Safeguarding IEC 61850 Implementation in Industrial Control Systems: A Technical Odyssey

Introduction: Navigating the IEC 61850 Cybersecurity Odyssey
In the intricate tapestry of Industrial Control Systems (ICS) and the ever-evolving landscape of Industrial Cyber Security, a singular standard rises above the rest as a beacon of modernization and innovation – IEC 61850. In the following pages of this technical article, we invite you to embark on an intellectual journey into the heart of IEC 61850’s implementation, with a laser-sharp focus on its most critical facet – Cybersecurity.

This is not a mere journey but an expedition into a realm where only the most adept and courageous engineers dare tread. Here, innovation becomes the compass guiding us forward, while security is our guardian against the perils lurking in the digital shadows. Our destination is where the past meets the future, legacy systems intertwine with cutting-edge technologies, and where the fate of industrial networks hangs in the balance.
The Magnitude of IEC 61850: A Linchpin of Modernization
As we embark on this journey, it is crucial to acknowledge the profound significance of IEC 61850. This international standard, initially conceived for the automation of electrical substations, has evolved into a linchpin that holds together the intricate machinery of modern industrial control. It serves as the architectural cornerstone upon which the digital transformation of critical infrastructure is built.
IEC 61850 transcends the boundaries of traditional communication protocols. It ushers in a new era, defined by a model-based approach that abstracts data models and services, then seamlessly maps them onto specific protocols like Manufacturing Message Specification (MMS), Generic Object-Oriented Substation Event (GOOSE), and Sampled Values (SV). This paradigm shift allows for unprecedented levels of interoperability and configurability, paving the way for enhanced efficiency and control in industrial environments.
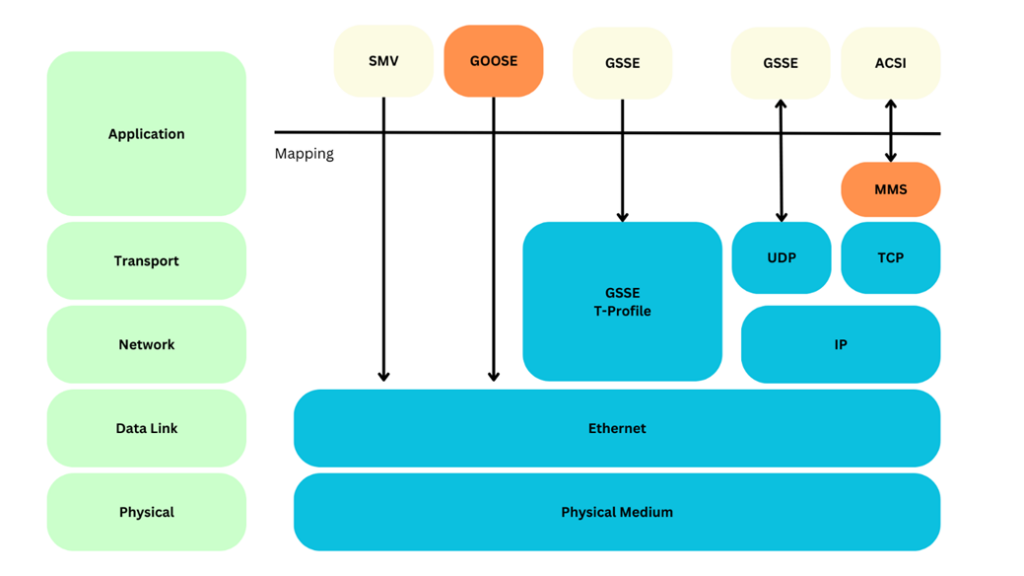
Our focus, however, is not solely on the marvels of IEC 61850 but on the nexus where innovation converges with cybersecurity. In a world increasingly marred by cyber threats, the security of industrial networks has become an imperative of the highest order. As such, IEC 61850’s journey is incomplete without a vigilant sentinel to safeguard its progress.
In this realm, engineers are tasked with more than technical mastery. They become the architects of digital fortresses entrusted with protecting critical infrastructure. IEC 61850’s successful implementation hinges on its ability to navigate the treacherous waters of cybersecurity. Together, they must craft a secure environment where data flows freely, real-time control is assured, and where the integrity of digital analogues remains uncompromised.
A Glimpse into the Odyssey Ahead IEC 6158
In the following words, I will delve into the technical intricacies of implementing an IEC 61850-compliant network, paying heed to the security measures underpinning its very existence. From advanced network segmentation to deploying intrusion detection systems, we will uncover the tools and techniques that enable engineers to safeguard the heart of IEC 61850 against external threats.
