Zero-trust approach for industrial networks

When Ruben Lobo got his start with Cisco 14 years ago, industrial organizations around the world looked a little different. That was before the 2010 Stuxnet attack made headlines as one of the largest and most successful industrial cyber-attacks in history, prompting industrial organizations to take a hard look at the security of their operations. “Cisco’s been in the industrial space now for more than a decade providing networking infrastructure in various industrial environments,” Lobo says. “What we’ve seen evolve over the years is essentially a recognition from many companies that they need to improve their security posture in these operational environments.” Lobo is Director of Product Management for Cisco’s IoT business unit. In that role, he’s responsible for managing the industrial switching and security product lines at Cisco. He’s also tasked with helping industrial organizations digitize operations and that experience has given him insight into how these organizations can best secure themselves in the face of digitization.“Digitization is happening,” Lobo says. “The question is how do you secure it. A zero-trust approach is the best way to get there.”

Ruben Lobo, Product Line Director – Cisco IoT
Lobo says a zero-trust approach is essential to protecting industrial organizations. In industrial environments today, the traditional security perimeter is eroding. Workloads are moving to the cloud. Industrial Internet of Things technology is causing previously siloed industrial control systems to be connected to the enterprise. Users, devices, and applications are everywhere. And the volume of remote users connecting to the network is increasing. These factors and more are creating a new landscape that presents unique cybersecurity challenges.
“We’ve seen for a very long time that there is a demilitarized zone that separates the operational side of the network from the enterprise side. Despite all of that being in place you see a lot of attacks,” Lobo says. “Mainly that happens for two reasons. In many cases, the DMZ is a bit porous because of changes over time and more importantly, a lot of the threats depending on the type of environment you’re in, come from inside the environment. A lot of these commercial industrial businesses are very dynamic, there are lots of people going in and out, there’s remote access, and there are people on the inside who very often bring in threats unknowingly. It’s not enough to just have a strong separation between IT and OT with a firewall or a data diode. You need to implement security measures inside these environments.”
Lobo says it’s time to look below the industrial DMZ and create trusted zones of access in the industrial network, with continual enforcement, closest to the network resource. That’s where a zero-trust approach comes in.
“You not only have to think about securing the users, but you also have to think about securing assets,” Lobo says. “That notion of zero-trust that is now being implemented in most of the enterprises is becoming more and more relevant in the industrial space.”
Zero-trust enables industry digitization by making OT asset LAN connectivity simple and secure. This approach is built around creating trusted zones of access and continual enforcement, closest to the protected resource. It’s designed to secure all users and application connections and is essential for identifying and classifying not just users, but critical endpoints, devices and applications.
By extending the workplace zero-trust approach to industrial settings, organizations can transition their network access from a “trust, then verify” approach to one with least privilege.
A Zero-trust approach for industrial networks
“The reason why the damage that is caused by these cyber incidents is so widespread is due to the fact that the networks themselves in industrial environments are very poorly designed,” Lobo says. “They’re very flat, very large. There’s no segmentation in place so what happens is the threat makes its way into this environment. It spreads across a factory with ease because nothing is segmented and then it can jump from one plant to another plant through the DMZ. That’s common and that’s why the damage is so widespread.”
In order to reduce the damage, Rubo says organizations must invest in endpoint visibility, endpoint compliance, network segmentation, and threat detection and response. Visibility ensures organizations grant the right level of network access to users and devices across domains. Segmentation enables organizations to shrink zones of trust and grant access based on least privilege. Using micro-segmentation, organizations can also automate containment of infected endpoints, should they wish to do so.
“The key thing to start on this journey is you first need visibility of your assets,” Lobo says. “You need to be able to identify vulnerabilities and then build out of that visibility of the communication flows, some kind of segmentation policy inside the environment. That’s where you start.”
Most of the solutions in the visibility space today depend on deep packet inspection to get this visibility. Deep packet inspection is obtained by mirroring traffic from the industrial network onto a separate appliance, but Lobo says that can present problems.
“If you think about control systems, the traffic in these environments is very localized,” Lobo says. “It’s not so much of a north-south traffic flow, it’s more contained. If you need to get visibility to that traffic, you need to have visibility to the traffic at the access layer where the device is connected to the network and if you try to do that by copying traffic from the access layer into an appliance, very quickly that solution becomes very very expensive. “
Cisco solves that problem by eliminating the need for traffic mirroring. The company offers a comprehensive pre-integrated solution to extend zero-trust security to industrial operations. This includes Cisco Cyber Vision, an advanced OT visibility and threat detection solution.
“If you think about where this industry was three or four years ago, there was a big debate about who was responsible for securing this environment,” Lobo says. “That question has now largely been answered. IT is being tasked with securing this infrastructure. It’s not about point solutions at all. It’s about how do you enable customers to take their existing security operations and bring those into those operational domains. How do you take all of this investment and extend it into the operational side of the house.”
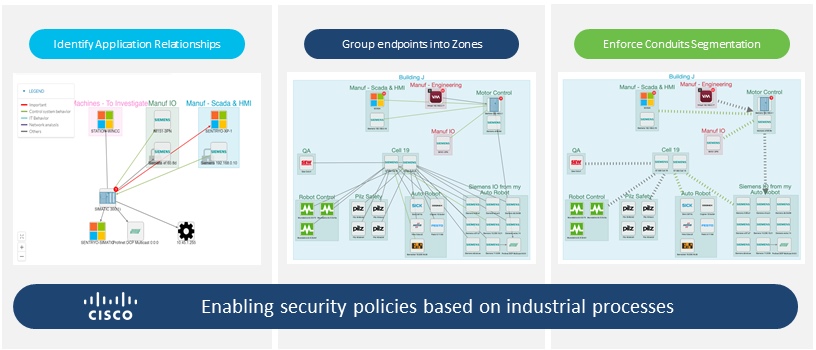
Cisco’s solutions work in tandem. Cisco Cyber Vision allows users to discover endpoints to build zones and conduits. Users can create segmentation policies by sharing group information with Cisco ISE and DNA Center. The Cisco DNA Center also allows users to verify that these policies will not disrupt production by analyzing network traffic behaviors. Overall, these solutions allow users to confidently deploy segmentation policies to enforce zones and conduits.
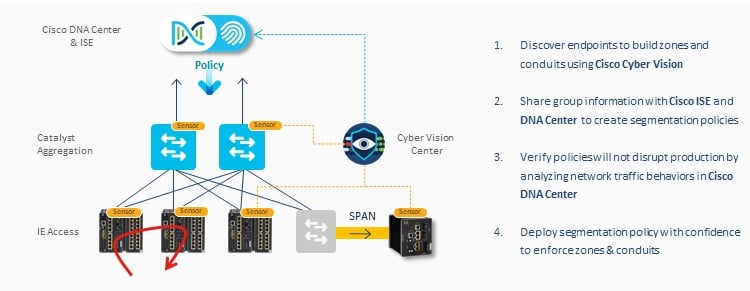
Putting it all together – Cisco Cyber Vision
“The real key to success here is a platform like Cisco Cyber Vision. These are all tools in a toolbox and you’ve got to integrate all of them and allow the IT SOC to be able to monitor these environments,” Lobo says. “So it’s really about integration and how all these components work together and how you enable the IT side of the house to secure this infrastructure. That’s one of the places Cisco is fairly strong because we have a very proactive security portfolio and our offerings within the industrial security space seamlessly integrate with the rest of the products in the space. That’s what enables IT to extend their security operations into the operational space.”
For more information – Cisco Cyber Vision










