Building ICS cyberdefenses using NIST guidelines, Purdue Model, IEC 62443 standards

With the rising number of cybersecurity incidents, ongoing hardware and software vulnerabilities have placed demands on operational organizations, including within the critical infrastructure sector, to work on building their ICS cyberdefenses. To assist with this endeavor, organizations must include, among other security measures, provisions of the NIST guidelines, the Purdue Model that defines best practices for the relationship between industrial control systems (ICS) and business networks, and the IEC 62443 standards.
A robust network architecture improves ICS security and provides a foundation for additional security measures to be implemented over time. For example, the Purdue Model, NIST SP800-82, IEC 62443, and the SANS ICS410 Reference Model heavily emphasize on network segmentation and communication control between segments. Furthermore, as perimeter firewalls are deployed universally to protect enterprise environments from internet-based attacks, ICS environments should have protection at their many enforcement boundaries.
Although industrial processes are at lower levels in the Purdue Model, the most sensitive data and points of control are typically at Level 3, which is also where most attackers first access the ICS network from the business network. Fundamentally, ICS systems should use dedicated infrastructure independent of the business network.
Industrial Cyber reached out to industry experts to evaluate how organizations work towards developing ICS cyberdefenses within their architecture using these mechanisms.

Organizations can begin by accepting that the external threat landscape is incredibly volatile, widespread, and increasingly complex, Chris Thomas, vice president for industrial at Darktrace, told Industrial Cyber. “Given attacks at machine speed, organizations will need advanced technologies to augment their security postures. In the near future, we even expect attackers to begin using AI offensively, allied to 5G speed, completely overwhelming human security teams.”
“As attackers continue to innovate, businesses also cannot continue to rely on knowledge of past attacks and forward-looking assessments based on historical experience to protect them from emerging cyber threats,” Thomas said. “While many organizations map Common Vulnerabilities and Exposures (CVEs) to prepare for incoming threats, these CVEs often have no practical mitigation advice and only represent known and researched vulnerabilities, of which very few are investigated in the OT sphere. The absence of CVEs in an organization’s digital environment does not indicate the absence of risk,” he added.
Thomas also pointed out that self-learning AI technologies can grant comprehensive visibility into these complex industrial environments, identifying threats across OT, IT, and converged OT/IT in their earliest stages. “This AI detects novel and never-before-seen attacks without relying on rules, signatures, or lists of CVEs. Rather, the AI learns the normal ‘patterns of life’ for all devices, users, and controllers in an organization, using this dynamic understanding of ‘normal’ to autonomously detect subtle anomalies indicative of an attack as they emerge,” he added.

Amir Gil, CRO of SIGA OT Solutions, told Industrial Cyber that following the rise of OT cyber-attacks in 2021 and 2022, like the attacks on the water treatment plant in Oldsmar Florida, in February 2021, the Colonial Pipeline in May 2021, and the Iranian railway in July 2021, there were a lot of lessons learned in terms of the OT cyber architecture required the be well prepared and resilient to such attacks.
“The basic assumption when designing OT cyber defense is it’s not a matter of IF they will be attacked but a matter of WHEN they will be attacked,” Gil said. “Thus, ICS cyber defense shall be treated equally as safety is taken care of and the priorities should be very quick detection capabilities, response capabilities, recovery from failure, and only then prevention. It includes a mindset change, financial and organizational investment in people, tools, processes, and infrastructure,” he added.
Gil suggests that organizations start by carrying out a risk assessment by professional OT cyber consultants, pentest by professional OT cyber experts, and re-design architecture for quick detection of attacks, response, and recovery. He also recommends budget tools, process changes, and infrastructure upgrades, including thorough training of teams (IT, OT, security, safety) while budgeting and working on reducing risks according to the risk assessment and pentests results.

Digital transformation has far outpaced advances in ICS cyber resilience and the ability to manage a business and all its inherent risks, E. Christian Hager, vice president of business development at Fend Incorporated, told Industrial Cyber. “Add to that the sometimes-forgotten assets and remote access points resulting from an acquisition or consolidation, and it becomes clear that despite best efforts to uphold an architecture, gaps can emerge.”
Hager also pointed out that, most importantly, recent sophisticated (and even less sophisticated) attacks have shown that the threat actors have been residing in many networks for longer than was previously thought. “Late-stage cyber mitigation efforts will always leave gaps, and if a bad actor is already in the system, they will know exactly how to get around new ‘fixes,’” he added.
In most cases, it will always come down to proper cyber hygiene, training, staff awareness, and active patching of systems that will ultimately only close yesterday’s known cyberattack vectors, according to Hager.
“Most importantly, the OT teams (especially ICS/ SCADA engineers and technicians) need to change perspectives and embrace the mindset that they are indeed first responders and on the front lines of a conflict,” Hager said. “Checking the box for compliance purposes is not the same as actively trying to think like a cyber attacker and wondering what else might be done to prevent a breach. If a breach does occur to the IT network, the OT must be able to continue operations,” he added.

