Beyond MFA: Can We Make Accessing Critical Infrastructure—Even in Air Gaps—Safe in 2023?

In November 2022, Industrial Cyber reported:
“MSTIC disclosed last month evidence of a novel ransomware campaign targeting organizations in the transportation and related logistics industries in Ukraine and Poland utilizing a previously unidentified ransomware payload . . . The payload was deployed by the hacker after an initial compromise that involved gaining access to highly privileged credentials.”
We see this time and again, yet we’re still surprised by how simple (if not easy) it is to obtain ill-begotten credentials, often by exploiting unsuspecting users or purchasing them on the dark web and then using privilege escalation tooling to target essential services. Credentials still factor into 80% of cybersecurity breaches, even as governments worldwide mandate critical infrastructure (CI) ecosystems adopt Zero Trust security postures.
In the US, for example, a March 2022 “Statement by President Biden on our Nation’s Cybersecurity” calls for, “extensive cybersecurity measures for the Federal Government and those critical infrastructure sectors where we have authority to do so . . . to enhance cybersecurity across all our critical infrastructure.” The statement links to guidance on hardening defenses where the number recommendation is: Mandate the use of multi-factor authentication on your systems to make it harder for attackers to get onto your system.
CI Faces Unique Authentication Challenges
Cybersecurity giant Barracuda surveyed 800 senior executives responsible for securing Industrial Internet of Things (IIoT) or operational technology (OT), areas that often involve air gaps. Findings showed just 18% of companies enforced MFA and restricted remote access.
We might suspect this would be different on the control and management side, but even there many organizations don’t extend MFA to air-gap islands for obvious reasons:
- they assume the air-gap moat magically protects them—an erroneous assumption
- SMS and emailed second-factor authentication (2FA) won’t work without internet connectivity
The net-net: MFA can’t resolve CI’s increasingly vital authentication problem: enabling secure remote access to air-gapped environments.
Physical Challenges to Strong Authentication in Air Gap Environments
As you may know, air-gapped computing has network interfaces removed or disabled to prevent connection to the Internet or other external networks. These islands often house the most critical elements of business operations that are physically and cyber-moated to ensure only authorized people get access.
Air gapping reduces the digital attack surface where secrets and workflows when compromised endanger lives or cripple the organization’s ability to function including networks and systems operated by:
- Military/government agencies
- Financial institutions and exchanges
- Industrial control systems (ICS) such as SCADA in oil and gas fields
- Power plants
- Mass transit
- Air traffic control
- Healthcare facilities
New risks emerge
While absolute physical and digital isolation makes it hard, though not impossible to breach air-gapped environments, doing so crushes productivity:

- Software updates must be done manually (and some legacy systems may be wholly unsupported)
- Intrusion detection may be delayed should an adversary gain access via leaked or stolen credentials or social engineering
- Sharing of data requires physical media such as flash drives that can be lost or damaged (who remembers Stuxnet?)
- Alternative media such as acoustic, light, seismic, magnetic, thermal, and radio frequencies can be used to distribute malware and steal data via “air-gap covert channels
- “Firmware and other updates to IoT devices cannot be centrally managed
- Businesses hold large amounts of technical debt, ironically, from decades of market success (the stuff still works!)
Recent geopolitical attacks involving Russia and Ukraine have heightened awareness around securing both data and operational technology (OT) controls within air-gapped environments. Since traditional MFA won’t work without the Internet, another layer must be employed to ensure strong authentication.
Raising the Stakes with Passwordless MFA
The real problem isn’t the lack of MFA; it’s the fact that traditional MFA really isn’t enough, as attackers have innovated tactics to go around it. To date, most identity-proofing procedures involve passwords, which involves people choosing, losing, and rechoosing credentials—a dynamic that frustrates both users and IT. Cisco, the networking and security giant, learned this lesson the hard way in 2022. A phisher scraped a Cisco employee’s VPN password from their personal Google account. They then leveraged MFA fatigues push bombing to ultimately reach admin privileges in the corporate network.
