Operational Technology (OT) Network IDS is Dead. Long Live the AirGap!

As someone involved in building solutions for Operational Technology since the late 90s, I’ve had the opportunity to witness various approaches to securing OT and Critical Infrastructure. It has been an enlightening journey, and I take pride in my commitment to learning about the industries and people I serve in order to help them develop effective security strategies for their environments.

Throughout history, physical operations have required protection and maintenance due to the inevitable human element and the transition from an agrarian to an industrial society. Mechanical water systems, which are physical in nature, have been constructed for centuries to meet operational needs. We have witnessed multiple industrial revolutions that introduced new technologies aimed at improving manufacturing processes and enhancing the quality of life for individuals.
Understanding this historical context is essential because, despite the feeling that we are dealing with something entirely new, we are actually within a cycle that humanity has experienced several times over the past few centuries. Reflecting on the past and learning from it enables us to comprehend our present journey and gain insights into future directions.
Looking back, we observe that operations have always been engineered and separated based on their specific purposes and required outputs. In production plants, cell area zones have traditionally been established to ensure operational resiliency. Systems were air-gapped by default since, prior to the advent of the internet, there was no connectivity between sites or, for the most part, between processes.
Operations have always been grounded in the physical world, governed by the principles of engineering and physics. Although I am not an expert in physics or physical equipment, I acknowledge that before computerization in the 1970s, production plants were safeguarded through physical means. Process engineers always engineered solutions to protect physical equipment from damage.
As the industrial revolution progressed, engineers gradually incorporated computerization to enhance operational efficiency. The introduction of the first Programmable Logic Controller (PLC) in 1969 allowed us to utilize software and PLCs to control physical processes. It is important to note that this evolution occurred alongside the use of physical safety systems.
Throughout the industry’s history, safety, availability, and resiliency have been paramount, with human life considered more valuable than any system output. While I won’t delve into every industrial revolution, I want to emphasize that engineering for specific purposes has been instrumental in driving industry advancements and achievements.
In the early 2000s, as systems became interconnected through networking, intranets, and the internet, the need for cybersecurity became evident to industries operating OT (then not always called OT but referred to as ICS or SCADA systems). They sought out security solutions but couldn’t find anything specifically engineered for their purposes. As a result, they resorted to using off-the-shelf hardware and software solutions designed for IT systems.
In my experience, we initially implemented segmentation, incorporating firewalls at the edge of the operational network to separate OT systems from IT. The risk to operations has always been associated with IT and the physical world. Operators often distrust IT for various reasons, primarily because IT is not engineered for their specific needs. IT has typically attempted to cater to everyone and often believed it was the core of the business, imposing its ideals on operations.
To address the lack of specialized OT security solutions, several vendors emerged in the early 2000s, originating from OT backgrounds. These vendors focused on different aspects, such as operational risk management, process segmentation, and research on protocol inspection. They shared a commonality: their roots in operations and an understanding of engineering processes enabled them to design solutions by OT practitioners for OT practitioners.
Many of these early pioneers remain influential figures in the industry today, including Brian Ahern, Andrew Ginter, Dale Peterson, and Eric Byres. Looking into their backgrounds provides valuable insights into where we have been and helps us understand the present and future perspectives, they offer based on their extensive experience in OT security.
