Industrial enterprises must tread the cybersecurity curve cautiously but with a sense of urgency as the threat landscape widens

The last few months have been extraordinarily challenging for anyone who protects industrial enterprises. So, it seems like it was not too long ago that we published the latest version of our Industrial Cybersecurity Technology, Solutions and Services Guide 2022.
The guide, originally designed to answer the initial questions we get from all sides, has grown enormously in bulk, stature, and the work involved.
While we conducted more than 62 interviews across vendors, integrators, and enterprise end-users in the lead-up to this guide, I’ll admit there is always more we miss – not on purpose, primarily due to resource limitations. Thankfully, many vendors will take the time to let us know if we overlooked them 😊.
Here’s how we see the market landscape as of the time of publication of this guide, earlier in the year. This market landscape categorizes industrial cyber solutions, trying to provide as much high-level information as possible on one page.
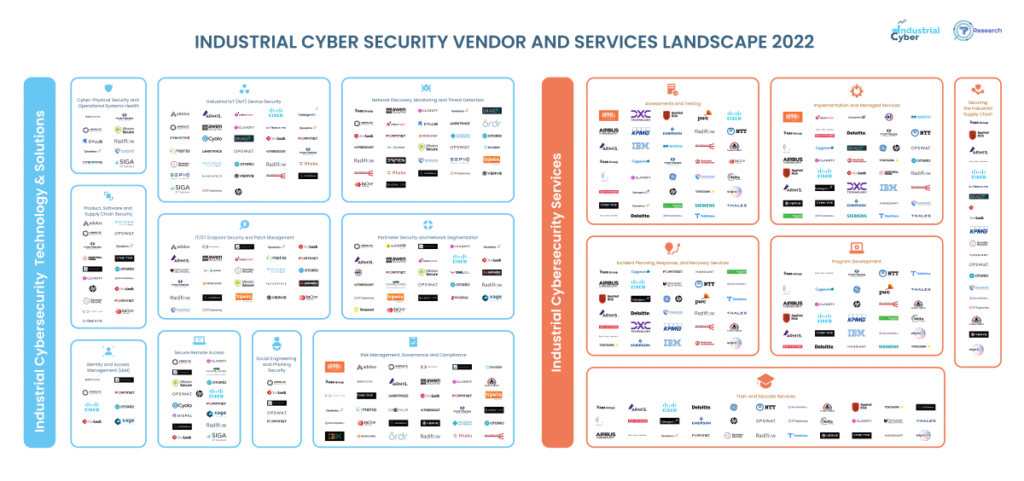
Unprecedented change
The last 12 to 24 months have been tumultuous, to say the least.
The COVID-19 pandemic proved to be a game changer for many. Not all, but most industrial enterprises were woefully underprepared. If you recall the early days of the pandemic, we saw images of engineering and operations teams that were literally sequestered on site, in plants and factories – a situation that had a very limited shelf life.
The immediate need for many was figuring out how to remotely connect everyone who needed access to these networks and devices.
Unfortunately, the need to react quickly often led to security holes being opened rather than closed. I think it’s safe to say that many of us are still dealing with those issues.
The COVID-19 pandemic led to operational changes within industrial enterprises, as hastily constructed short-term workarounds have morphed into the long-term status quo for many businesses. Apart from other factors, the pandemic impacted organizational approach to cybersecurity and risk appetite.