Our expedition will also navigate the challenges that engineers must confront along the way. These challenges include reconciling compatibility with legacy systems, achieving a delicate balance between interoperability and security, and configuring complex network settings that maintain the highest performance and safety standards.
As we set forth on this intellectual voyage, it is with the understanding that the fate of industrial networks hangs in the balance. The success of IEC 61850 and its integration with emerging technologies will define the future of industrial control. As engineers and guardians of this digital frontier, we are poised to lead the way, ensuring a secure passage through this uncharted territory.
So, fasten your seatbelts, for the journey into the heart of IEC 61850’s cybersecurity implementation is about to commence, and it promises to be an odyssey of unparalleled significance and impact.
Charting the Course for IEC 61850 Network Design: A Cybersecurity Odyssey
Our journey into the heart of IEC 61850 implementation takes us through technical challenges. Each step is a decisive move towards ensuring the utmost cybersecurity in Industrial Control Systems (ICS). Here, I outline in detail each leg of this cybersecurity odyssey.
Advanced Network Segmentation – Our Compass
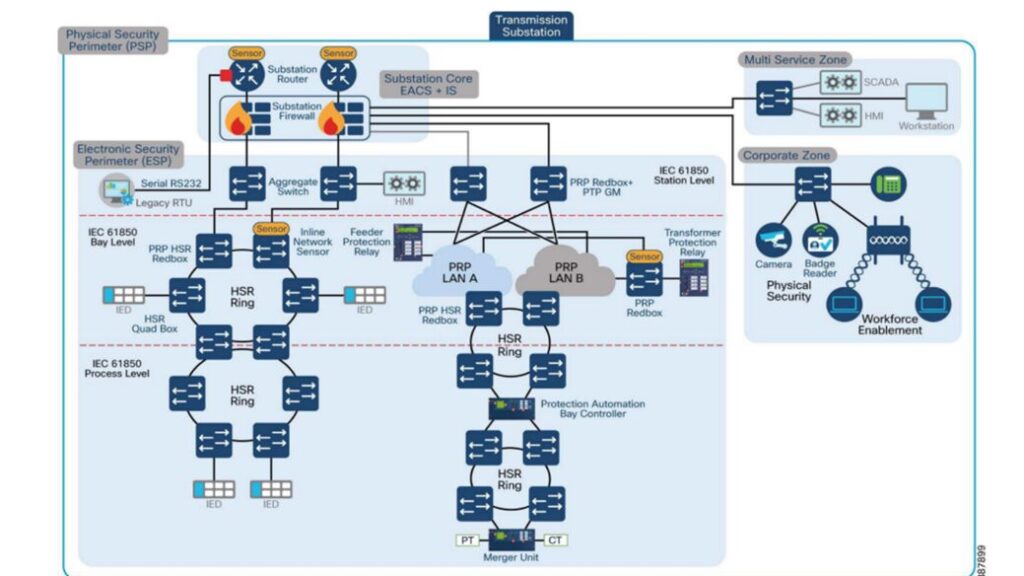
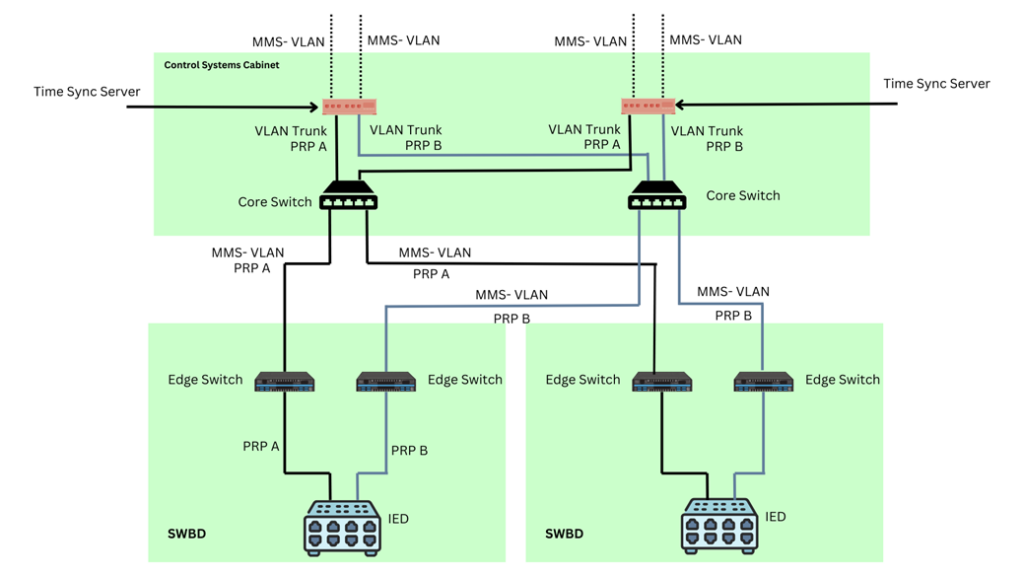
Our journey commences with the strategic deployment of advanced network segmentation techniques – VLANs and Multiprotocol Label Switching (MPLS). These tools act as our navigational compass, guiding us through the intricate IEC 61850 landscape. Their primary purpose is to create isolated layers within the network, a fundamental pillar of network security.