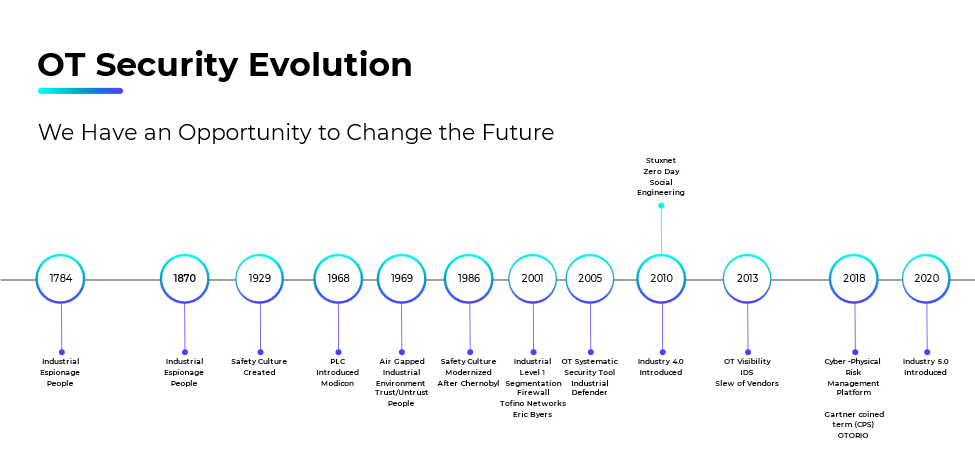
In 2011, the concept of Industry 4.0 emerged from a high-tech strategy project by the German government. It is no surprise that Germany, a longstanding leader in manufacturing, played a significant role in promoting these concepts. Industry 4.0 focuses on computerizing manufacturing processes and introduces process sensors to facilitate predictive maintenance analytics. While Industry 4.0 emphasizes the utilization of new data sources, it also emphasizes leveraging existing data and interconnecting systems for improved operational efficiency.
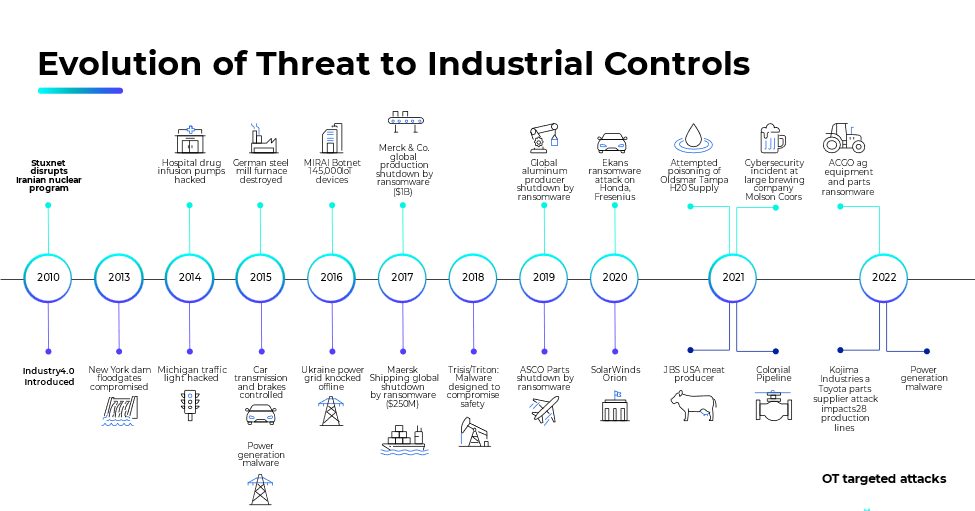
Industry 4.0 advocates for agile business models designed to adapt to change, making the associated risks in deployed Industry 4.0 environments constantly shifting. This fluidity necessitates careful consideration when selecting technology, as we operate in a world of perpetual change. Continuous risk monitoring should replace the outdated snapshot-in-time approach of past threat risk analyses. Our focus should be on reacting to present conditions rather than dealing with historical environmental factors. This fundamental shift is one reason why Network IDS is no longer viable; it is a reactive rather than a proactive solution.
