First Impressions and Lasting Insights from an S4 Rookie

I must confess, somewhat sheepishly, that this year marked my inaugural visit to S4. Despite previous intentions to attend, various obstacles, including the challenges posed by COVID-19, have prevented my participation until now. I extend my deepest gratitude to Dale Peterson, the visionary founder and dynamic force behind the S4 community, for orchestrating such a compelling event.
S4 is not a gathering for the faint-hearted. At first glance, it might resemble a blend of an extended family reunion or a gathering reminiscent of the “Friends” TV show cast, with everyone seemingly enjoying the camaraderie, but don’t be fooled — this event is an intense and immensely rewarding marathon of work spanning 3-4 days. I anticipate it will take me several weeks to fully digest and understand all the insights and knowledge I’ve gained from both the formal presentations and the invaluable informal discussions with industry leaders.
This conference stands alone in its ability to gather such a high caliber of practitioners and thought leaders, all generously sharing their expertise with the singular aim of advancing our community and industry. The atmosphere is remarkably open and welcoming; whether you’ve dedicated 20 years to industrial automation or are newly intrigued by the field, the willingness of participants to offer advice and share knowledge freely is truly exceptional.
Dale suggests that S4 may not cater to everyone, a notion with which I have mixed feelings. Certainly, newcomers might be overwhelmed by the technical intricacies of some sessions, and vendors in search of business opportunities could leave feeling somewhat disillusioned.
In my conversations with several newcomers (asset owners) attending for the first time, many expressed initial reservations about their technical fit for the event. Remarkably, they each discovered aspects within the sessions and discussions that resonated with them, providing a gateway to grasp and navigate through wider subjects. From automation professionals exploring cybersecurity for the first time to IT and cybersecurity experts who had never set foot on a production floor, attendees found ways to connect with the material, likely leaving more informed and confident in charting a path forward for themselves and their organizations.
Dale’s opening keynote, emphasizing the significance and impact of belief on success, reflects the essence of this gathering. It’s the diversity of professional backgrounds, united by a shared humility and spirit of inclusivity, that characterizes this unique community. While S4 has commendably spotlighted the importance of gender diversity through its Women in ICS initiative, the industry’s pursuit of broader diversity remains an ongoing challenge, with much work still ahead.
Danielle Jablanski, a Non Resident Fellow at the Atlantic Council eloquently highlighted a notable disparity within the industry and broader society: the existence of double standards and inequities, especially in professional expectations and resource distribution among organizations. She emphasized how smaller, resource-limited organizations are frequently left most exposed. This point resonated deeply with me, as it seems the industry, including vendors and System Integrators, primarily targets the top tier of the pyramid, often neglecting the more vulnerable and less financially appealing segments. This oversight not only reflects a significant issue within our industry, aiming to protect and secure but also mirrors broader societal challenges when it comes to ‘defending civilization.’
In the opening keynote, Dale emphasized the common belief in OT security that defenders must be perfect to prevent attacks, highlighting how this belief sets an unrealistic standard and contributes to stress and a sense of futility among professionals. He went on to call for a shift in how success is measured in OT security, advocating for metrics and stories that highlight successes rather than focusing solely on failures or the need for perfection.
Dale called on the S4 community to redefine what success means in OT security, moving away from fear, uncertainty, and doubt (FUD) and towards a more balanced and realistic assessment of risks and achievements.
For me, this represents a sign of maturity in an industry that is still navigating its path and identity, a process inherent to its evolution. Some believe that, in the long term, there isn’t a distinct OT cybersecurity market.
Ted Gutierrez, CEO of SecurityGate, discussed the challenges of accurately defining the Total Addressable Market (TAM) for OT cybersecurity. As an analyst covering this market, this is a conundrum I know all too well, and it’s a question frequently posed to me by both investors and vendors. Ted raised doubts about the market’s size being as extensive as some projections suggest, highlighting potential implications for investment strategies and expectations for market expansion.
Others argue that the unique needs and focus of industrial organizations necessitate a distinct OT cybersecurity market. Ultimately, only time will reveal the outcome.
Reflecting on our market coverage over the last 7-8 years, it’s evident that this period, though relatively brief, has witnessed a couple of cycles of consolidation and acquisitions. Concurrently, there’s been a surge of new startups and service providers entering the scene.
