NSA rolls out details on advancing zero trust maturity throughout the network, environment pillar
The U.S. National Security Agency (NSA) is releasing a cybersecurity information sheet (CSI) that details curtailing adversarial lateral movement within an organization’s network to access sensitive data and critical systems.
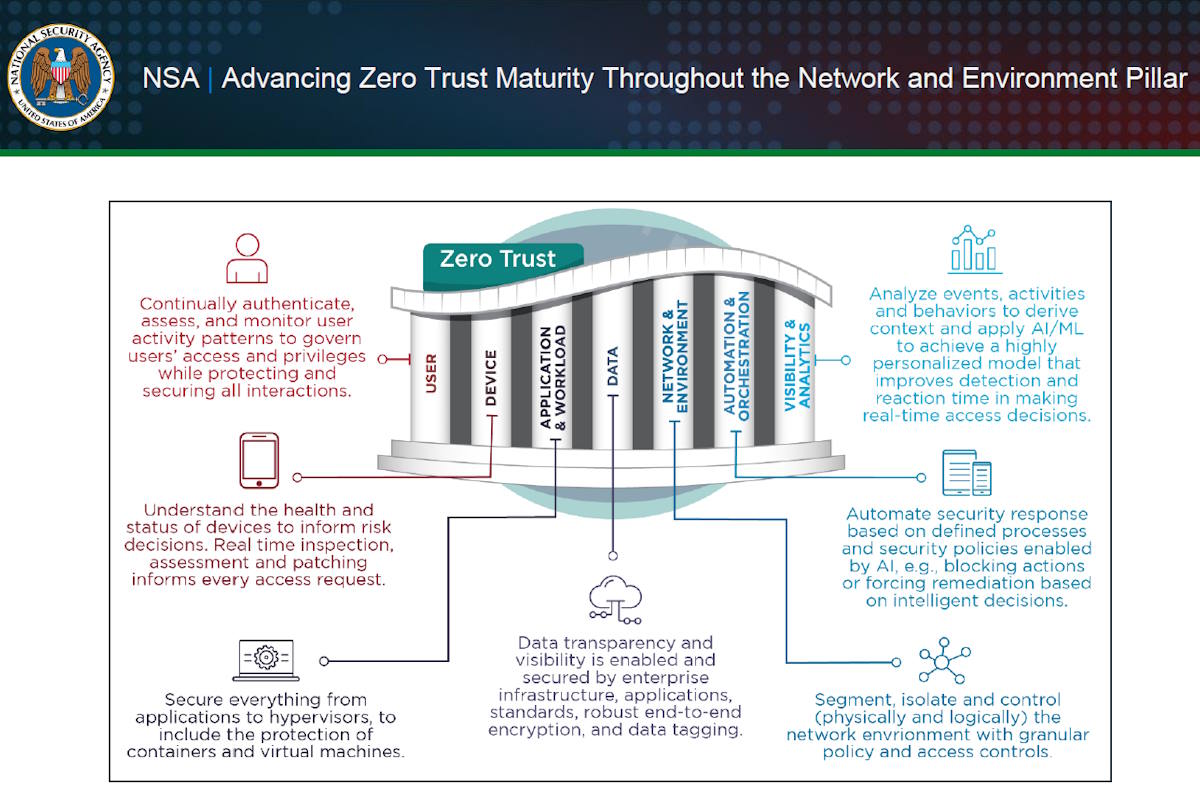
The zero trust network and environment pillar curtails adversarial lateral movement by employing controls and capabilities to logically and physically segment, isolate, and control access (on-premises and off-premises) through granular policy restrictions. It also strengthens internal network control and contains network intrusions to a segmented portion of the network using zero trust principles.
Entitled ‘Advancing Zero Trust Maturity Throughout the Network and Environment Pillar,’ the CSI outlines the key capabilities of the network and environment pillar, including data flow mapping, macro and micro segmentation, and software defined networking. NSA is assisting Department of Defense (DoD) customers in piloting zero trust systems and is developing additional zero trust guidance for incorporating zero trust principles and designs into enterprise networks.
“Organizations need to operate with a mindset that threats exist within the boundaries of their systems,” Rob Joyce, NSA cybersecurity director, said in a media statement. “This guidance is intended to arm network owners and operators with the processes they need to vigilantly resist, detect, and respond to threats that exploit weaknesses or gaps in their enterprise architecture.”
