BitSight research reveals almost 100,000 exposed ICS, enabling hackers to access, control physical infrastructure
Cyber risk vendor BitSight announced Monday new research which found that nearly 100,000 ICS (industrial control systems) owned by global organizations are exposed to the public internet. The research also identified that the exposed organizations span 96 countries and include several organizations. Additionally, the sectors with the highest concentration of exposed ICSs include education, technology, government and politics, and business services.
Hackers can exploit exposed ICS hardware to seize control over physical infrastructure, posing a global threat to businesses and communities, potentially including power grids, traffic light systems, security systems, and water systems. Such a severe attack has the potential to cause significant business disruption, threats to human safety, data and intellectual property compromise, and national security threats.
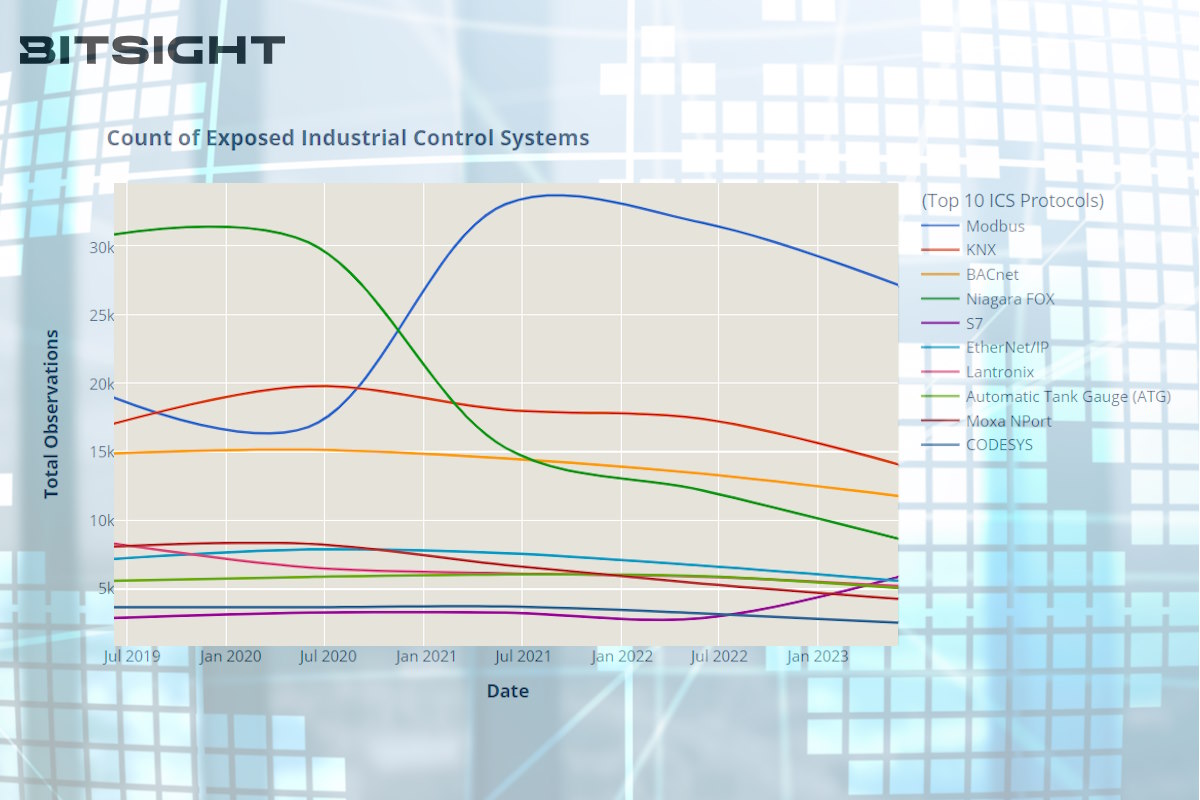
While Bitsight observed a steady decline in the number of internet-facing ICSs from 2019 to 2023, there remains a significant risk to organizations, their partners, and their constituents.
“Industrial control systems play a critical role in helping organizations avoid societal disruptions and the exposure of these devices is a serious matter,” Derek Vadala, chief risk officer at BitSight, said in a media statement. “This research shows that while the number of exposed ICSs is trending downwards, the overall threat level remains too high. An attack on just one ICS device would be a potentially catastrophic event that could have far-reaching consequences.”