However, there have also been phases where adoption seemed to hit a plateau, especially among early adopters and even as it began reaching the early majority. This was particularly noticeable during times when vendors primarily emphasized visibility, without clearly demonstrating value.
I find myself in strong agreement with Ted’s emphasis on the necessity for cybersecurity solutions to be closely aligned with operational needs, encompassing safety, reliability, and profitability. Again, this reflects the ongoing journey and maturation of our industry.
Here’s a snapshot of the top 5 speakers and presentations I attended, in no particular order:
1. Autonomous AI – The New Environment You Will Need to Secure
Kence Anderson, CEO Composabl

Anderson delved into the realm of autonomous AI, detailing its creation, application, and the security implications associated with its deployment in operational environments. The presentation focused on how to effectively bridge the gap between the theoretical potential of autonomous AI and its practical implementation in operational settings, underlining the importance of collaboration between engineers and security professionals to harness AI’s benefits while mitigating risks.
Key highlights included:
Autonomous AI Development – Anderson emphasizes that autonomous AI, capable of making strategic decisions in complex environments, will be developed by engineers, not materialize from conscious AI systems or emerge from tech company silos. He stresses the importance of engineering expertise within organizations for the creation of autonomous AI.
Autonomous AI in Manufacturing – Anderson discussed the autonomous AI system developed for PepsiCo to optimize Cheetos production. The AI system improves product consistency by learning from and assisting human operators, showcasing the beneficial collaboration between AI and human expertise.
Sanderson outlines five “Superpowers” that autonomous AI brings to industrial and operational technologies:
- Perception: Enhancing decision-making through advanced sensory data analysis.
- Learning: Gaining expertise through practice and feedback.
- Strategy: Applying tactics based on environmental conditions.
- Forward Planning: Considering future outcomes to make decisions.
- Deduction: Intuiting unmeasured variables from experience.
Security Considerations for Autonomous AI – Anderson highlighted the need to secure autonomous AI systems, particularly in areas like perception, which can be susceptible to manipulation. He advises on securing the control loop, considering communication pathways (cloud vs. edge infrastructure), and selecting appropriate levels of autonomy for AI deployment.
AI Deployment and Safeguards – Anderson stressed the importance of embedding safety checks and safeguards into autonomous AI systems, akin to those used for human operators. He advises on structuring AI with a perception layer for data analysis and a skills layer for decision-making, emphasizing the need for collaboration between security professionals and other subject matter experts to ensure effective deployment.
Engagement with Autonomous AI – Anderson encourages security professionals to take a proactive role in the design, implementation, and deployment processes of autonomous AI to maximize its benefits and ensure ROI. He concludes by offering his book as a resource for understanding and designing autonomous AI systems.
2. Priority Is in The Eye of The Asset Owner

Danielle Jablanski, a Non Resident Fellow at the Atlantic Council
Danielle’s presentation was really a call to action for the cybersecurity community to rethink how we prioritize and address threats in a way that is inclusive, equitable, and effectively reduces risk across all sectors of critical infrastructure.
Key highlights included:
Double Standards and Inequities – Danielle began by highlighting double standards within the industry and society, particularly noting disparities in professional expectations and resource allocation among organizations. She points out that smaller, resource-constrained organizations are often the most vulnerable.
The problem of Prioritization – Danielle addresses the difficulty in prioritizing critical systems due to the interconnected and essential nature of various infrastructures. This complexity is exacerbated by the inability to define what constitutes an OT incident clearly.
Exercise with Water ISAC – Danielle described the exercise she conducted with the Water Information Sharing and Analysis Center (Water ISAC) to apply her methodology for prioritizing cyber threats. This method involves stakeholders in discussions to rank scenarios based on their potential severity, likelihood to cause public panic, and ability to overwhelm local response capacities.
Standardized Priority Score – A key outcome of her methodology is the development of a standardized priority score that allows for comparing and prioritizing different scenarios across sectors and regions. This tool can help focus resources and attention on the most critical vulnerabilities and threats.