Leading vendors like Microsoft, Google, and Cisco are raising the stakes on authentication by espousing a passwordless approach. Done right, passwordless MFA takes users out of the password management business altogether and places the secret keys to the kingdom squarely within IT’s domain.
Instead of relying on “what users know”—which they can easily be tricked into sharing—passwordless MFA leads with the more reliable “what you have” and “what you are” elements of identity-proofing. Better yet, done right, passwordless MFA extends strong remote authentication to air-gapped environments.
Obstacles to Passwordless MFA
The technology poised to drive passwordless authentication, PKI or Public Key Infrastructure, is in its early stages of adoption. Many initial implementations use expensive smart cards and require significant retooling of applications and back-end directories—a major deterrent for users and IT alike. Transitioning to PKI technologies like X.509 certificate approaches can disrupt operations and create hybrid login workflows.
As the technology advances, approaches based on FIDO2 keys offer cost and provisioning advantages over traditional smart card approaches and costly upgrades to certificate issuing infrastructure. This approach, however, requires support for FIDO2 CTAP2 or WebAuth protocols needed to read FIDO keys, something most devices in air-gap environments won’t support.
The promise of passwordless being what it is—a way to enable secure remote access to air-gap islands—identity managers should consider these and other more creative techniques that streamline cost and complexity.
Devising An Air-Gap Friendly Approach
One approach is to leverage a series of progressive tunneled interactions to achieve strong remote authentication and strike the best balance between security and productivity. In the example shown below, a user must authenticate into three separate directories using three independent identities.
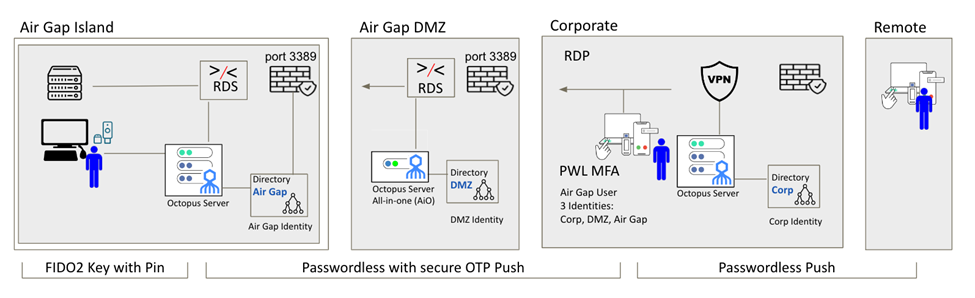
Each of the three progressive zones—Corporate, De-militarized zone (DMZ), and Air Gap—is serviced by its own unfederated directory:
Corporate – Passwordless MFA: Users type their username which generates a push to their mobile app to perform biometric authentication, satisfying both the “what you have” and “what you are” criteria to gain access to corporate resources.
DMZ – Passwordless DMZ identity: The next step is to access the DMZ via Remote Desktop Protocol (RDP) via a DMZ server running Remote Desktop Services (RDS). Authentication is accomplished passwordlessly through an unfederated DMZ identity and synchronized OTP services exposed only to the user after strong passwordless takes place on a mobile app.
Manually typing the code fulfills the requirement for no communication in or out of the air gap and verifies something the user has and is, with the mobile biometric requirements.
Air Gap – Passwordless Air Gap identity: Authentication is accomplished to the Air Gap identity and OTP delivered from the user’s SDO app, but this time using their unfederated Air Gap directory identity, similar to crossing the DMZ.
With this passwordless workflow, users never know a password, which eliminates the risk of sharing accounts or exposing secrets to intruders and nefarious insiders. Secrets automatically get rotated to shorten exposure windows. Admins gain the confidence that access is verified with legitimate user multi-factors and air gap users get a streamlined login that works with corporate apps and services too.
Buyer Beware
Like everything else, how you implement passwordless MFA drives and defines success. Beware of “passwordless” solutions that merely reduce the frequency with which users enter passwords but don’t eliminate them entirely from the user knowledge. After all, infrequently use passwords are the most dangerous as they have to be simple or written down. Other solutions—most in fact—can’t extend MFA to legacy systems typically found within air-gapped and industrial environments.