BitSight disclosed in a blog post that “from 2019 to June 2023, we observed a decline in the number of ICSs exposed to the public internet. This is a positive development, suggesting that organizations may be properly configuring, switching to other technologies, or removing previously exposed ICSs from the public internet.”
To measure device exposure, BitSight identified exposed ICSs and mapped them to its inventory of global organizations. “Our analysis reveals that — contrary to industry norms — thousands of organizations are using ICSs directly reachable from the public internet, presenting a series of potential consequences of which private and public sector leaders should be aware.”
“While the aggregate number of exposed ICSs has been trending downward, we detected unique behavior on a protocol-by-protocol basis,” according to the BitSight report. “Exposed systems and devices communicating via the Modbus and S7 protocols are more common in June 2023 than before, with the former increasing in prevalence from 2020 and the latter more recently from mid-2022. However, exposed industrial control systems communicating via Niagara Fox have been trending downward since roughly 2021.”
Also, organizations should be aware of these changes in prevalence to inform their OT/ICS security strategies. “One of the first steps in mitigating OT risk is knowing where the risk is likely to lie.”
BitSight also detected that exposed ICS are spread across the globe, with notable concentrations of systems relying on specific protocols. “The geographic distribution of these exposed systems is important – private and public sector leaders should leverage this information to identify which protocols are most prevalent in geographies relevant to their operations, business or otherwise.”
“For example, organizations with operations in the United States and Europe may approach their strategy differently. Exposed industrial control systems using CODESYS, KNX, Moxa Nport, and S7 are largely concentrated in the European Union (EU),” the report identified. “Therefore, EU-based organizations — including government agencies and businesses — may opt to focus on these protocols first. Meanwhile, exposed systems using ATG and BACnet largely reside in the United States, likely warranting more acute attention from organizations based in or operating in the U.S.”
Bitsight found the top 10 countries by number of organizations having at least one exposed ICS (exposed organizations) are the U.S., Canada, Italy, the U.K., France, Netherlands, Germany, Spain, Poland, and Sweden.
To better understand ICS exposure, BitSight revealed where exposed organizations are headquartered, to which sector they belong, and the protocol used by the exposed device(s).
Recognizing the grave consequences of a potential attack on vulnerable ICS, BitSight recommends actions for security leaders, ICS manufacturers, and government policymakers.
For security leaders, organizations should immediately engage in outreach and remediation efforts to identify any ICS deployed by the organization and/or third-party business partners, and promptly assess the security of these systems. They must also remove any ICS from the public internet, and employ safeguards like firewalls to protect against unauthorized access to your industrial control systems. Additionally, security leaders must acknowledge the unique control needs that apply to OT, including ICS, rather than just apply a traditional IT risk model to this infrastructure.
ICS manufacturers and other OT technology must take action to increase the cybersecurity of their devices. This includes improving device security before deployment and working with clients to ensure the proper configuration and security of already deployed devices. Some manufacturers are leading with innovative initiatives to improve the security of their devices and their customers.
For example, Schneider Electric has made device security and customer security a business priority. Through a joint effort with BitSight, Schneider Electric is working to identify externally observable risks to the OT community and engage customers in remediation initiatives. Manufacturers should follow Schneider Electric’s lead and take steps to use secure-by-design principles to develop more secure technology; improve the security posture of deployed equipment and machinery by leveraging data and insights; and build programs to accurately and swiftly detect misconfigured or otherwise exposed systems.
BitSight identified that the exposed systems identified in this research should alert policymakers to the current state of ICS — and more broadly, OT — security. Due to the potentially serious consequences resulting from incidents involving industrial systems, policymakers should understand the risks of exposed ICS, particularly those involving critical infrastructure.
They must also inform national security strategies and programs to include adversarial threats targeting OT, and how an industrial cyber attack could impact national security and human safety; and quantify the impact — financial and otherwise — that a cyber attack targeting industrial infrastructure could inflict on national, regional, and local economies as well as diplomatic relationships.
Last week, the National Institute of Standards and Technology (NIST) published the third revision of NIST SP 800-82, with updates focusing on the expansion in scope from industrial control systems (ICS) to operational technology (OT); updates to OT threats and vulnerabilities; and updates to OT risk management, recommended practices, and architectures. The NIST SP 800-82r3 document provides OT asset owners and operators with updates to current activities in OT security; and updates to security capabilities and tools for OT.










