CISA publishes summary of response to comments for ZTMM update
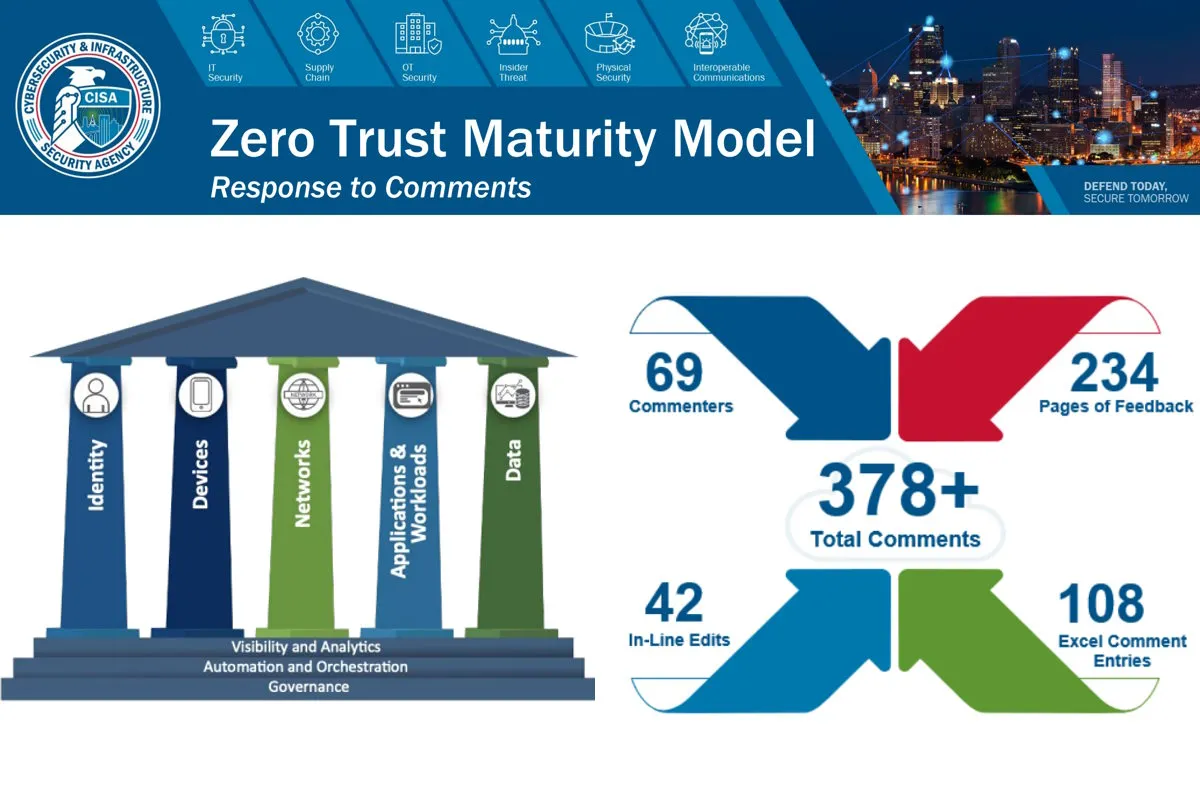
Apart from publishing Version 2.0 of its Zero Trust Maturity Model (ZTMM), the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a Response to Comments summarizing the comments and modifications in response to version 1.0 feedback, during the 2021 public comment period.
The summary said that the published update is a result of many different inputs, including comments gathered during the ZTMM V1.0 ‘Request for Comment’ period from September to October 2021. It also covered a review of Zero Trust Implementation Plans with the Office of Management and Budget (OMB), as required by OMB M-22-09. Additionally, it includes Inputs from CyberStat Working Groups, findings from National Security Telecommunications Advisory Committee (NSTAC) meetings, modernization deep dives, and individual one-on-one meetings with agencies, international partners, and the greater IT community.
Although the maturity model is not intended to be exclusionary, it does not address challenges specific to operational technologies, certain classes of Internet of Things (IoT) devices, or broadly incorporating emerging technologies, such as deception platforms, authenticated web application firewalls, and behavior analytics.
“CISA has been acutely focused on guiding agencies, who are at various points in their journey, as they implement zero trust architecture,” Chris Butera, technical director for cybersecurity at CISA, said in a media statement. “As one of many roadmaps, the updated model will lead agencies through a methodical process and transition towards greater zero trust maturity. While applicable to federal civilian agencies, all organizations will find this model beneficial to review and use to implement their own architecture.”
CISA issued a request for comment period for the ZTMM from Sept. 7, 2021, to Oct. 1, 2021, and collected 378 comments from agencies, vendors, consulting services, academic organizations, trade associations, individuals, and foreign organizations.
