Sectrio data reveals hackers are breaching lack of visibility in OT environments
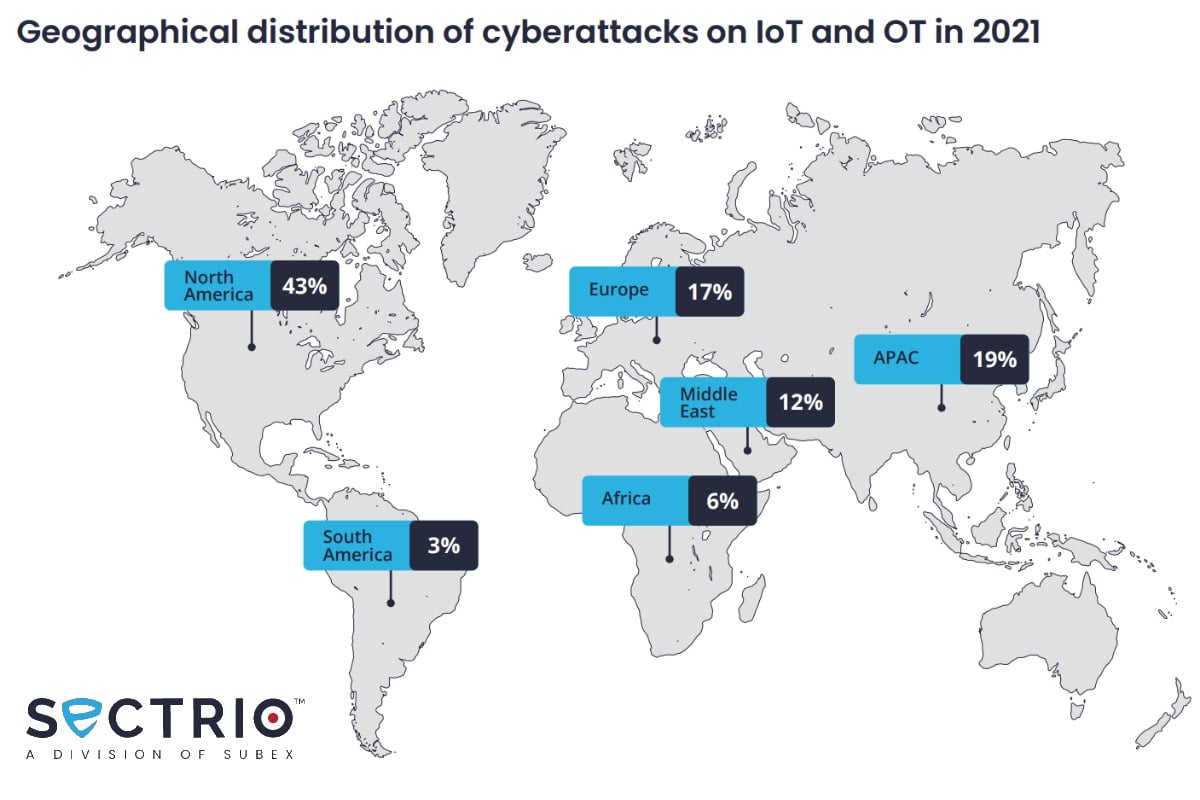
Cybersecurity company Sectrio data disclosed that the U.S. has retained the tag of being the most targeted nation in the world last year, registering a 71 percent increase in attacks over 2020. Energy, healthcare, manufacturing, utilities, maritime, and defense were among the most targeted sectors. In addition, the company found overworked security operation center (SOC) teams and a lack of visibility into some of the infrastructure that led to some businesses getting into the hands of the hackers.
The problem of visibility is more on the OT side than IT side, Kiran Zachariah, vice president for digital security at Sectrio, told Industrial Cyber. “In case of IT, since the devices are often new, inventoried and patched (such devices can also be subject to a vulnerability scan easily), security teams have all the information that have to secure them. However, in case of OT, OT asset inventories are often outdated, the devices cannot be scanned for vulnerabilities and there could be OT devices that have been sitting on the network for years doing functions that the plant team may not even be aware of,” he added.
“Based on the data collected from our honeypot, hackers are conducting recce drives across many sectors in North America,” Sectrio said on Tuesday in its fifth ‘The Global Threat Landscape Report 2022.’ “These include oil and gas, manufacturing, retail, defense, energy and utilities, they are also on the lookout for new targets. The widespread use of OT, partial adoption of automation, and use of new and unhardened IoT and IT devices could impact sectors such as mining and shipping.”
“As per our analysis, mining companies may already be targeted to some extent while the attacks on shipping and freight management companies are now growing,” the company added. Hackers could also target new businesses in segments such as connected vehicles, renewable energy, and retail supply chains. These are priority segments for hackers who use such attacks to mature their breach tactics and to gain media attention, Sectrio added.
The mining sector could be targeted in 2022 as there is rising hacker interest in this sector, Sectrio data revealed in its report, which covers details from threat actors, malware, breach tactics, at-risk sectors, quantum and quality of cyberattacks, and specific threats to operational technology (OT) and IoT deployments and critical infrastructure installations.
