Emerging Trends and Securing the Future of Smart Manufacturing

Welcome to the ninth and final article of our series on manufacturing cybersecurity. This installment marks the culmination of our journey through the intricate and evolving landscape of industrial cyber protection in the era of Industry 4.0 and beyond. Throughout this series, we have navigated the complexities of cybersecurity in the manufacturing sector, a critical component of our global economy and our way of life.
As the manufacturing sector wholeheartedly embraces the digital revolution, the significance of robust cybersecurity and cyber risk strategies cannot be overstated. In this era of interconnected technology, people, and data-driven processes, the intertwining of cyber with manufacturing has become more pronounced. This final article aims to lay out one possible future, highlighting the dual necessity of enabling the business and its customers through productivity, reliability, and continuity, while concurrently protecting it through safety, security, and recoverability.
As we conclude this series, we hope that the insights provided will empower manufacturers to navigate the digital landscape with greater confidence and foresight. The future of smart manufacturing promises immense potential, and it is through proactive and comprehensive cybersecurity measures that this potential can be fully realized.
We’ve seen how this new industrial revolution is seriously changing the game, especially when it comes to cybersecurity in operational technology (OT) environments. For businesses, it’s not just about jumping on the Industry 4.0 bandwagon; it’s also about smartly navigating the risks and challenges that come with it.
Let’s break this down a bit:
Seeing Clearly and Weighing Your Options
Industry 4.0 is all about leveraging data, but here’s the catch – the more IoT and industrial IoT devices you have, the bigger the cybersecurity risk. Take the recent Clorox supply chain attack, for example. It highlighted some real headaches like business interruptions, safety issues, financial hits, and even dents in reputation. Businesses need to get savvy with their risk/benefit analysis, deciding what data and devices are essential for network connectivity. The idea is to connect only what you need, reducing the chances of cyber threats.
When IT Meets OT
Industry 4.0 is bringing IT and OT closer together, and with that comes more data and more risk. It’s crucial for organizations to get their IT and OT teams on the same page. They need to work together to build a cybersecurity strategy that covers all bases – one that understands and addresses the unique security needs of both worlds. It’s all about bridging that gap and making sure the entire network is safeguarded.

The Industrial CISO
With Industry 4.0, assets are no longer just in one place; they’re spread out, adding a whole new level of complexity to cybersecurity. Companies have to step up their asset management game. This means keeping track of every connected device and making sure they’re all secure. Regular checks for vulnerabilities, keeping software updated, and continuous monitoring are part of this package.
These challenges are indeed among the most complex and unique that an Industrial Chief Information Security Officer (CISO) and their team can face. It’s a whole new ballgame compared to safeguarding critical data in a near-impenetrable vault. Instead, they find themselves in the thick of securely sharing this data with “trusted” partners. This scenario brings into sharp focus the intricate balancing act of “secure enablement.”
Let’s expand on this:
The Art of Secure Collaboration
In today’s interconnected industrial world, data sharing is not just a convenience; it’s a necessity for growth and innovation. However, sharing data safely with partners, suppliers, or even within different departments of the same organization, requires a sophisticated approach to cybersecurity. The industrial CISO’s role evolves from just protecting data to enabling its safe and efficient flow across various networks, ensuring that it remains secure even when it’s outside their direct control.
Innovation and Risk Management
Innovation, especially in the context of Industry 4.0, naturally brings risks. But here’s the catch – innovation without risk is like swimming without getting wet; it’s just not possible. The key lies in understanding these risks – they can be accepted to a certain degree, actively mitigated, or in some cases, transferred (think insurance policies or outsourcing certain aspects). Ignoring these risks is not an option. Doing so is akin to flirting with the dark side, where the consequences can be severe and far-reaching.
A Proactive Approach to Cybersecurity
In this dynamic environment, the role of the industrial CISO is not just reactive; it’s increasingly proactive. This means anticipating potential security breaches and having robust strategies in place. It’s about understanding not just the technology, but also the human and process elements of cybersecurity. Training staff, developing a security-conscious culture, and keeping abreast of the latest threats and countermeasures are all part of this proactive stance.
Balancing Act between Security and Business Objectives
Finally, there’s the critical aspect of aligning cybersecurity strategies with broader business goals. It’s a tightrope walk – on one side, there’s the need for security and compliance, and on the other, the drive for innovation, efficiency, and profitability. The industrial CISO’s role is to find that sweet spot where security measures enable, rather than hinder, business objectives.
