New MITRE Engage mappings released for ATT&CK for ICS, ATT&CK for Mobile
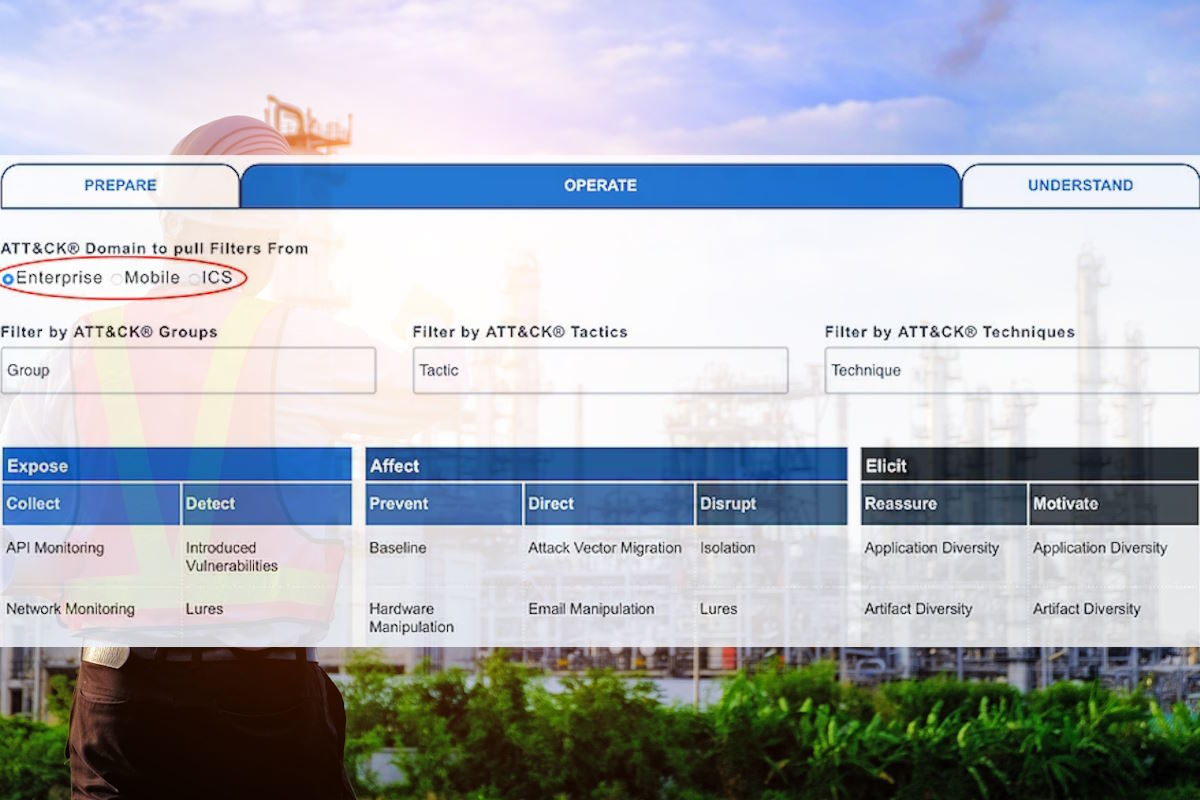
Non-profit organization MITRE announced Monday that its Engage team has introduced new mappings for techniques from the ATT&CK for Mobile and ICS Matrices. Defenders can now apply the same process of identifying engagement opportunities from adversary behavior for operations based in ICS and Mobile environments. The MITRE Engage mappings can be viewed through the Engage Matrix Explorer or in the raw data found on Github.
Currently, MITRE Engage includes several mappings to the Enterprise ATT&CK Matrix, Maretta Morovitz wrote in a Medium post for MITRE Engage. “These mappings can be explored in detail through the Engage Matrix Explorer.”
In her post, Morovitz identified the work done by Dylan Hoffmann, Gabby Raymond, Emma Holt, and Ian Rodriguez.
She detailed that adversary engagement diverges from other defensive technologies in a crucial aspect: it understands the threat as human. “When the adversary is human, rather than mere code, they become susceptible to vulnerabilities and biases. These factors can lead them to make decisions detrimental to their malicious objectives but advantageous to the defender’s interests.”
Morovitz added that even in scenarios lacking direct human involvement, such as when facing an autonomous cyber adversary, adversary engagement can prove effective by addressing the known challenges inherent in such operations.
“One way we can do this is with MITRE ATT&CK,” Morovitz pointed out. “ATT&CK outlines the various tactics and techniques an adversary may engage in during the course of a malicious operation. We can use ATT&CK to look at each adversary tactic, technique and procedure (TTP), analyze how this behavior makes the adversary vulnerable to manipulation, detection, influence, or disruption, and ultimately identify the engagement opportunity space.”
The MITRE Engage Matrix is informed by adversary behavior observed in the real world and is intended to drive strategic cyber outcomes. The Engage Matrix is broken into several components. Across the top of the Matrix are the Engage Goals. Goals are the high-level outcomes that operations would like to accomplish. The next row contains the Engage Approaches, which enables tracking progress towards selected goals. The remainder of the Matrix is composed of the Engage Activities, driven by real adversary behavior, and are the concrete techniques used in the approach which are divided into two categories.
Strategic goals, approaches, and activities bookend the Matrix and ensure that defenders appropriately drive operations with strategic planning and analysis. Engagement goals, approaches, and activities are the traditional cyber denial and deception activities that are used to drive progress toward the defender’s objectives. When an adversary engages in a specific behavior, they are vulnerable to exposing an unintended weakness.
In Engage, “we look at each ATT&CK technique to examine the weaknesses revealed and identify an engagement activity or activities to exploit this weakness. By mapping the Engagement Activities to ATT&CK we can better plan which activities will enable us to reach our strategic objectives,” MITRE said.
Morovitz said that the Engage team worked with experts from across MITRE including MITRE’s new Cyber Infrastructure Protection Innovation Center (CIPIC) under the direction of Mark Bristow, to develop these mappings.
Last week, MITRE launched its AI Assurance and Discovery Lab to discover and mitigate critical risks in artificial intelligence (AI)-enabled systems that need to operate in increasingly complex, uncertain, and high-stakes environments. The lab, which is based at MITRE’s McLean, Virginia, headquarters, features configurable space for risk discovery in simulated environments, AI red teaming, large language model evaluation, human-in-the-loop experimentation, and assurance plan development.










