NSA delivers recommendations for maturing devices using zero trust device pillar within security framework
The U.S. National Security Agency (NSA) published Thursday a Cybersecurity Information Sheet (CSI) covering zero trust security framework that enables federal agencies, partners, and organizations to assess devices in their systems and be better poised to respond to risks associated with critical resources. The document provides recommendations for maturing devices using the zero trust device pillar to ensure that devices seeking access earn trust based on device metadata and continual checks to determine if the device meets the organization’s minimum bar for access.
The ‘Advancing Zero Trust Maturity Throughout the Device Pillar’ CSI offers crucial guidance to network owners and operators within the National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB). These stakeholders must include device identification, inventory, and authentication, device authorization using real-time inspection, and remote access protection. The document also serves as a strategic response to the escalating cybersecurity threats that are surpassing the capabilities of traditional defense mechanisms, necessitating a scalable and more effective security approach.
The device pillar is a foundational component of zero trust to ensure devices within an environment,and devices connected to or attempting to connect to resources,are located, enumerated, authenticated, and assessed. Devices are subsequently permitted or denied access, based on a dynamic risk calculation, to specific objects or data. A device is only authorized access if it is ‘compliant’ (meets the environment’s security conditions specified by policy). Devices determined to be non-compliant may be denied access or granted limited access.
The primary capabilities of the device pillar include identification, inventory, and authentication; detection of unknown devices and configuration compliance checks of known ones; device authorization using real-time inspections; remote access protections; hardware updates and software patches; device management capabilities; and endpoint detection and response for threat detection and mitigation.
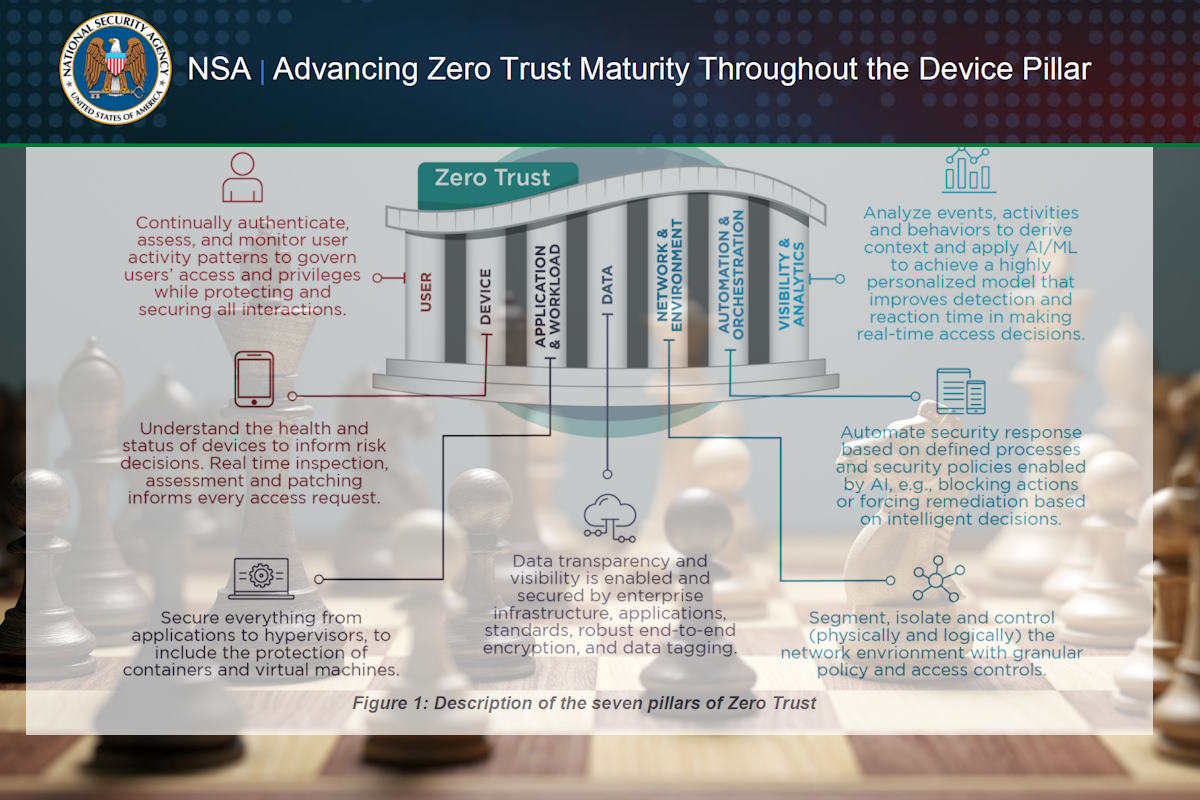
The NSA detailed that the zero trust security model is best illustrated as seven pillars that together comprise the complete cybersecurity posture. These include user, device, network and environment, application and workload, data, automation and orchestration, and visibility and analytics. Each pillar requires certain criteria and objectives to achieve zero trust enactment.
Focused on the device pillar with recommendations for reaching increasing maturity levels of device pillar capabilities, the NSA document prescribes mechanisms to shield devices from low-level, persistent threats over their entire lifecycle. Adoption of a zero trust mindset “enables organizations to never assume devices within an established environment are secure or that actors cannot hide from defenses in the OS or applications by delving into hardware and firmware.Implementing mature ZT device pillar capabilities enables organizations to assess devices and respond to risks to critical resources in the environment,” it added.
The NSA document listed seven device pillar capabilities associated with maturity levels. These include device inventory, device detection and compliance, device authorization with real-time inspection, remote access protection, automated vulnerability and patch management, centralized device management, and endpoint threat detection and response. As capabilities mature and additional capabilities are deployed, enterprises advance through basic, intermediate, and advanced maturity phases and are more able to operate according to zero trust principles.
Discovering and defining the organization’s mission and identifying the supporting assets that need to be secured will help build a clearer picture of the as-is architecture which can be compared against the recommendations in this pillar along with the other zero trust pillar CSIs. This comparison will help all stakeholders to identify organizational risks and gaps and ultimately inform them on what a mature zero trust architecture will look like for their organization. Each organization will need to evaluate their individual requirements to determine a suitable solution. The goal is to develop zero trust roadmap strategies that align with the organization’s zero trust goals.
The NSA also listed a couple of key ideas for implementing the zero trust device pillar. These include detecting and identifying devices within or connecting to the environment; authenticating and continually re-authenticating devices; using automated solutions to manage device configurations, vulnerabilities, and patches; and maintaining a dynamic authorization list with policies and procedures in place for denied devices.
It also covers conducting risk-based assessments to determine access for all devices; enforcing more stringent access policies for remote access due to the higher risk environment; and monitoring endpoints for signs of threat activities, incorporating endpoint monitoring and responses into network-wide security capabilities.
NSA is assisting DoD customers in piloting zero trust architectures, coordinating activities with existing NSS and DoD programs, and developing additional zero trust guidance to support system developers through the challenges of integrating zero trust within NSS, DoD, and the DIB environments. Upcoming additional guidance will help organize, guide, and simplify incorporating zero trust principles and designs into enterprise networks.
In March, the NSA published a CSI that helps system operators mature identity, credential, and access management (ICAM) capabilities to mitigate certain cyber threat techniques. The initiative further discusses how these capabilities are integrated into a comprehensive zero trust framework while providing system owners and operators the ability to identify, resist, and respond to various cyber intrusion techniques.










