Comprehensive Guide to Integrated Operations (Part 4)

Network and OT Cyber Security Requirements: ICT for Integrated Operations
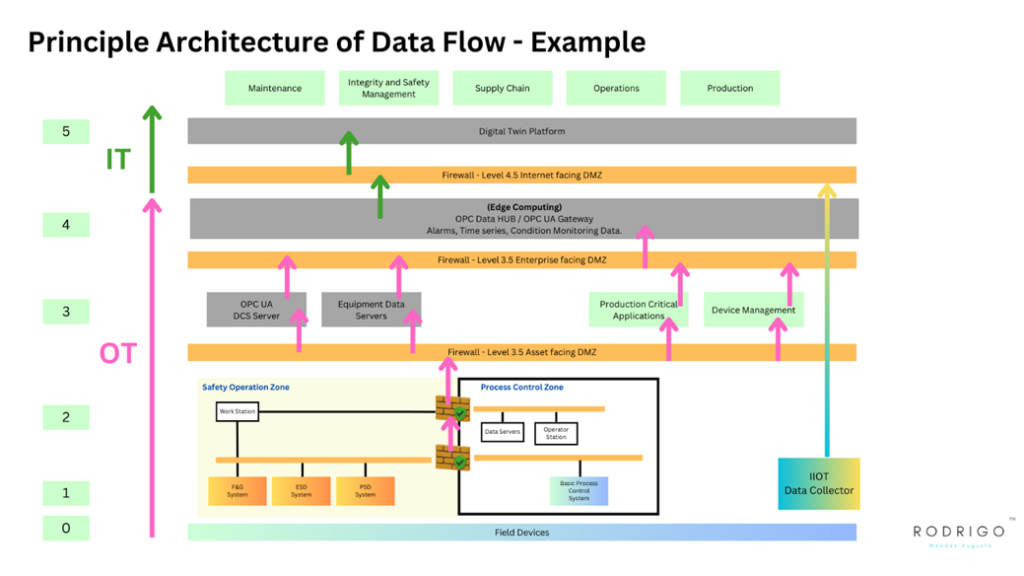
In Integrated Operations, where Information and Communication Technology (ICT) is pivotal in connecting and automating industrial processes, ensuring robust network and Operational Technology (OT) cybersecurity is crucial. This section delves into the detailed requirements to safeguard these interconnected environments against cyber threats, ensuring operational integrity, safety, and continuity.
Network
Network Segmentation and Access Control
Segmentation: Implement strict network segmentation policies to separate OT networks from IT networks and further divide the OT network into distinct zones based on the criticality and function of the systems. This minimises the attack surface and restricts the lateral movement of potential threats.
Access Control: Employ stringent access control measures, including role-based access controls (RBAC), to ensure that individuals and systems have access only to the resources necessary for their specific roles. Multi-factor authentication (MFA) should be mandated for accessing critical systems.
Firewalls and Intrusion Detection Systems (IDS)
Firewalls: Deploy stateful firewalls at critical network boundaries to monitor and control incoming and outgoing network traffic based on predetermined security rules. Application-level firewalls (next-generation firewalls) should be used for deeper inspection and control.
Intrusion Detection and Prevention Systems (IDPS): Implement IDS/IPS solutions to monitor network and system activities for malicious actions or policy violations. These systems should be capable of real-time analysis and immediate response to mitigate threats.
Secure Remote Access
In light of increased remote operations, secure remote access solutions are essential:
Virtual Private Networks (VPNs): Use robust encryption protocols to secure remote connections. Ensure that VPN gateways are fortified with multi-factor authentication and are regularly updated.
Remote Access Policies: Define and enforce strict policies for remote access, including using secure, dedicated devices and continuously monitoring remote connections.
Patch Management and Vulnerability Assessment
Patch Management: Establish a comprehensive patch management program to regularly update OT and network devices with the latest security patches—Prioritise patches based on the systems’ criticality and the vulnerabilities’ severity.
Vulnerability Assessments: Conduct regular vulnerability assessments and penetration testing to identify and remediate potential security weaknesses in the network and OT systems.
Security Monitoring and Incident Response
Security Information and Event Management (SIEM): Deploy SIEM systems to aggregate, correlate, and analyse security-related data from various sources, providing real-time visibility into potential security incidents.
Incident Response Plan: Develop and maintain an incident response plan tailored explicitly to OT environments. This plan should include containment, eradication, recovery, and post-incident analysis procedures.