Rather than chasing the latest world event or buying the latest shiny security solution, organizations focusing on people, processes, and technology can make holistic improvements to their ICS programs, Bill Lawrence, SecurityGate.io’s chief information security officer (CISO), told Industrial Cyber. “Train the people as if you can’t find any more, enable them to perform thorough risk assessments and diagnostics, and commit to prioritized remediations of the OT systems that are most important to safety and business continuity. Having a security engineer who is fluent in whatever flavor of NIST or ISA/IEC assessments your company chooses, with added skillsets in things like the MITRE ATT&CK for ICS, will be quite beneficial,” he added.
Assessing the Purdue Model’s role in developing ICS cyber defenses within the organizational architecture, Thomas said that the Purdue Model is a well-known architecture for understanding complex ICS (OT) infrastructure. “Modern OT networks are deliberately segregated following the principles laid out and refined in the Purdue model architecture. However, given increased IT/OT convergence and even IT/OT interdependence, these boundaries are blurring in the traditional sense, and so visibility over the entire digital environment is both more critical and difficult to maintain than ever before,” he added.
“Through monitoring network traffic, Self-Learning AI can offer organizations direct visibility and cybersecurity coverage over everything from Level 1 (Basic Process) to supervisory functions (2, 3), DMZs, business logistics, enterprise networks (4, 5), and beyond into cloud networks and SaaS services,” according to Thomas. “This AI also provides indirect visibility into Level 0 (Process) as information transmits to the higher levels,” he added.
The Purdue model was built as a tool to analyze IT/ OT architecture in the 90s and is still relevant as a tool for analysis and planning ICS cyber, Gil said. “The early usage was mainly for IT/OT efficiency design and later adopted heavily by cyber stakeholders as a tool for cyber resilience analysis and architecture design. Still used by regulators, cyber tools vendors, analysts/consultants, integrators, and customers.”
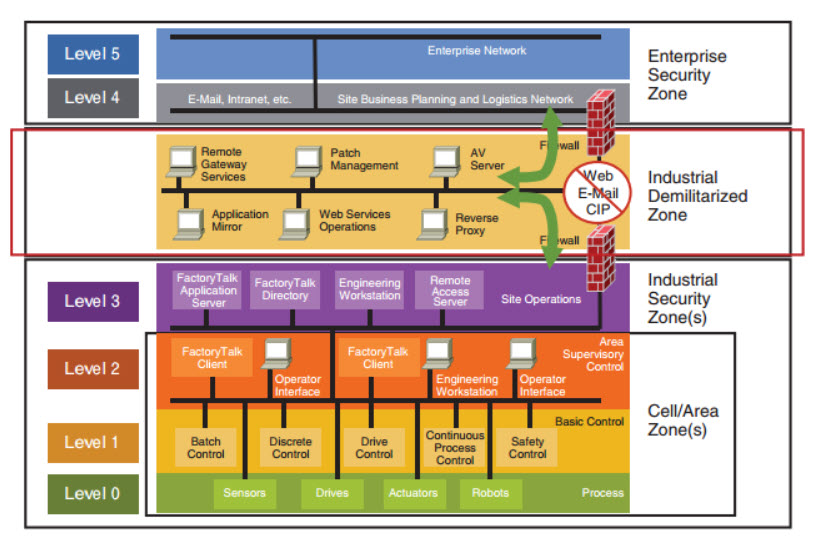
Gil further pointed out that the Purdue Model is not holy – it serves as a good tool for analysis and design, and see how it evolved in the last few years to include all the new components added to OT and IT and the convergence of IT and OT systems. “It’s not really important if organizations align to it or not – but is it helpful for them to improve their cyber defense and cyber resilience in a much more complex environment.”
The Purdue Model should, but does not, always play a role in developing cyber defenses, Hager said. “Devices in the lower end (Levels 0, 1) of the Purdue Model are inherently NOT protected from cyber threats and have zero cybersecurity built in. Yet we are seeing more of these new devices being connected via WIFI & Bluetooth to networks and the cloud, exposing a direct link to the ICS. Add to that that many of these components are manufactured in countries that have been sanctioned for selling insecure equipment to critical infrastructure providers or have state-sponsored cyber ops actively probing or attacking the US, and the problem becomes almost insurmountable,” he added.
Unfortunately, convenience (two-way remote access to ICS and SCADA) as part of a larger digital transformation has always won over security in the past, which was best highlighted by the Oldsmar, Florida breach 18 months ago, according to Hager. “DHS-CISA has recommended methods to mitigate unwarranted access to ICS, OT networks in critical infrastructure (and the IoT/IIoT devices that reside therein). These include DMZs, one-way communication (data) diodes, and air gaps,” he added.