Some of the changes precipitated by the pandemic are positive and needed. Others are not so much. While initially slowing down initiatives, the pandemic response created a catalyst that reinvigorated security projects. Ultimately, cybersecurity needs and solutions will shake out in the marketplace.
A war in Europe, the invasion of Ukraine has significantly increased the level of concern and activity about protecting critical and other infrastructure from cyber threats. If anything, it has demonstrated how intertwined the world economies are and how susceptible global supply chains are to both physical and cyber threats. On a personal note, I will take this opportunity to state that the senseless and brutal invasion of Ukraine has been utterly devastating for all. My thoughts are constantly with colleagues and friends suffering from the war and those living under occupation.
The last 12-24 months have been relentless on the cyber front – there has been no lack of high-profile attacks on everything from water, gas pipelines, and transportation.
Colonial, Oldsmar, JBS, Molson Coors, NHS, Greek pipeline company DESFA, UK public transport company Go-Ahead – the victims’ list across key verticals just keeps growing.
Details regarding last month’s alleged breach of water systems at the U.K. water supply company by the Russian-based Cl0p ransomware hacker group are still emerging – and from what we have seen so far, it’s not pretty.
If anything is clear at this point in time, asset owners and operators are facing immediate danger.
More than meets the eye
For anyone following the market, vulnerabilities seem to be uncovered and reported daily. Unfortunately, in our corner of the industry, malicious actors don’t have to bother with zero-day attacks. Adversaries and nation-state hackers have a host of vulnerabilities to exploit at their disposal. We are making it too easy for our adversaries. Many of these successful attacks have been due to the lack of basic cyber hygiene.
Global supply chains also face relentless threats from nation-state and criminal hackers seeking to steal sensitive information and intellectual property, compromise the integrity of government systems, and conduct other acts that adversely impact a nation’s ability to provide services safely and reliably to the public.
While this is a rather bleak picture, there are some positives – in particular, the conversation around industrial cybersecurity has increased greatly. Moreover, there is a reaction from all corners, with the industry, government, and industry bodies, working towards building and bolstering organizational cybersecurity posture.
Legislators and regulators rolling up their sleeves
Governments around the world are starting to move. For example, the U.S. presidential order has caused a flurry of activity, though not all of it well directed. Still, nevertheless, it helped highlight cybersecurity concerns plaguing the sector and bring about the necessary interest thereof. The TSA directive is one such instance.
Singapore has recently updated and republished its Cybersecurity Code of Practice for Critical Information Infrastructure which came into effect in June.
The Australian government passed the Security Legislation Amendment (Critical Infrastructure Protection) Bill 2022 to boost the security and resilience of the nation’s critical infrastructure framework to safeguard the essential services that Australian citizens rely on from physical, supply chain, cyber, and personnel threats.
Likewise, the U.S. CISA is developing regulations following the Cyber Incident Reporting for Critical Infrastructure Act, which was signed into law by U.S. President Joe Biden in March.
The EU NIS2 directive and many more government and industry-specific regulations and frameworks abound – IEC 62443 standards, the NIST 800-82 guidance, the MITRE ATT&CK framework, and the list goes on. Information sharing is starting to happen but is still limited to using various channels, including MITRE, DoE, CISA’s ICS-CERT, JCDC, etc.
Now, while I don’t believe we can regulate our way out of this challenge, the sheer amount of discussion, debate, and focus are very welcome – the increased interest is even begging to drive some action.
Keeping the momentum
At some times, it might seem that things don’t change. At other times, change might take time. I often say that the industrial cybersecurity challenge is more about people and processes – culture than technology. So, just a reminder (particularly for vendors new to the space) that OT and IT professionals have different – and sometimes opposing – worldviews.

Engineers are concerned with the safe operation and the continued production – keeping the light on, gas flowing services going while using any solution, product, and approach that makes this a priority.
Another issue is that OT networks cannot be simply halted for patching, reconfiguration, or re-architected – vendors designing solutions to enhance the security of these environments must take this into account before stepping onto the production floor.
Concerns, Obligations, and Crossing the Chasm
With all that we have covered so far, it is clear that the industrial cybersecurity paradigm is changing. As a result, industrial enterprises, the executives that run them, and the shareholders and their board representatives are facing an incredibly complex challenge.

Several factors have caused the shift in board-level interest and involvement. For instance, the growing number of cybersecurity attacks and incidents making headlines, regulators who increasingly hold companies accountable for addressing gaps in their cybersecurity resilience, and the increase in cybersecurity and technology investment.
As cybersecurity breaches may have a significant impact, company directors are feeling the heat, with many of them personally liable for the consequences. As a result, the ground is literally shifting under their feet.
At the same time, it seems insurance companies are beating a retreat. Last month, the Lloyd’s of London announced it will require underwriters to exclude coverage for state-backed cyberattacks linked to war from 2023 across all insurer groups. While the insurance firm stated that it ‘remains strongly supportive of the writing of cyberattack cover,’ it recognizes that ‘cyber-related business continues to be an evolving risk.’
Evidently, the losses brought about by these ‘catastrophic’ state-backed attacks can potentially exceed what the insurance market can absorb. Moreover, with rising ransomware attacks and subsequent payouts, insurers are forced to find ways to limit their risk or go out of business.
Given that the industrial sector has a mere six months until the new Lloyd’s rules kick in, the backup plan of transferring risk may be off the table.
What potentially lies ahead
Cyber risk is essentially a business risk – to address and mitigate those risks, we need tools and processes to enable you to see and understand the current picture, change that picture, and affect the outcome.
Until recently, vendors have focused on providing visibility and asset inventory. While many industrial enterprises have deployed solutions, including visibility and asset inventory tools, many more have yet to do so. They are waiting for more value – they need to be able to change the outcome, proactively mitigate some of these risks, and provide transparency to the board and shareholders.
As an industry, we need to go beyond visibility and start looking at securing the industrial enterprise end-to-end. Of course, moving beyond visibility is no simple task. However, when the hard work really begins, identifying and segmenting business-critical processes, measuring risk, and even implementing basic cyber hygiene can be tough.
It seems there is nothing easy about securing the industrial enterprise. If you’re up for a challenge, you’ve found the right place; if not, best look elsewhere.










