US GAO reports that DOD has partially implemented selected cybersecurity requirements for CUI systems
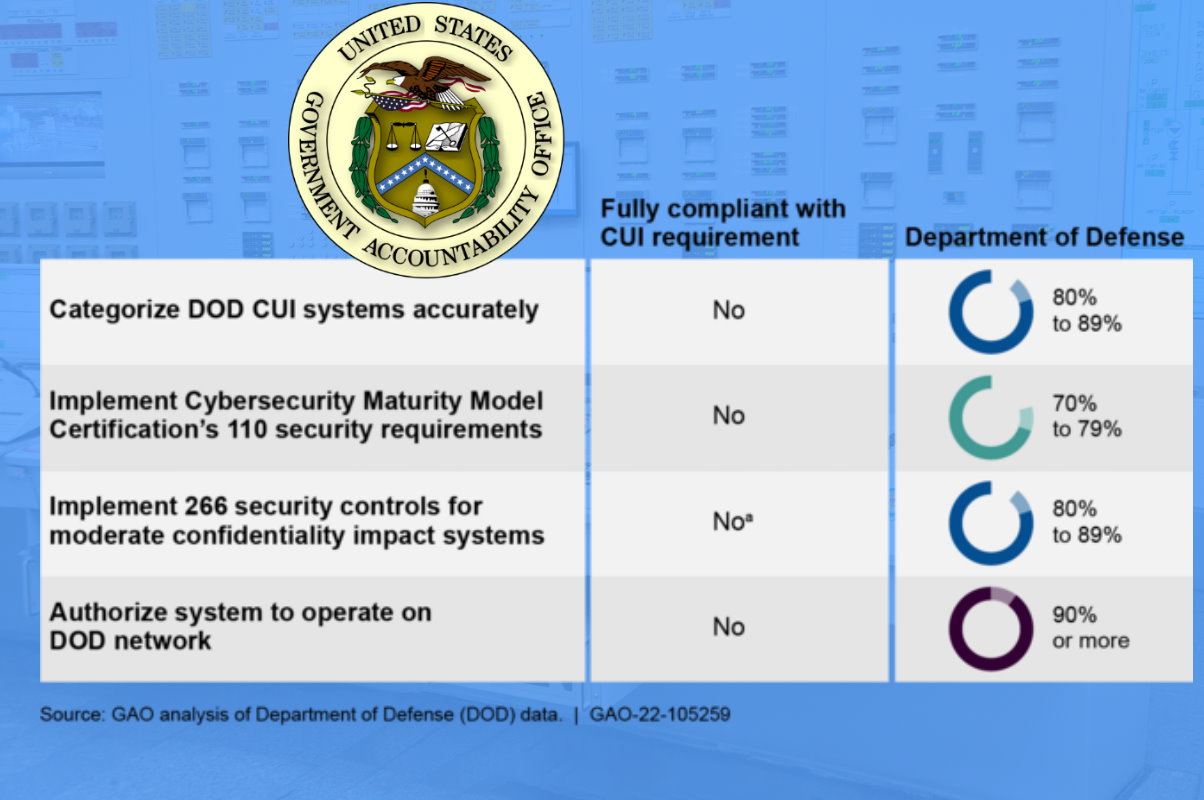
A report by the U.S. Government Accountability Office (GAO) determined that the Department of Defense (DOD) has reported implementing more than 70 percent of four selected cybersecurity requirements for controlled unclassified information (CUI) systems, based on GAO’s analysis of DOD reports, including a June 2021 report to Congress, and data from DOD’s risk management tools. The GAO report also describes the status of DOD components’ implementation of selected CUI cybersecurity requirements, and actions taken by the DOD CIO to address the cybersecurity of CUI systems.
The selected parameters in the GAO report include categorizing the impact of the loss of confidentiality, integrity, and availability of individual systems as low, moderate, or high, implementing specific controls based in part on the level of system impact, and authorizing these systems to operate. “As of January 2022, the extent of implementation varied for each of the four requirement areas. For example, implementation ranged from 70 to 79 percent for the cybersecurity maturity model certification program DOD established in 2020, whereas it was over 90 percent for authorization of systems to operate,” the GAO report identified.
“As the official responsible for department-wide cybersecurity of CUI systems, the DOD Office of the Chief Information Officer (CIO) has taken recent action to address this area,” the GAO report said. Specifically, in October 2021 the CIO issued a memorandum on implementing controls for CUI systems. The memo identified or reiterated requirements that CUI systems must meet. These included requiring additional supply chain security controls and reiterating that all CUI systems have valid authorizations to operate, it added.