Boosting Safety and Security of Connected Technologies: OT, IACS, IIoT, and Cloud Systems
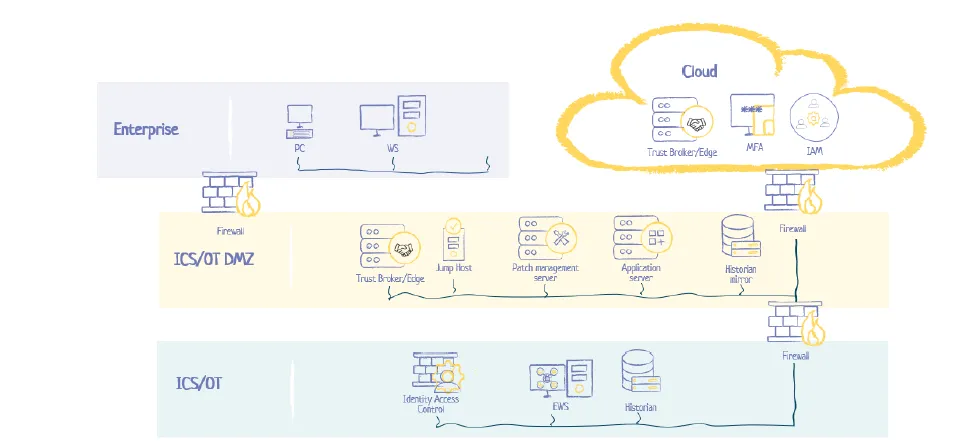
Securing the manufacturing sector’s interconnected technologies is not a one-and-done deal. It requires a comprehensive, multifaceted approach and a robust defense-in-depth strategy. This is the way forward for organizations looking to safeguard their interconnected tech effectively.
Best practices include:
- Testing Environments – With the complexity of IoT devices, edge computing, and digital twins, it’s a no-brainer to thoroughly test these technologies in a controlled setting before they go live. This step is not just about ticking a box; it’s about identifying potential vulnerabilities, fine-tuning security measures, and getting the configurations just right, all while ensuring your operations run smoothly.
- Securing MQTT Communications in IoT – Secure communication is the backbone of IoT’s functionality. Here, MQTT (Message Queuing Telemetry Transport) steps into the spotlight. It’s not just about using MQTT, though; it’s about fortifying it with solid encryption, stringent authentication, and tight access control. This way, the data flowing between your IoT devices stays confidential and tamper-proof.
- Digital Twin Best Practices – Digital twins aren’t just fancy digital replicas; they’re critical assets. Ensuring their security means strict access controls and robust encryption. A digital twin in the wrong hands is like giving away a treasure map to your operations. Therefore, it’s paramount to keep this data under lock and key, within safe domains.
- Defense-in-Depth Strategy – Think of this as a multi-layered security shield. It’s about having an arsenal of defenses like firewalls, intrusion detection systems, SIEM solutions, security gateways, data diodes, endpoint protection, and Identity and Access Management (IAM). This approach isn’t just about layering security measures; it’s about creating a resilient, adaptable defense system that’s ready for a variety of threats. By integrating these various measures, not only do you reduce the chances of successful attacks, but you also boost your detection, response, and recovery capabilities.
Actionable Steps for Enhancing Cybersecurity include:
- Agile Asset Inventory Tools – As OT and IIoT devices multiply, traditional manual and even passive asset inventories just can’t keep up. It’s time to invest in dynamic tools that continuously discover and monitor assets. This approach ensures every device is on the radar, minimizing the risk of sneaky vulnerabilities.
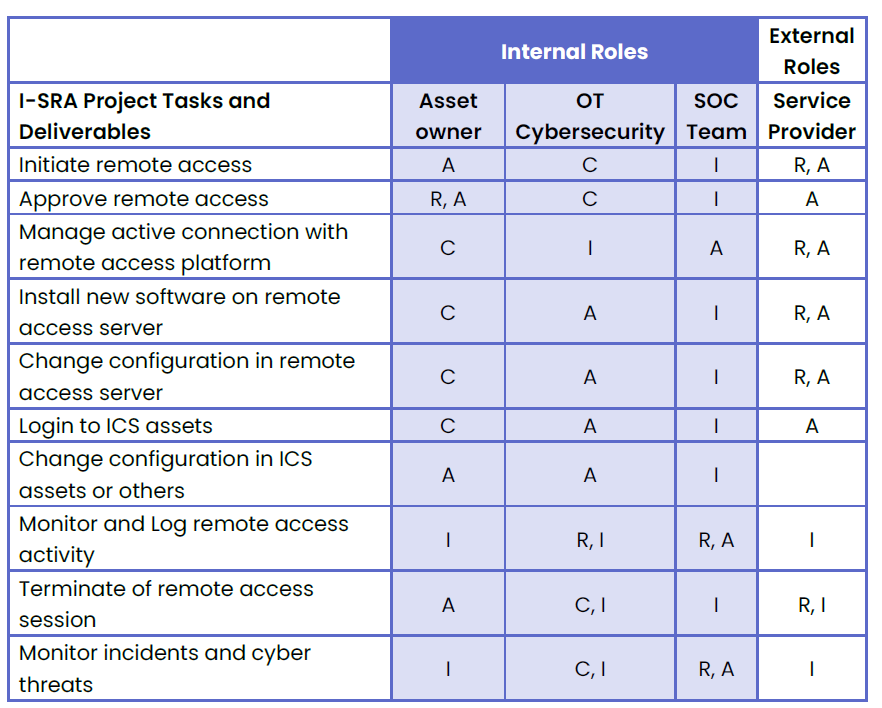
- Formal Documentation and Policy – Establishing well-documented cybersecurity policies and procedures is a foundational step. Having clear and consistently updated guidelines ensures that security measures are systematic and thorough. Incorporate a RACI (Responsible, Accountable, Consulted, Informed) model in each area to delineate roles and responsibilities. This structured approach not only facilitates regular audits but also ensures adherence to compliance standards and keeps you abreast of the evolving threats in smart manufacturing.
