NIST CSF 2.0 Core discussion draft released, stakeholder feedback invited
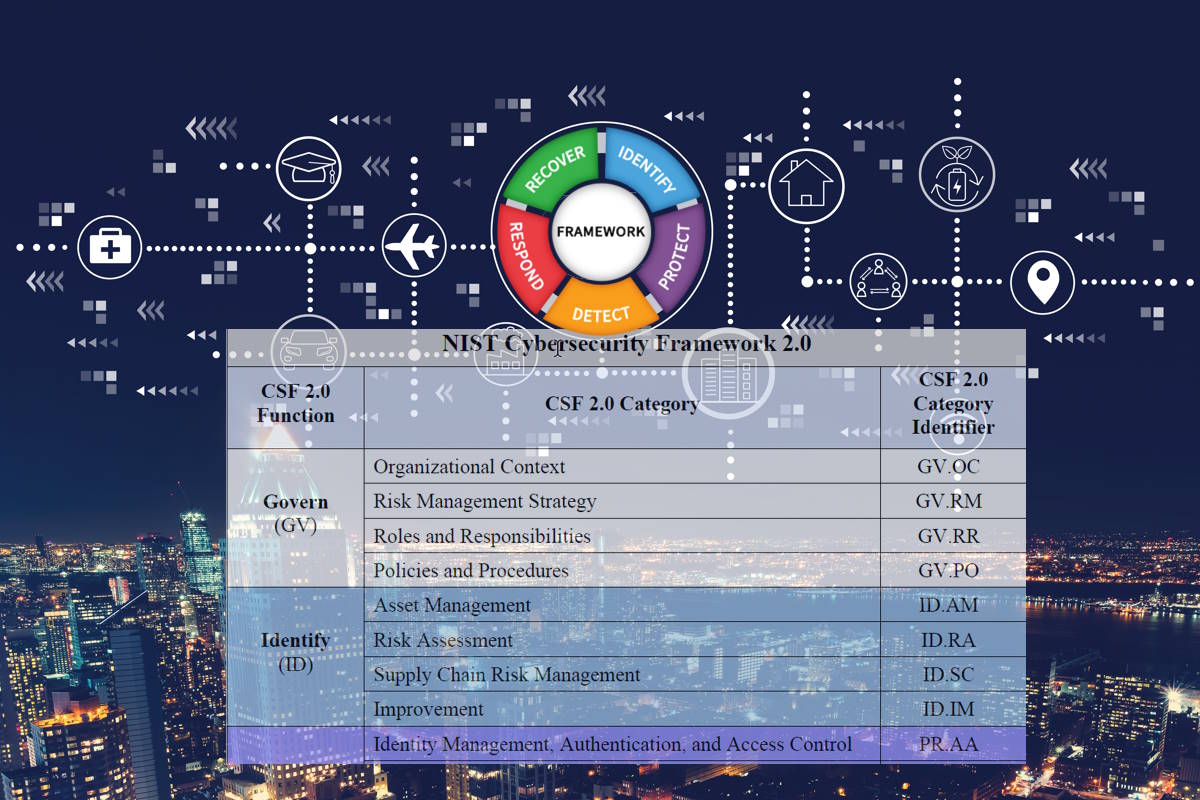
The National Institute of Standards and Technology (NIST) published Monday a discussion draft that identifies the potential Functions, Categories, and Subcategories of the NIST Cybersecurity Framework (CSF) 2.0 Core. In its preliminary stage, the early draft of the NIST CSF 2.0 Core, covers cybersecurity outcomes across six functions, 21 categories, and 112 subcategories, and is intended to increase transparency of the update process and promote discussion to generate concrete suggestions for improving the framework.
The NIST is releasing the document for discussion to inform the development of the complete NIST CSF 2.0 draft. Feedback on the discussion draft may be submitted to [email protected] at any time, and it ‘will inform the complete NIST CSF 2.0 draft anticipated to be released for public comment this summer.’
The agency also seeks feedback as to whether the cybersecurity outcomes address current cybersecurity challenges faced by organizations, are aligned with existing practices and resources, and are responsive to the comments. NIST seeks concrete suggestions about improvements to the draft, including revisions to functions, categories, and subcategories, and submissions of omitted cybersecurity outcomes.
NIST also requests feedback on the format, content, and scope of Implementation Examples; suggestions of possible Examples; and the appropriate level of abstraction between Subcategories and Examples. In addition, NIST requests feedback on the best way to showcase final modifications from CSF 1.1 to CSF 2.0 to ease the transition.