Targeted primarily for national security systems (NSS), DoD, and the Defense Industrial Base (DIB), the guidance document may also be useful for owners and operators of other systems that might be targeted by sophisticated malicious actors. It incorporates guidance from the DoD’s Zero Trust Strategy, Zero Trust Reference Architecture, and Cybersecurity Reference Architecture (CSRA). Additional guidance for other system owners and operators is also available from the National Institute of Standards and Technology (NIST) and the Cybersecurity and Infrastructure Security Agency (CISA).
“While a network is the connectivity of hardware and software, the cybersecurity environment as defined in the DoD CSRA and NIST SP 800-207 is the digital ecosystem encompassing all of the network components, non-person entities, and protocols for inter-communication, The document identified. “The ZT maturity model delivers a network secured in-depth through several key functions of each of the four networking and environment pillar capabilities: Data flow mapping, Macro segmentation, Micro-segmentation, and Software Defined Networking.”
The network and environment serve this model through a segmented robust architecture that must be intentionally developed at the outset and maintained and improved upon throughout the environment’s lifecycle. In addition to a secure network segmentation framework, zero trust architecture employs secure network traffic management through strong encryption and persistent verification of all users, devices, and data.
Automation and orchestration depend on defined processes and security policies, along with adaptive network capabilities to dynamically isolate or modify network segmentation as needed. Intuitive analytics monitor networks and other events and activities for suspicious behaviors. Given the proper application, these capabilities support the zero trust architecture and have the potential to improve the network’s security.
The network and environment pillar isolates critical resources from unauthorized access by defining network access, controlling network and data flows, segmenting applications and workloads, and using end-to-end encryption. This is accomplished through proper network segmentation at the macro and micro levels, combined with software defined networking (SDN), to allow centralized control and automation. The pillar depends on an organization’s depth of awareness and understanding of its data –how it flows within standalone networks and across networks that interconnect physical infrastructure, cloud computing, and distributed work environments.
Data flow mapping identifies the route data travels within an organization and describes how that data transforms from one location or application to another. This activity highlights the internal and external nodes on which data is stored or processed, which enables the discovery of any data misuse.
Organizations should leverage data owners’ and network teams’ knowledge to form a comprehensive data flow map. This map can also identify data flows where the data is not properly encrypted. In cases where data is not encrypted in transit, the data senders should enable end-to-end encryption where possible or leverage virtual private networks (VPNs) —or equivalent encrypted tunnels and protocols —to protect the data in transit.
Macro segmentation provides high-level control over traffic moving between various areas of an organization’s network by breaking up a network into multiple discrete components with each supporting a different security requirement. In other words, macro segmentation can be thought of as the separation of sub-organizations within a company.
Moving over to micro segmentation, the document outlined that it provides security at a granular level by breaking down a portion of the network into smaller components to limit how data flows laterally through strict access policies. Microsegmentation can be thought of as the network separation within a sub-organization; employees in the same department should not have access to each other’s resources unless explicitly required. This provides for additional security enforcement closer to applications and resources, augmenting policies already established at the network perimeter.
SDN offers unique advantages in terms of granularity through micro segmentation, adaptability, and centralized policy management. Integrating SDN components into existing infrastructure also can enable customizable security monitoring and alerting.
Though microsegmentation can be achieved with traditional system components and manual configuration, the centralized nature of SDN allows for dynamic implementation and management across the network. SDN enables the control of packet routing by a centralized control server via a distributed forwarding plane, provides additional visibility into the network, and enables unified policy enforcement.
To mature the network and environment capabilities, an organization should map data flows based on usage patterns and operational business requirements, and properly segment the network at both the macro and micro levels. For centralized control and automated tasking, use SDN where it is available and practical to do so and automate security policies to gain operational efficiency and agility. They also call for the use of risk-based methodologies to define access rules that include mechanisms to ensure malicious or unauthorized traffic is dropped before reaching network resources at the perimeter, macro, and micro boundaries.
The NSA is actively assisting DoD customers in piloting ZT systems, coordinating activities with existing NSS and DoD programs, and developing additional ZT guidance to support system developers through the challenges of integrating ZT within NSS, DoD, and DIB environments. Upcoming guidance will help organize, guide, and simplify the incorporation of ZT principles and designs into enterprise networks.
Last October, the NSA, in collaboration with the CISA and industry partners, published a cybersecurity technical report (CTR). The NSA-CISA document guides identity and access management (IAM) to developers and vendors of multi-factor authentication (MFA) and single sign-on (SSO) technologies with actionable recommendations to address key challenges in their products.