Call for Elimination of Double Standards – Danielle urged the industry to work towards eliminating double standards in cybersecurity prioritization, advocating for a more equitable approach that considers the unique vulnerabilities and needs of each sector and organization.
Danielle reminded us all that cybersecurity is inherently subjective, with priorities determined by each asset owner’s unique perspectives and needs. The goal is to work collaboratively to reduce the severity and impact of potential incidents across the board.
3. Applying FAIR To OT
Justin Turner Director, Security and Privacy Practice Protiviti

Justin’s presentation outlined a structured approach to quantifying cyber risk, leveraging both specific and generalized data to inform cybersecurity strategy and investment decisions within OT environments. This process is critical for prioritizing actions based on financial impact and risk exposure.
Key highlights included:
Risk Quantification Process – starts with identifying a threat (e.g., nation-state, script kiddie) that uses a method (e.g., exploiting a missing patch) on one or more assets, leading to an impact on the organization. This process aligns with the FAIR (Factor Analysis of Information Risk) framework, which, like the NIST Cybersecurity Framework, allows for varying levels of maturity based on organizational needs and risk appetite.
Asset Definition Flexibility – Assets can be defined at different levels of granularity, from individual devices to entire manufacturing sites. Consistency in asset definition is crucial for meaningful risk comparison across sites.
Input Gathering for Risk Computation – Necessary inputs include vulnerabilities, controls, industry-specific data, and prior breach information. These inputs feed into Monte Carlo simulations to produce risk quantifications, offering a range of potential outcomes rather than a fixed value.
Importance of Data – While more data tightens the range of risk quantification, even limited data can provide a useful approximation of risk. This is pivotal for organizations that may not have detailed insight into every potential vulnerability or impact.
Data Sources for Quantification – Data sources include public breach information, internal outage and financial data, and industry benchmarks. This information is used to simulate various risk scenarios and quantify potential financial impacts.
Outputs and Decision-Making: Justin reminded us that the goal is to quantify cyber risk in financial terms to aid in prioritizing cybersecurity investments. Outputs from the simulations help identify where the organization faces the highest risk exposure, guiding resource allocation toward mitigating these risks.
4. Fireside Chat
Robert M. Lee, Co-Founder & CEO of Dragos

Always interesting to hear from Rob Lee. The conversation between Dale and Rob offered a sophisticated perspective on the present landscape of OT cybersecurity. It highlighted the importance of adopting strategic, knowledge-based defensive strategies, building the capacity to comprehend and react to security incidents, and underscoring the significance of foundational cybersecurity measures in safeguarding against a diverse array of threats.
Key highlights included:
Distinction between Deployed and Employed Malware – Rob emphasized the importance of understanding whether a malicious tool has merely been deployed for potential use or actually employed in attacking targets. The distinction helps in assessing the level of threat and urgency for response.
Visibility and Monitoring Challenges – Rob noted a significant issue in cybersecurity: the lack of comprehensive monitoring across the global infrastructure. It’s noted that less than 5% of the global infrastructure is effectively monitored, leading to a gap in understanding the full scope of threat activities.
Risk of Criminal Use of Advanced Malware – Rob expressed concern over sophisticated malware tools developed by state actors falling into the hands of criminal groups, which could lead to high-impact attacks on critical infrastructure.
Homogeneity and Connectivity in OT Systems – the discussion highlighted that as industries become more connected and standardized, the risk landscape changes. Systems across different sectors are becoming more similar, making them more vulnerable to scalable and reusable attack tools. Rob mentioned how adversaries are not just attacking randomly but are selecting strategic targets that could have significant impacts, emphasizing the need for organizations to understand and mitigate these targeted threats.
Importance of Basic Cybersecurity Measures – Despite the complexity of threats, Rob underscores the effectiveness of basic cybersecurity practices in preventing breaches, even against sophisticated state-sponsored attacks. He continued to touch upon the challenge of determining the right level of detection capabilities, reinforcing a risk-based approach to deciding how much to invest in detection technologies and processes. He also recommended that organizations are at different stages of cybersecurity maturity, and initially, they need to focus on basic controls and, as they advance, use detailed threat intelligence to refine and target their defensive strategies.