The Sectrio data analyzed the evolution of threat vectors, mode of attacks, cyberattacks logged, targets attacked, and cybersecurity gaps exploited. It covered data from over 75 cities across the globe-spanning over a billion attacks and 10,000 (collective and cumulative) hours of analysis of cyberattacks, malware, hacking tactics, network breaches, data leaks, and other important aspects related to enterprise and critical infrastructure cybersecurity networks.
The company also found malware-laden traffic was coming into North American cities from across the globe. “A majority of this traffic could be traced to APT hotspots. Possible botnet traffic emerging from within the US was also logged by our honeypots. This could be the outcome of devices operating in unmonitored environments being hacked into and used to route malware-laden traffic into other networks in the chain.”
Sectrio found that hackers are now targeting widespread disruption and huge ransoms through targeted cyberattacks. It revealed that ransom cost per GB of data held by hackers is now US$39000, as the rise in average ransom demand stood at 71 percent.
“While the geopolitical motivation in many of these attacks remains at a very high level, the expansion of botnets in Mexico poses a new security risk to businesses in the region,” Sectrio said. Manufacturing facilities in Mexico are also being subject to high levels of reconnaissance probes by hackers, it added.
Colorado-based Sectrio also identified that some hackers are carrying out localized attacks from within the region using sophisticated phishing kits developed in parts of Eastern Europe and the Middle East. “We came across many such kits that were modified to some extent to target businesses in US and Mexico. These kits are now freely available on the web but sophisticated APT groups such as Lazarus and Fancy Bear could be embedding them with trojans to control the networks and data in businesses targeted by these local hackers,” it added.
Sectrio data also pointed to a new tactic that advanced persistent threat (APT) groups are using to widen their net. “By offering free phishing kits, they are allowing other groups to conduct the initial hacking work while they lurk in the background waiting to jump networks or digital assets to reach a target asset which could be a critical infrastructure facility or a defense installation,” it added.
The company also detected that the malware load in the traffic analyzed by its team has grown significantly in the last six months of last year. “This over-the-board increase will definitely put an additional strain on the already overworked SOC teams managing the security needs of businesses in sectors such as manufacturing, utilities, and others,” it added.
Hackers are specifically targeting control systems and connected IoT devices, Sectrio data revealed. “The former to cause disruption and the latter to target third-party infrastructure such as websites, critical servers, and even mobile phones,” it added.
“These are targeting behaviors that we have seen in our honeypot locations in North America,” Zachariah said. “IoT devices are being used to create breaches in critical and non-critical infrastructure. Considering the volume of such attacks logged by our honeypots and the growth in botnets (IoT devices hijacked and controlled by hackers), there must have been instances of hackers successfully breaching defenses,” he added.
Sectrio data also recognized that supply chains are presenting hackers with a moving and lucrative target. Apart from large-scale disruption, such attacks also offer more return on investment, making such attacks a favorite due to the opportunity to strike businesses from multiple entry points. The company identified that reconnaissance attacks continue to rise across supply chains. Hackers are maintaining a high level of interest in attacking and studying supply chains.
“There could be adversarial groups that are focused on exclusively attacking supply chains as such high levels of interest can (ideally) only be sustained through focused efforts,” the report said.
Manufacturing, retail, and utility supply chains were targeted the most, Sectrio data disclosed. “Within manufacturing, those related to large-scale manufacturing of white goods, automobiles, defense hardware, and farm equipment were the ones targeted the most by hackers. In the case of every supply chain attack, multiple vendor chains and even sub-vendors were targeted (in the case of businesses with long tails),” it added.
Supply chain poisoning is ‘now a major concern,’ Sectrio revealed. “The defense sector was most impacted by supply chain poisoning in 2021. Random military hardware including drones, communication equipment, controllers, surveillance hardware switchgear, inspected and scanned by our research team revealed the presence of suspicious foreign contaminants and signs of digital infection,” it added. Supply chain poisoning refers to how a code level infection is added in software, components used in the development of software, or firmware supplied to businesses and government.
Sectrio data further determined that investments in OT cybersecurity investments and attention are still lagging. Businesses that are hosting complex hybrid environments or are connected to IT, OT, and the IoT environments are now gradually understanding the importance of ramping up their cybersecurity measures to align them with the complexity involved in securing such environments. “However, the hackers are miles ahead of them as they are well aware of these cybersecurity gaps than the cybersecurity teams protecting them,” it added.
Looking ahead in 2022, Sectrio said that new threats also emerge along with new actors, new malware, and breach methods. Some of the likely key factors include the rise of geopolitical threats, network and device vulnerabilities that will get more attention from hackers and businesses, and the need for compliance and standards to move from a voluntary exercise to a compulsory one for sectors that are not hosting any critical infrastructure.
It also expects supply chain vetting and internal security practices will turn mainstream and more streamlined, while attack surfaces will continue to expand due to rising digital transformation and automation leading to more IoT and OT cyberattacks grabbing headlines.