- Training and Awareness – Never underestimate the power of a well-informed workforce. Regular training programs keep everyone sharp about the latest cyber threats and the best security practices.
- Minimize Attack Surface – A key security principle is to shrink your attack surface. Implement access controls, segmentation, and other security measures to limit exposure. This not only reduces the impact of potential threats but also restricts the enemy’s movement within your network.
- Securing Data In and Out – Data security is critical, whether data is coming in or going out, at rest or on the move. Focus on deep encryption, vigilance against data exfiltration, and maintaining data integrity. Proper data handling is your shield against breaches and keeps sensitive information confidential.
Key Takeaways from the Manufacturing Cybersecurity Series – The Final Wrap-Up
At this crucial juncture in our increasingly digital industrial landscape, manufacturing organizations are grappling with a rapidly evolving cybersecurity threat. The integration of digital technologies and the interconnectedness of industrial automation systems have heightened the risk of cyberattacks, posing a significant threat to vital infrastructure – everyone’s infrastructure is critical to someone. These organizations must elevate industrial cybersecurity on their priority list.
The task at hand isn’t just about recognizing the urgency of prioritizing industrial cybersecurity. Manufacturing organizations must also confront the dual necessity of enabling their business through enhanced productivity, reliability, and continuity, while simultaneously safeguarding it through robust safety, security, and recoverability measures.
Tackling current challenges is important, but manufacturing organizations must also stay ahead of future threats in industrial cybersecurity. As technology races forward and cybercriminals grow more sophisticated, we can expect new vulnerabilities to surface.
To navigate these future risks effectively, the manufacturing sector must be proactive, investing in strong cybersecurity measures. This requires ongoing training and education, along with a readiness to adapt to the evolving threat landscape.
The message here is straightforward and urgent: cybersecurity in manufacturing isn’t a passive or reactive task; it’s an active, ongoing process. This involves regular risk assessments, identifying and mitigating vulnerabilities, and implementing robust security controls. Equally important is fostering a cybersecurity-aware culture throughout the organization, ensuring everyone from top executives to factory floor workers understands their role in maintaining security.
Collaboration is another critical component. By sharing knowledge and best practices with industry peers, government entities, and cybersecurity experts, manufacturing organizations can significantly enhance their collective defense. Such partnerships can also lead to the development of industry-wide standards and guidelines, strengthening the sector’s overall security posture.
The risks and consequences of cyberattacks on critical manufacturing infrastructure are too significant to be ignored. By internalizing the key insights presented, preparing for emerging challenges, and adopting best practices, these organizations can strengthen their defenses against cyber threats, securing their operations and contributing to the resilience of the broader industrial landscape.
In this context, the role of the Industrial CISO transcends traditional views. It’s about being a facilitator of business enablement, not a hindrance to innovation. The Industrial CISO must evolve into the ultimate diplomat, adeptly balancing the complexities of diverse technology and varied stakeholder interests – from the control room to the board room. Their focus should be on driving the business forward and serving customers, all while maintaining robust security measures.

In case you missed the previous installments:
- Part 1: Industrial Cybersecurity Manufacturing Cybersecurity in the Manufacturing
- Part 2: The Journey Beyond Industry 4.0 – Embracing Smart Manufacturing
- Part 3: Navigating the Manufacturing Threat Landscape
- Part 4: Cyber Risk in Manufacturing – A Closer Look
- Part 5: Cybersecurity Strategies and Best Practices for Manufacturing
- Part 6: Manufacturing Cybersecurity – Standards, Regulation and Compliance
- Part 7: Cyber Incident Management, Response, and Recovery in Manufacturing Environments
- Part 8: Manufacturing – Supply Chain Security










