issues. When considered in isolation, exploitation of this system is not significant,” according to Baines. “The SolarView series are all monitoring systems, so loss of view is likely the worst-case scenario. However, the impact of exploitation could be high impact depending on the network the SolarView hardware is integrated into.”
For instance, Baines added that if the hardware is part of a solar power generation site, then the attacker may affect the loss of productivity and revenue by using the hardware as a network pivot to attack other ICS resources.
“The fact that a number of these systems are internet-facing and that the public exploits have been available long enough to get rolled into a Mirai-variant is not a good situation,” Baines added. “As always, organizations should be mindful of which systems appear in their public IP space and track public exploits for systems that they rely on.”
On Thursday, U.S. and Canadian cybersecurity agencies warned of cyber hackers leveraging newly identified Truebot malware variants against organizations in the two countries. Truebot is a botnet that has been used by malicious cyber groups, like the CL0P ransomware gang, to collect and exfiltrate information from its target victims.