VLANs: Think of VLANs as road signs in our digital landscape. They allow us to separate traffic into logically distinct segments, ensuring that different types of data (MMS, GOOSE, SV) travel on separate roads, never intersecting. This isolation is a vital safeguard, as it limits the potential impact of security breaches.
MPLS: As we delve deeper, MPLS becomes our versatile route planner. It allows route traffic efficiently based on its priority and security requirements. It ensures that critical data flows through secure channels while maintaining network efficiency. In essence, MPLS ensures that our journey through the IEC 61850 realm is swift, safe, and precisely orchestrated.
Enhanced Security Protocols Implementation – Our Shield and Armor
As our expedition advances, we encounter IEC 62351, the security extension designed exclusively for IEC 61850. In this realm, it serves as our shield and armour, fortifying our defences against cyber adversaries.
TLS/SSL for Confidentiality and Integrity: Picture TLS/SSL as an impenetrable fortress surrounding our communications. It encrypts MMS traffic, rendering it unintelligible to prying eyes and ensuring its integrity during transmission. In a world where data confidentiality is paramount, TLS/SSL forms an unbreachable barrier.
Robust Authentication Mechanisms: Our armour against intrusion is fortified by robust authentication mechanisms. They ensure that only trusted entities can access our IEC 61850 network. These mechanisms demand the presentation of verifiable credentials, preventing unauthorized entry into our digital fortress.
Authenticity and Integrity of GOOSE and SV Messages: GOOSE and SV messages, crucial components of IEC 61850, are safeguarded by IEC 62351. This ensures that these real-time control and data transmission signals remain untampered and authentic throughout their journey, further fortifying the security of our network.
Device Hardening and Security Compliance – Our Mantra and Guiding Star:
As our odyssey takes us deeper into the heart of the IEC 61850 network, we arrive at the sanctuary of Intelligent Electronic Devices (IEDs). Device hardening becomes our guiding mantra in this sacred space, and compliance with security standards like IEC 62443 serves as our North Star.
Device Hardening: Device hardening is akin to fortifying the innermost chambers of our castle. It involves disabling unused ports and services closing off potential entry points for cyber adversaries. It also enforces unbreakable password policies, ensuring that only authorized individuals can access these devices.
Firmware Updates: Our devices require constant vigilance to remain resilient. Firmware updates, performed regularly, ensure that known vulnerabilities are patched and security is continually reinforced. In this ever-changing landscape, staying current with the latest firmware is our shield against emerging threats.
IEC 62443 Compliance: Our journey is underpinned by the unwavering commitment to compliance with IEC 62443 standards. This comprehensive framework is our guiding star, providing a roadmap to achieving robust cybersecurity in IEC 61850 networks.
In the upcoming sections of our odyssey, we shall delve further into the intricacies of implementing Intrusion Detection Systems (IDS), conducting network traffic analysis and monitoring, and designing for network resilience and redundancy. As we journey deeper into the heart of IEC 61850’s cybersecurity realm, we discover that the path ahead is both challenging and rewarding, offering insights and strategies to ensure the future security of industrial networks.
Delving into the Intricacies of IEC 61850 Network Security
As our cybersecurity odyssey continues, we approach the pivotal juncture where we explore the intricacies of implementing Intrusion Detection Systems (IDS), conducting network traffic analysis and monitoring, and designing for network resilience and redundancy. Each of these facets is a cornerstone in our quest to ensure that IEC 61850 networks stand as bastions of security and efficiency, safeguarding the uninterrupted operation of critical industrial systems.