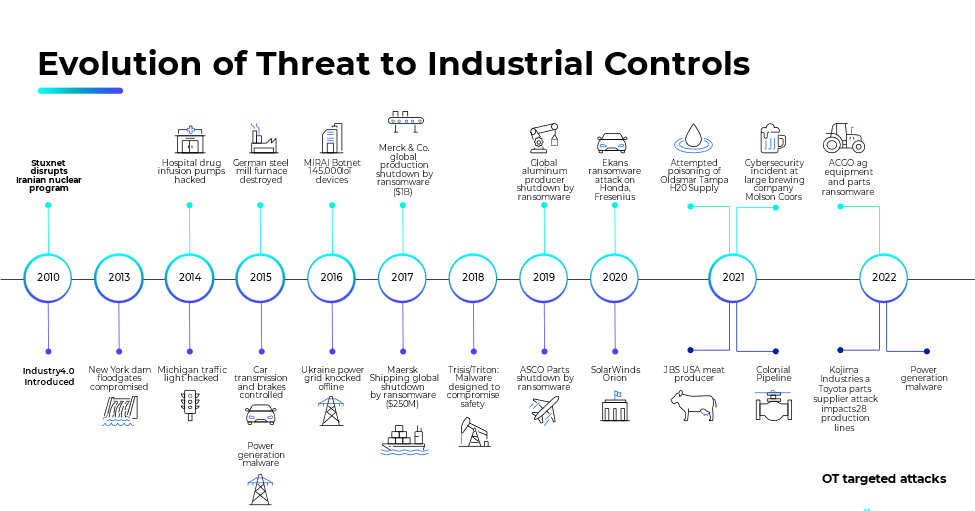
Discussions often revolve around active controls versus passive inspection, and customers prefer solutions that do not actively modify OT environments. When the term “proactive solutions” arises, people may misinterpret it as being “active” in the traditional sense. Passive solutions, such as IDS that require extensive tuning to the environment, often generate excessive alert noise, leaving administrators frustrated and overwhelmed. On the other hand, proactive solutions enable administrators to understand the environment’s exposure, take action to modify configurations, and reduce the attack surface. This allows them to comprehend relevant alerts and gain insights that go beyond mere volume, pinpointing specific actions required to enhance security while minimizing the attack surface. Effective communication is crucial in conveying this distinction; otherwise, the subtleties of the point may be lost. Moreover, since IDS solutions typically rely on network traffic and protocols to identify devices, asset precision can be compromised depending on the protocol being inspected. Customers require a reliable asset inventory, and network-based approaches often fall short in providing the required fidelity. To address this, the evolution of OT security necessitates leveraging multiple data sources to enhance asset information fidelity while building contextual awareness of asset interconnections and their potential impact on business operations in case of compromised security measures leading to production outages.
I have always held the belief that security technologies are cumulative, meaning that as new technologies emerge, we build upon existing ones rather than discard them. We add new technologies incrementally to bolster the overall security posture. However, with the current landscape boasting thousands of security vendors, each offering a multitude of choices that are not necessarily cumulative in nature, I find myself reevaluating this strategy. Clients require clear choices when constructing their security programs, posture, and contextual awareness across not only their operations but also their enterprise cyber and cyber-physical systems.
There are basic security needs that every client must address, and technologies catering to these needs are inherently cumulative. We all require a foundational set of measures. However, beyond these fundamental controls, today’s landscape necessitates selective deployment of technologies tailored to each client’s unique environment. Simultaneously, it is crucial to align these technological choices with the basic security controls to comprehend risk exposure, take actions to mitigate risk, and apply appropriate controls to address vulnerabilities in systems, processes, product lines, and cell areas. This approach also involves establishing robust zones and conduits, as the systems gain contextual awareness of assets and their interdependencies, enabling configuration improvements for protocols, firewall policies, network ACLs, PLCs, RTUs, IEDs, and their control masters.
The demise of IDS can be attributed to customers recognizing its lack of value in solving their operational security challenges. Market guides have shifted from emphasizing visibility to focusing on cyber-physical system security and risk management. This change is driven by the realization that these systems offer the best return on investment, maximizing the value derived from existing tools deployed to mitigate risks within their environments.
In conclusion, I declared, “Long live the AirGap” in the title. While the traditional physical air gap may have been prevalent in the past, modern environments still require segregation, albeit in a logical manner. We achieve this by utilizing tools such as data diodes for one-way communication gateways, firewalls, ACLs, and zero trust principles for user authentication, authorization, and segmentation of the attack surface using various technical methodologies. These measures allow us to establish zones and conduits controlled by policy, essentially creating a virtual segmented air gap. This approach offers greater flexibility by providing controls not only in the North-South direction but also in the East-West direction within our operations. The modern version of the air gap is more sophisticated but still exists. Long live the AirGap.
Some may argue against this statement, as a true air gap implies no communication whatsoever. However, in the context of modern applications that require connectivity and communication, we must adapt the principles of an air gap to contemporary terms.
The OT security market is ripe for a shake-up, and I believe we are currently in the midst of it. We will witness vendor consolidation, rationalization of valuations for OT security providers, and the introduction of new concepts aimed at meeting the demands of discerning modern buying committees.