Resource Center
Filter
AI
SBOMS
Webinar
Video
Zero trust for OT
IoT/IIoT
IT/OT
Product, Solutions & Services
Market Updates
Industry Focus
Threats and vulnerabilities
Vendor
Govt & Regulations
Guides & frameworks
Clear Filters

AI
MITIGATING AI RISK- Safety and Security Guidelines for Critical Infrastructure Owners and
The guidelines specifically address risks to safety and security, which are uniquely consequential to critical infrastructure. NIST defines “safety” as a property of a system such that it does not, under defined conditions, lead to a state in which human life, health, property, or the environment is endangered; safety involves reducing both the probability of expected harms and the possibility of unexpected harms. Because AI risks to critical infrastructure are highly contextual, critical infrastructure owners and operators who use AI-systems should account for their specific circumstances as they use these guidelines.

Govt & Regulations
AI for Energy – Opportunities for a Modern Grid and Clean Energy Economy (DoE)
This report was prepared pursuant to the Executive Order (E.O.) on the Safe, Secure, and Trustworthy Development and Use of AI (14110), issued October 30, 2023. Priority use cases have been identified in four broad areas where AI can be immediately deployed to improve the grid while achieving the Administration’s goals for reducing emissions and providing affordable and reliable electricity to all Americans: grid planning, permitting and siting, operations and reliability, and resilience.

Govt & Regulations
2023 Cyber Trends and Insights in The Marine Environment (CGCYBER)
This report summarizes U.S. Coast Guard Cyber Command’s (CGCYBER) findings from calendar year 2023 and the associated mitigation recommendations. CGCYBER continues to expand its presence and navigate an increasingly interconnected marine environment. As we witness a surge in technological advancements, the organizations that facilitate the exchange of goods face evolving cyber threats, demanding our unwavering attention and concerted action.

Guides & frameworks
APT44: Unearthing Sandworm (Mandiant)
In its third year, Russia's war in Ukraine sees Sandworm as a significant cyber threat, increasingly integrated with Russia’s conventional forces and central to the military efforts. Beyond Ukraine, Sandworm operates globally, impacting key areas for Russia. With many expected to vote in 2024's elections, Sandworm’s potential for disrupting democracy is concerning. Consequently, Mandiant has classified it as APT44 due to its continuous global threat.

Guides & frameworks
Industrial Cybersecurity Technology, Solutions & Services – Buyer’s Guide 2024
Welcome to the sixth annual edition of the Industrial Cybersecurity Technology, Solutions, and Services Buyers’ Guide. As we celebrate another year, our goal remains to clarify the complex cybersecurity landscape for industrial organizations, aiding them in enhancing their operational safety and security. Once again, this is the time for industrial cybersecurity to perform and shine. So put on your hard hats and strap in.

Guides & frameworks
H2 2023 – a brief overview of main incidents in industrial cybersecurity (Kaspersky ICS)
In this overview, we discuss cybercriminal and hacktivist attacks on industrial organizations. This overview includes information on incidents confirmed by either the affected organization or responsible government officials publicly. Compromise reports and claims made by cybercriminal groups alone are not discussed.
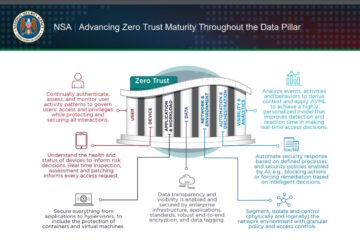
Govt & Regulations
Advancing Zero Trust Maturity Throughout the Data Pillar (NSA)
This cybersecurity information sheet (CSI) provides recommendations for maturing data security and enforcing access to data at rest and in transit, ensuring that only those with authorization can access the data. It further discusses how these capabilities integrate into a comprehensive Zero Trust (ZT) framework.

Guides & frameworks
Xage Security
State of Zero Trust in the Industrial Enterprise
The Takepoint Research report indicates a significant shift towards adopting the Zero Trust model in OT, with 72% of professionals integrating it to boost security and efficiency. It highlights secure remote access as a key application, aligning with goals to reduce risk and enhance operations. Moreover, it points out the need for collaborative efforts across organizational roles to implement Zero Trust effectively, aiming to improve productivity and security.

Govt & Regulations
GridEx VII Lessons Learned Report (NERC & E-ISAC)
This report summarizes the recommendations and observations identified through each exercise. The recommendations are intended to help electric utilities, government partners, the E-ISAC, and other stakeholders prepare for and respond to security incidents that affect the North American electricity system.