Implementing Intrusion Detection Systems (IDS): The Sentinel of Vigilance
The deployment of “Intrusion Detection Systems (IDS)” is akin to placing vigilant sentinels at the gates of our digital fortress. IDS is a proactive defence mechanism that constantly monitors the IEC 61850 network for signs of intrusion or suspicious activity.
Intricacies: The key to effective IDS implementation lies in the precision of its configuration. Engineers must meticulously define rules and signatures that enable the system to identify abnormal behaviour and potential threats. These rules can be fine-tuned to recognize specific patterns in IEC 61850 traffic, such as deviations from normal behaviour or unusual command sequences. Furthermore, IDS systems should perform deep packet inspection to scrutinize network traffic content, providing a granular view of data exchanges. This level of detail is crucial for identifying subtle anomalies that could indicate cyber threats.
Conducting Network Traffic Analysis and Monitoring: The Discerning Eye
Network traffic analysis and monitoring are the discerning eyes that scrutinize every facet of IEC 61850 communications. They allow engineers to gain insights into the network’s health, efficiency, and security.
Intricacies: Effective analysis involves the use of advanced tools and techniques. Engineers deploy packet analyzers that dissect the structure of IEC 61850 packets, ensuring they adhere to the standard’s specifications. They also examine the timing and sequencing of GOOSE frames, MMS requests, and SV messages to detect any irregularities that may indicate a cyber threat or network performance issue. Furthermore, real-time traffic monitoring gives engineers a continuous view of the network’s status, allowing them to respond promptly to anomalies. It is through these intricacies that engineers ensure the correct implementation of the protocol and maintain the network’s integrity.
Designing for Network Resilience and Redundancy: The Unbroken Chain
Network resilience and redundancy planning represent the unbroken chain that ensures the IEC 61850 network’s continued operation, even in adversity. It is the culmination of our cybersecurity odyssey, where every network element is fortified for resilience.
Intricacies: Achieving network resilience and redundancy requires meticulous planning and the implementation of specialized protocols. Engineers design redundant network paths to create alternative routes for critical control signals, minimizing the risk of communication breakdown due to link failures. High-availability Seamless Redundancy (HSR) and Parallel Redundancy Protocol (PRP) are deployed to guarantee zero packet loss during link failure. These protocols enable rapid switchover between redundant paths, ensuring the continuous flow of data and control signals.
With each intricate layer added to our cybersecurity strategy, we edge closer to our destination – a future where IEC 61850 networks are secure and efficient. In this future, critical industrial systems operate without interruption, fortifying the backbone of industries and ensuring the continuity of essential services. Our odyssey through the intricacies of IEC 61850’s cybersecurity realm safeguards modern society’s technological foundation, where security and efficiency are harmoniously balanced.
Edge Closer to Our Destination: A Secure and Efficient Future for IEC 61850 Networks

As we continue our journey into the heart of IEC 61850’s cybersecurity realm, we edge closer to a future where IEC 61850 networks embody robust security and exceptional efficiency. In this vision of tomorrow, critical industrial systems operate without interruption, fortifying the backbone of industries and ensuring the seamless continuity of essential services. Our odyssey through the intricacies of IEC 61850’s cybersecurity is not just a technical endeavour; it is a mission that safeguards the technological foundation of modern society, where security and efficiency are harmoniously balanced.
A Future of Security
In the future, IEC 61850 networks will be fortified like impenetrable fortresses. Security measures are woven into the very fabric of the network architecture, ensuring that cyber threats are thwarted at every turn. Intrusion Detection Systems (IDS) stand vigilant, identifying and responding to suspicious activity with unwavering precision. The deployment of advanced encryption protocols ensures the confidentiality and integrity of data, making it virtually impenetrable to cyber adversaries.
The culture of cybersecurity permeates every facet of industrial operations. Engineers, administrators, and stakeholders understand their critical role in safeguarding the network. Security awareness and training programs are commonplace, empowering individuals to recognize and report potential threats. Compliance with rigorous security standards like IEC 62443 is not just a requirement but a commitment ingrained in the organizational DNA.
A Future of Efficiency
Efficiency is the beating heart of this future. IEC 61850 networks operate with unmatched precision and optimization, delivering real-time control and data transmission with minimal latency. Advanced network segmentation ensures that different types of traffic flow seamlessly without contention, allowing critical control signals to traverse the network without delay. Quality of Service (QoS) configurations prioritize essential data streams, guaranteeing they receive the utmost attention and resources.