The discussion draft of the NIST CSF 2.0 Core is a continuation of NIST’s extensive engagement with the community to craft CSF 2.0. The Discussion Core presented here reflects feedback received thus far through:
- The 92 written responses to the January 2023 CSF 2.0 Concept Paper,
- The February 2023 In-Person Working Sessions were attended by about 250 participants in Rockville, Maryland,
- The ‘Journey to the NIST Cybersecurity Framework 2.0’ February 2023 Workshop #2 was attended virtually by more than 2,000 participants from 69 countries,
- The ‘Journey to the NIST Cybersecurity Framework 2.0” August 2022 Workshop #1 was attended virtually by about 4,000 participants from 100 countries),
- The 134 written responses to the February 2022 NIST Cybersecurity RFI,
- Feedback from organizations that have leveraged the CSF over the years,
- NIST participation in conferences, webinars, roundtables, and meetings around the world.
The CSF 2.0 Discussion Core increases focus on cybersecurity outcomes applicable to all organizations, removing language specific to critical infrastructure across the Core. It also covers the prevention of cybersecurity incidents through outcomes-focused in Govern, Identify, and Protect functions and the detection and response of incidents through the Detect, Respond, and Recover functions. Additionally, cybersecurity governance through a new Govern function covering organizational context, risk management strategy, policies and procedures, and roles and responsibilities.
The Discussion Core also includes cybersecurity supply chain risk management outcomes, continuous improvement through a new Improvement Category in the Identify function, and leveraging the combination of people, process, and technology to secure assets across all Categories in the Protect function. It also includes resilience of technology infrastructure through a new Protect function category, and cybersecurity incident response management, including the importance of incident forensics, through new categories in the Respond and Recover functions.
In January, NIST released a bulletin inviting industry participants and other interested collaborators to participate in the NCCoE project, which focuses on responding to and recovering from a cyber incident within an operational technology (OT) environment. The NCCoE project focuses on the Respond and Recover portions of the NIST CSF while guiding manufacturing organizations in designing mitigations into an OT environment to address cyber incidents.
While the Core is arguably the most recognizable piece of the CSF, it is not the only element of the CSF that will be updated, the NIST discussion draft document pointed out. “There is still much to do to implement the CSF 2.0 Concept Paper, including development of guidance on CSF implementation, the relationship, and alignment of the CSF to other NIST and non-NIST resources, and the use of the CSF for assessment and measurement.”
NIST encourages the community to continue engaging in the update process, including the Calls to Action identified in the CSF 2.0 Concept Paper. Progress in the CSF 2.0 effort, as well as ways to engage, can be found on the NIST CSF 2.0 webpage.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) published last month stakeholder-based updates to the Cybersecurity Performance Goals (CPGs). In response to feedback received directly from the critical infrastructure community, these CPGs have been reorganized, reordered, and renumbered to align closely with NIST CSF functions to help organizations use the CPGs to prioritize investments as part of a broader cybersecurity program built around the CSF.
Jen Easterly, CISA director said in the March 2023 update of the CPGs version 1.0.1 that the agency heard “the global Operational Technology and Industrial Control Systems (OT/ICS) community clamor to be seen and recognized alongside traditional IT security and supported in their essential role of defending our increasingly connected electric grids, hospitals, water facilities, and other critical infrastructure.”
She added that it became clear that even with comprehensive guidance from sources like the NIST CSF, many organizations would benefit from help identifying and prioritizing the most important cybersecurity practices along with support in making a compelling argument to ensure adequate resources for driving down risk.
Last week, the NIST also published its Identity and Access Management (IAM) Roadmap which provides a consolidated view of NIST’s planned IAM efforts over the coming years. It singles out strategic objectives, aligns efforts with nationally defined priorities, and supports long-term planning. It is informed by advances in the technology landscape, current policies and strategies, feedback on NIST’s existing identity and access management guidance, and engagement with public and private stakeholders.
As the roadmap is an initial draft to gain further input to inform of the agency’s plans, NIST seeks ‘specific input’ from stakeholders on are the guiding principles clear, are any important principles missing, and if any of the strategic objectives need clarification. The draft also seeks feedback on whether any key objectives are missing, if there are specific activities, research, or guidance which should be included, and if so, why. The document also seeks comments on which strategic objectives are most likely to have an impact and should be prioritized, and what additional outputs would be useful to accompany the roadmap.
Feedback and comments should be directed to [email protected] by Jun. 1, 2023, with relevant comments, including attachments and other supporting material, that will be made publicly available on the IAM program page.
In March, the National Security Agency (NSA) collaborated with the CISA and industry partners to release a guide providing actionable IAM recommendations to secure systems from threats better. Developed for system administrators, the paper identifies key mitigations to the top threats providing best practices and mitigations to counter threats to IAM related to identity governance, environmental hardening, identity federation/single sign-on, multi-factor authentication, and IAM auditing and monitoring.