Version 2.0 of the ZTMM incorporates these recommendations, furthering the federal government’s continued progress toward a zero-trust approach to cybersecurity in support of the National Cybersecurity Strategy. While the ZTMM is specifically intended for federal agencies, all organizations should review this guidance and take steps to advance their progress toward a zero-trust model.
Recognizing that organizations begin their journey toward zero trust architectures from different starting points, the update to the ZTMM includes a new maturity stage called ‘Initial’ that can be used as a guide to identifying maturity for each pillar. In all four stages of maturity (Traditional, Initial, Advanced, and Optimal), CISA has also added several new functions and updated existing functions to consider when organizations plan and make decisions for zero trust architecture implementation.
The updated maturity model provides a gradient of implementation across the five distinct pillars to facilitate implementation, allowing agencies to make minor advancements over time toward the optimization of zero trust architecture. The five pillars of the ZTMM are – Identity, Devices, Network, Data, and Applications and Workloads.
Commenters requested additional guidance and space to evolve along the maturity model, the summary revealed. “In response, CISA added the additional maturity stage ‘Initial’ to the maturity model and realigned text for consistency across all pillars. CISA revised the guiding criteria for each stage to account for the new maturity model stage. These maturity stages are meant to be dynamic; planned progress from stage to stage may shift in scope over time,” it added.
The summary also identified that commenters also looked for updates to the longer-term ZTMM purpose. “In response to this, CISA updated the text preceding the model to reflect content updates and revised the purpose so the ZTMM is no longer a stopgap solution but continues to support agencies in designing and implementing their ZTA transition plans. The ZTMM has been aligned with OMB’s M-22 -09 ‘Moving the U.S. Government Toward Zero Trust Cybersecurity Principles’ (released January 2022) to include new and updated figures and highlight aspects of cybersecurity not included in the mode,” it added.
Commenters requested expanded content and guidance across all pillars and functions to provide more granularity to ZTA support implementation. In response to this, CISA revised the text for every function of the model, expanded and added functions for each pillar, and clarified the intent of cross-cutting pillars.
The CISA highlights notable changes in specific stages including identity, devices, networks, applications and workloads, data, and cross-cutting capabilities.
“Additional details provided in Authentication regarding ‘phishing-resistant MFA,’ including implementation of passwordless MFA via FIDO2 or PIV, the addition of flexibility with Identity Stores that emphasizes integration across self-managed and hosted identity stores, and addition of a new Access Management function for tailored access,” the summary pointed out. For devices, “Updated Policy Enforcement & Compliance function to address software and configuration management; revised Automation and Orchestration and Governance to include ‘deprovisioning,’ offboarding devices, and remediation steps for failure to meet posture requirements; and added Device Threat Protections function for centralized security management,” it added.
When it came to networks, the CISA summary pointed to a revised network segmentation function to promote micro-segmentation based on application profiles and added network traffic management function and network resilience function. Further revised pillar to incorporate elements of the original threat protection function into visibility and analytics, and expanded traffic encryption function.
The CISA summary disclosed that it updated the application access function to incorporate contextual information, enforce expiration conditions, and adhere to least privilege principles. It also revised application threat protections and application security testing to integrate protections into application workflows for real-time visibility and security testing throughout the software development life cycle.
The document also said it incorporated a new secure application development and deployment workflow function to formalize code deployment, restrict access to production environments, and promote a shift to immutable workloads. Renamed and revised application accessibility function to focus on making applications available to authorized users over public networks in alignment with OMB’s M-22-09.
The CISA summary delivers an expanded data encryption function to support encrypting data across the enterprise, formalize key management policies, and incorporate cryptographic agility. It also revised data inventory management and added data categorization function to address maturity toward inventoried and understood data types, and added data availability function to optimize availability and emphasize access to historical data.
The document added that visibility and analytics, automation and orchestration, and governance now include detailed scoping descriptions, pillar-independent paths to maturity, and updated recommendations across each pillar.
The commenters also shared feedback with CISA to clarify terms and concepts. In response, CISA included editorial edits, including adding and updating references, clarifying concepts throughout the ZTMM, and adding other general improvements to ensure consistency and improve flow.
Last month, the National Security Agency (NSA) published a Cybersecurity Information Sheet (CSI) that helps system operators mature identity, credential, and access management (ICAM) capabilities to mitigate certain cyber threat techniques. The initiative further discusses how these capabilities are integrated into a comprehensive zero trust (ZT) framework while providing system owners and operators the ability to identify, resist, and respond to various cyber intrusion techniques.