Network traffic analysis and monitoring tools give engineers unprecedented insights into network performance. These tools empower them to fine-tune and optimize the network continuously, ensuring it operates efficiently and implementing redundancy and resilience protocols such as HSR and PRP, guaranteeing uninterrupted operations, even in the face of unforeseen challenges.
A Future of Continuity
This envisioned future is one of uninterrupted continuity. Critical industrial systems operate without disruption, upholding the vital functions that sustain industries and society. Power grids remain stable, ensuring the reliable distribution of electricity. Manufacturing processes operate with unparalleled precision, minimizing downtime and maximizing productivity. Essential services, such as water supply and transportation, continue to function seamlessly, serving the needs of communities without interruption.
Safeguarding the Technological Foundation of Modern Society
Our odyssey through the intricacies of IEC 61850’s cybersecurity realm is not just an isolated journey but a mission to safeguard the very foundation upon which modern society rests. The convergence of security and efficiency within IEC 61850 networks bolsters the critical infrastructure that sustains our way of life. It ensures that the industrial systems underpinning our existence remain resilient, secure, and optimized in an increasingly interconnected world.
In this future, we find harmony between security and efficiency, where the fortification of IEC 61850 networks protects against threats and enhances the capabilities of industries. It is a testament to the unwavering commitment of engineers and cybersecurity experts who have embarked on this odyssey, leaving behind a legacy of innovation and resilience that resonates far beyond the boundaries of technology.
Conclusion: The Culmination of Our Cybersecurity Odyssey

As our journey through the intricate terrain of IEC 61850’s cybersecurity realm draws to a close, we find ourselves at the culmination of an intellectual odyssey that transcends mere technical exploration. It is a journey that embodies the convergence of knowledge, innovation, and unwavering dedication to safeguarding critical industrial systems. In this concluding chapter, we reflect upon the significance and lasting impact of our endeavours.
The Mission: A Pinnacle of Cybersecurity Excellence
Our mission to explore the depths of IEC 61850’s cybersecurity intricacies was not merely a technical endeavour but a quest to elevate the standards of cybersecurity excellence in industrial control systems. An odyssey took us through the labyrinthine corridors of network segmentation, advanced security protocols, device hardening, intrusion detection, network analysis, and resilience planning. Each step was a testament to the depth of knowledge, the precision of execution, and the unwavering commitment of engineers and cybersecurity experts who dedicated themselves to this cause.
The Vision: A Future Secure and Efficient
In our journey, we envisioned a future where IEC 61850 networks would be shining examples of security and efficiency. Critical industrial systems will operate seamlessly in the future, fortified by robust security measures. Security awareness would be ingrained in the culture of industrial operations, and compliance with rigorous standards would be second nature. Efficiency would be the hallmark of IEC 61850 networks, ensuring that real-time control and data transmission were achieved with unmatched precision. Network performance would be optimized through continuous monitoring and fine-tuning. The promise of redundancy and resilience would guarantee uninterrupted operations, even in the face of unforeseen challenges.
The Legacy: Safeguarding Modern Society
Our odyssey was not just a technical journey; it was a mission to safeguard the very technological foundation of modern society. The convergence of security and efficiency within IEC 61850 networks ensures the resilience and reliability of critical infrastructure. Power grids remain stable, manufacturing processes operate with precision, and essential services continue to function seamlessly. This legacy of innovation and resilience resonates far beyond technology, shaping the sustainability and continuity of industries and communities.
A Harmonious Future: Security and Efficiency
In closing, our odyssey through the intricacies of IEC 61850’s cybersecurity realm has been an endeavour that harmonizes security and efficiency, proving that these seemingly disparate ideals can coexist to fortify the backbone of industries. It demonstrates that the delicate balance between security and efficiency can be achieved in an interconnected world where the digital transformation of critical infrastructure is paramount. It is a testament to the unwavering commitment of engineers and cybersecurity experts, a legacy of knowledge and innovation that ensures the continued operation of essential services, and, ultimately, the safeguarding of modern society.
As we conclude our journey, we look forward to a future where IEC 61850 networks stand as bastions of security and efficiency, where the mission to protect critical industrial systems remains unwavering, and where the harmony between these ideals fortifies the technological foundation of modern society. Our odyssey may end, but its impact will endure, shaping the cybersecurity landscape for years.