Additionally, the GAO report said that the reminded system owners of the March 2022 deadline for all DOD CUI systems to implement necessary controls and other requirements. The Office of the CIO has been monitoring DOD components’ progress in meeting this deadline, it added.
For the purpose of the report, the scope of GAO analysis is focused on approximately 2,900 CUI systems across the department. Five DOD components – Army, Air Force, Defense Health Agency, Marine Corps, and Navy – own about 85 percent of the department’s CUI systems.
The GAO said that it conducted the performance audit from May 2021 to May 2022 in accordance with generally accepted government auditing standards. “Those standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. We believe that the evidence obtained provides a reasonable basis for our findings and conclusions based on our audit objectives,” it added.
GAO’s analysis of DOD-reported data determined that DOD components have taken actions to implement selected cybersecurity requirements for CUI systems, but none were fully compliant. “DOD is working toward achieving 100 percent compliance in three of the four categories applicable to the department: categorize systems accurately, implement 266 security controls, and authorize systems to operate on DOD’s network,” the report added.
“As of January 2022, DOD CIO officials reported that DOD components had incorrectly categorized 13 percent of its CUI systems below the moderate-impact confidentiality level,” the GAO report said. “We found that the Defense Health Agency accurately categorized more than 90 percent of its CUI systems whereas the Air Force inaccurately categorized the impact level for more than 20 percent of their respective systems,” it added.
The DOD’s CMMC version 2.0 program, if implemented, will require defense contractors whose systems process, transmit, or store DOD CUI to be compliant with NIST Special Publication 800-171, in order to achieve level 2, advanced cybersecurity, GAO identified in the report.
“DOD’s cybersecurity data reflected that DOD components’ CUI systems were compliant with 78 percent of the 110 security controls that CUI systems of defense contractors must meet under DOD’s proposed CMMC version 2.0 program,” GAO said. “However, DOD’s components’ systems would not be approved to process, transmit, or store DOD CUI if CMMC version 2.0 applied to the components. This is because CMMC would require defense contractors to comply with all 110 security controls to achieve level 2, advanced cybersecurity,” it added.
As of January 2022, “the DOD components had not met 22 percent of the 110 security controls. Specifically, we found that the Marine Corps and the Navy CUI systems were compliant with more than 80 percent but less than 90 percent of the CMMC-required security controls for their systems while the other four DOD components were compliant with more than 70 percent but less than 80 percent,” the GAO report added.
To achieve the required moderate-impact confidentiality level, DOD officials who authorize information systems are supposed to select applicable security controls from a list of 266 security controls, GAO said in the report.
“As of January 2022, DOD CIO officials had found DOD components were compliant with 82 percent of moderate-impact confidentiality controls,” the report said. “We found that the Air Force, Army, Marine Corps, and Navy were compliant with more than 80 percent but less than 90 percent of moderate-impact baseline confidentiality controls, while the Defense Health Agency and Other components were non-compliant with more than 20 percent of the moderate-impact baseline confidentiality controls,” it added.
The agency also identified that the DOD’s risk management framework and NIST’s guidance require a system before it is connected to the DOD network, to undergo an assessment of its security and residual risk. “If the results of this assessment are acceptable to the authorizing official, the system is granted an authorization to operate on DOD’s network.22 As a part of the risk management process, DOD systems are to be reauthorized to operate on DOD’s networks every 3 years,” it added.
Last October, the Deputy CIO for Cybersecurity issued a memorandum that defined requirements that DOD’s CUI systems must meet and establishes a deadline for compliance of March 2022. The memorandum defines minimum impact categorization requirements for CUI systems, additional supply chain security controls, a reiteration of the requirement of valid authorizations for CUI systems, and a timeline for compliance.
“As of February 2022, DOD reported that approximately 20 percent of CUI systems had not met the requirements and officials had not developed associated corrective-action plans,” the GAO report said. According to DOD officials, non-compliant systems will continue to operate while officials implement their corrective-action plans. DOD officials also stated that the five-year completion period will account for possible budget issues during remediation, it added.
Last December, GAO released a report that addressed what steps the DOD has taken to develop the CMMC model, the extent to which DOD has made progress in implementing CMMC, including communication with industry, and the extent to which DOD has developed plans to assess the effectiveness of CMMC.