Call for Improved Capability to Identify Cyber Events – Rob issued a strong call for organizations to have the capability to determine the cause of incidents in their OT environments, distinguishing between cyber-attacks and other causes to appropriately respond and recover.
5. The Value of (and lack of) Detection at Various Stages In the Kill Chain
Joe Slowik, ATT&CK CTI Lead, MITRE
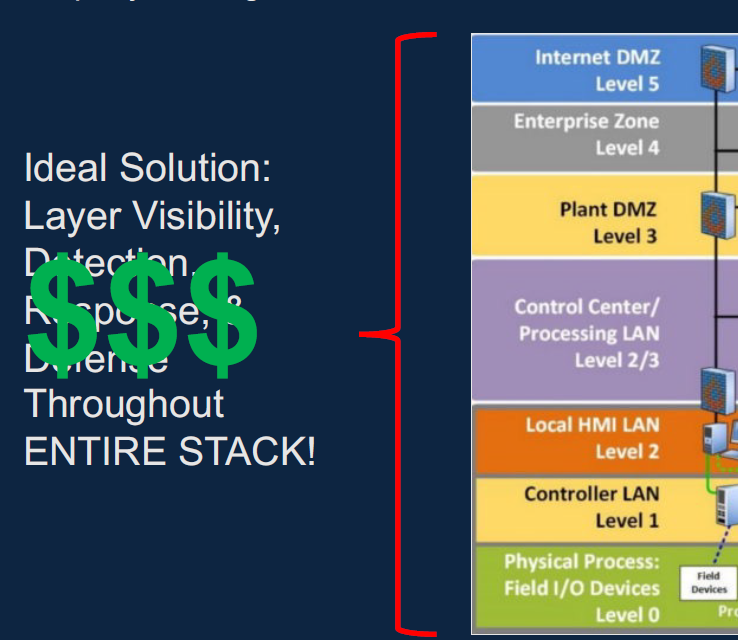
True to form, Joe impressed the S4 audience with the depth of content he managed to squeeze into his 30-minute slot. Joe advocated for a balanced, pragmatic approach to OT security that prioritizes early detection and effective response within the constraints of limited resources, while also considering the evolving technological landscape and its impact on security architecture.
Key highlights included:
Goal of OT Threat Detection – Joe reminded the audience that the main goal is to secure and prevent the loss of the ability to generate value, essentially protecting the organization’s mission and revenue generation capabilities against state-sponsored entities and ransomware attacks.
Defensive Strategy and Value Preservation – Joe noted that security’s core function is preserving and maintaining the ability for organizations to generate value safely. I wholeheartedly agree, and sometimes, this essential aspect is overlooked amidst the mayhem.
Detection and Response Perspective on Triton – Joes walked us through the Triton malware incident as a case study to discuss detection, emphasizing that early detection is crucial but also noting that detection alone is not sufficient for security—it must lead to effective response and recovery to ensure safety and prevent significant financial losses.
Challenges in OT Specific Detection – Joe acknowledges that OT-specific detection is hard and expensive, pointing out that not all organizations can afford a comprehensive detection and monitoring system across their OT environments.
Preventative vs. Post-Incident Response – Joe stressed the importance of early detection in the IT environment to prevent OT incidents. However, he also advocates for having a minimal level of data capture in the OT environment for forensic analysis and incident scoping if an intrusion occurs.
Resource Limitations and Prioritization – He noted that given the resource constraints most organizations face, the presentation suggests prioritizing detection and mitigation efforts where they can provide the greatest return on investment, focusing on preventing the most damaging incidents.
Pitfalls and Technological Trends: Joe acknowledged potential pitfalls, such as poor network design and the advent of new technologies like cloud-based OT systems, which can circumvent traditional security models.
Realistic and Practical Approaches: Joe. Much like Dale in the opening keynote, advised against striving for a perfect security solution, suggesting instead a pragmatic approach that aims for a substantial level of protection with the available resources. This approach involves leveraging IT-based defenses to prevent OT incidents and ensuring data capture for forensic analysis in the OT environment.
It’s important to note that the S4 community is incredibly welcoming to anyone who has a passion for OT cybersecurity. And I wanted to shout out to all the amazing folks I met or caught up with over the past week at S4, simply an amazing bunch of people.