Cybersecurity Awareness and Training
Awareness Programs: Implement ongoing cybersecurity awareness programs for all personnel, emphasising the unique challenges and responsibilities associated with OT security.
Specialised Training: Provide IT and OT staff training on cybersecurity practices and tools relevant to industrial control systems.
Data Protection and Encryption
Data Encryption: Apply strong encryption standards to protect sensitive data in transit and at rest, including operational data, personal information, and intellectual property.
Data Integrity Protection: Utilise mechanisms such as digital signatures and checksums to ensure the integrity of critical data and prevent tampering.
Compliance and Standards
Regulatory Compliance: Ensure compliance with relevant industry regulations and standards, such as NERC CIP for the energy sector, GDPR for data protection, and ISA/IEC 62443 for industrial cybersecurity.
Best Practices and Standards: Adhere to cybersecurity best practices and frameworks, such as the NIST Cybersecurity Framework, to guide the development and implementation of security measures.
Supply Chain Security
Vendor Risk Management: Assess and manage the cybersecurity risks associated with third-party vendors, ensuring they adhere to the same security standards and practices.
Software Integrity: Verify the integrity and authenticity of software and firmware updates, especially those provided by third-party vendors, to prevent the introduction of malicious code.
By addressing these comprehensive network and OT cybersecurity requirements, organisations can significantly enhance the resilience and security of their integrated operations against the evolving landscape of cyber threats. This robust security posture protects critical infrastructure and supports the reliability, efficiency, and innovation of industrial processes within the ICT framework.
Conclusion: Ensuring Robust Security and Efficiency in Integrated Operational Technology Environments
In the dynamic and interconnected world of Operational Technology (OT) and Information and Communication Technology (ICT), integrating systems and processes has unlocked new operational efficiency, productivity, and innovation levels. However, this integration also presents complex challenges, particularly in data flow, system integration, and cybersecurity. Addressing these challenges is beneficial and essential for maintaining operational integrity, safeguarding critical infrastructure, and ensuring industrial operations’ continued success and resilience.
Holistic Approach to Integration and Security
Successfully integrated operations necessitate a holistic approach, combining robust information management, sophisticated data flow architectures, and stringent cybersecurity measures. This approach should encompass technological solutions, organisational policies, employee training, and a culture of continuous improvement and risk management. Organisations can develop more cohesive and effective strategies for managing their integrated systems by fostering a collaborative environment where OT and IT professionals work together.
Adaptive and Forward-Looking Strategies
Rapid technological advancement and the evolving landscape of cyber threats require adaptive and forward-looking strategies. Organisations must remain vigilant, continuously monitoring and updating their systems, policies, and practices to counter emerging risks. This includes embracing innovative technologies such as artificial intelligence, machine learning, and blockchain, which can offer new ways to enhance operational efficiency and cybersecurity.
Regulatory Compliance and Best Practices
Compliance with industry regulations and adherence to best practices are foundational elements of effective integrated operations. Organisations must stay informed about relevant standards, such as IEC 62443, NIST frameworks, and sector-specific regulations, and ensure that their operations align with these guidelines. However, compliance should be viewed not as an endpoint but as a baseline to build more comprehensive and tailored security strategies.
Investment in People and Processes
Ultimately, the success of integrated OT and IT environments hinges on the people who design, operate, and manage these systems. Investing in training and development programs to enhance the skills and awareness of all employees, from front-line operators to top executives, is crucial. Equally important is the investment in processes that support collaboration, knowledge sharing, and incident response, ensuring that the organisation can respond effectively to challenges and opportunities.
Building a Resilient Future
The journey towards fully integrated and secure OT and IT environments is ongoing and requires commitment, innovation, and collaboration. Organisations can navigate the complexities of modern industrial operations by addressing the detailed requirements outlined in this discourse—from data management principles and architecture to cybersecurity and network protocols. In doing so, they protect themselves against immediate threats and lay the groundwork for a resilient, efficient, and forward-thinking future.
In conclusion, as we continue to forge the path of integration in industrial operations, the focus must remain on creating not only technologically advanced but also robust, secure, and sustainable systems. Organisations can achieve operational excellence and a competitive edge in the rapidly evolving industrial landscape by prioritising comprehensive security measures, continuous improvement, and a holistic approach to integration.










