Mandiant throws light on elusive Sabbath ransomware group targeting critical infrastructure in US, Canada
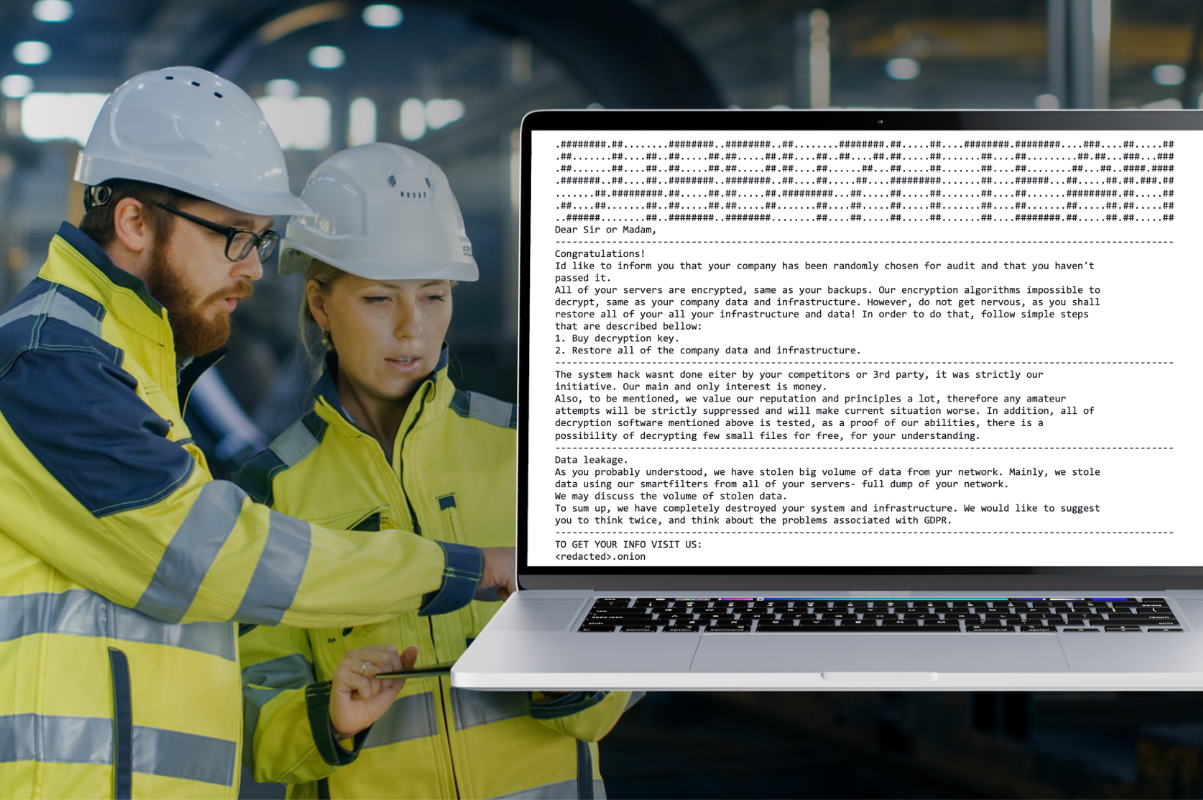
Mandiant released details on the Sabbath ransomware group, targeting critical infrastructure including education, health, and natural resources in the U.S. and Canada. The attacks on critical infrastructure by ransomware groups have become increasingly concerning, and governments have given particular attention to cracking down on ransomware attackers and groups that target and disrupt critical infrastructure.
UNC2190, operating as Arcane and Sabbath, has targeted critical infrastructure since June this year.
In September this year, Mandiant discovered a post on ‘exploit.in’ seeking partners for a new ransomware affiliate program, Tyler McLellan and Brandan Schondorfer, Mandiant researchers wrote in a blog post on Monday. By Oct. 21, the 54BB47h or Sabbath ransomware ‘shaming site and blog’ were created and quickly became the talk of security researchers. In contrast with most other affiliate programs, Mandiant observed two occasions where the ransomware operator provided its affiliates with pre-configured Cobalt Strike BEACON backdoor payloads, they added.
UNC2190 uses a multifaceted extortion model where ransomware deployment may be quite limited in scope, bulk data is stolen as leverage, and the hacker actively attempts to destroy backups. The hacker also utilized public data leaks to extort the victims to pay ransom demands. While Sabbath operates a ‘public shaming blog,’ Mandiant has only observed victims being publicly extorted beginning in mid-November 2021, where six victims were added over the span of two days. Previously under the Arcane brand, Mandiant observed three victims publicly extorted in June 2021, the post added.
While the use of BEACON is common practice in ransomware intrusions, it is unusual for a ransom affiliate program operator to provide the BEACON, providing both challenges for attribution efforts and offering additional avenues for detection, the post said.
In July 2020, UNC2190 deployed Rollcoast ransomware while branded as Eruption. Mandiant has not observed samples of UNC2190-deployed ransomware in 2021 and no samples of Rollcoast have ever been submitted to VirusTotal, the company said. The Rollcoast ransomware would also check the system language and exit if it detected a non-supported language code, such as from Russia, Croatia, or Sweden.
Many other ransomware families have similar checks to avoid encrypting systems in Russia and other Commonwealth of Independent States member countries presumably to avoid attracting the attention of law enforcement in countries where the ransomware operator and affiliates are more likely to reside, Mandiant said.
The Sabbath ransomware surfaced in October this year when the group publicly shamed and extorted a US school district on Reddit and from a now-suspended Twitter account, @54BB47h, Mandiant said. During this recent extortion, the hacker demanded a multi-million-dollar payment after deploying ransomware. Media reports indicated that the group took the unusually aggressive step of emailing staff, parents, and even students directly to further apply public pressure on the school district.
Behind the scenes, few technical changes were made to the affiliate model used to carry out the attacks between the rebranding from Arcane to Sabbath. BEACON samples and infrastructure from both ransomware affiliate services remained unchanged. The malware sample PE compile times were identical on Themida-packed BEACON droppers used by the hacker.
Although UNC2190 is a lesser-known and potentially a smaller ransomware affiliate group, its smaller size and repeated rebranding have allowed it to avoid much public scrutiny. The Sabbath ransomware has continued to operate over the past year while making only minor changes to its strategies and tooling, including the introduction of a commercial packer and the rebranding of its service offering. This highlights how well-known tools, such as BEACON, can lead to impactful and lucrative incidents even when leveraged by lesser-known groups.
Mandiant Intelligence had in October revealed details on the FIN12 group with almost 20 percent of observed victims in the healthcare industry and several of these organizations operating healthcare facilities. Since initially emerging, FIN12 has maintained close partnerships with TRICKBOT affiliated cyber attackers.
Ransomware will continue to expand its reach, DigiCert said in its predictions for 2022. Ransomware attacks impacted a diverse array of industries in 2021, including healthcare organizations, technology companies, automotive manufacturers, and even the NBA.
“Like cyberterrorist events, ransomware attacks often attract heavy press coverage, which can further encourage bad actors seeking publicity,” DigiCert said in a recent post. “We predict that ransomware attacks will continue to escalate, especially as the use of cryptocurrency expands — and makes ransom payments harder to trace outside the banking system,” it added.