“We have noticed that many water organizations are embracing the trend to protect Purdue level 2 & 3 infrastructure and move to a ‘digital twin’ strategy by replicating the OT data historian, data logger, or other servers on the enterprise network without allowing access to the OT network itself,” Hager said. “This can be done in several ways, most effectively with a DMZ or a data diode. That allows for real-time operational data & alerts to be securely extracted from the OT environment and used for predictive maintenance, on-call service, and reporting,” he added.
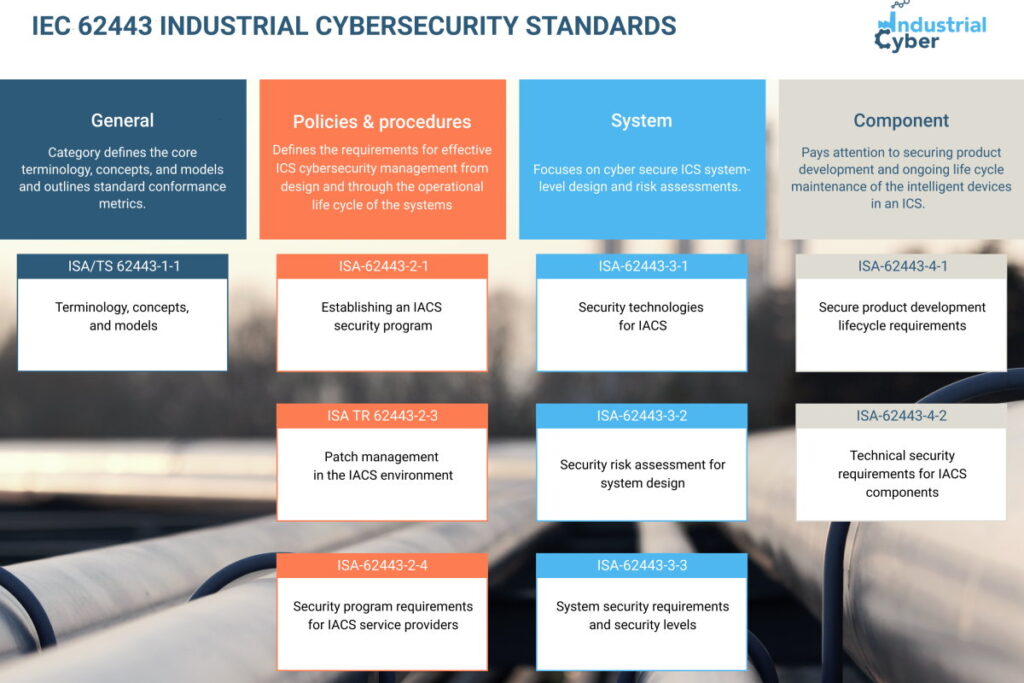
Lawrence said that the Purdue Model was useful in understanding the hierarchical arrangement of the domains and attempted separation of IT from OT network can control. “The push to add more connectivity between the layers and addition of IoT sensors and control devices has blurred the lines. Rather than a focus on a decades-old model, time would be better spent learning about risk-based approaches, such as the concepts of conduits and zones in ISA/IEC 62443 and the security benefits there,” he added.
Looking into the mechanisms that organizations have in place to ensure that their ICS cyber defenses within the architecture comply with the NIST CSF framework, NIST 800-82 provisions, and the ISA/IEC 62443 standards, Thomas said that ultimately organizations have the tall task of manually trying to adhere to these frameworks and provisions; however, more and more are turning to technology and automation to help with these guidelines.
“With self-learning AI technology, many organizations have augmented their efforts significantly with autonomous identification, protection, detection, and response,” according to Thomas. “This AI has enabled these businesses to combat and recover immediately from the sophisticated, novel, and rapidly moving cyber incidents, significantly bolstering operational resilience.”
Thomas said that these frameworks are guidelines to help organizations better understand their cyber-risk and ideally prevent operational downtime in the event of a breach. “As organizations with ICS environments become more complex and interconnected, understanding their networks, assets, and risks is essential. These frameworks and provisions are far more achievable and effective when human efforts are augmented with self-learning AI that can help businesses measure and mitigate cyber-risk as well as harden defenses against known and unknown threats,” he added.
“Organizations do not have built-in mechanisms to their compliance or alignment with NIST CSF framework, NIST 800-82 provisions, and the ISA/IEC 62443 – they must create and maintain such mechanisms,” Gil said. “Very similar to other security standards like ISO-27001 all these standards do not provide assurance that your organization is secured. These standards are just very good guidance that was built upon the commutative experience of critical infrastructure stakeholders – private/public CI organizations, regulators, auditors, CI consultants, etc. They provide a good base to create the right strategy of how to be more cyber resilient and how to implement this strategy- with specific vertical industry emphasis,” he added.
“As we lack the direct insight to the actual mechanisms within individual organizations, we, as an industry, have seen sector-specific efforts to bring ICS ‘cyber laggards’ up to certain standards as with the NIST SP 1800-10B specifically for ICS cyber within the manufacturing industry,” Hager said.
He also said that of great significance is the work that Idaho National Laboratory has done to form a foundation for the DoE’s National Cyber Informed Engineering (CIE) Strategy, which was released last month. “CIE and by logical extension, Consequence-Driven Cyber-Informed Engineering (CCE), allows critical infrastructure organizations across the board to actively align and optimize their own engineering processes with benchmarked thought principles and technology solutions. In essence, customization of each cybersecurity strategy to limit threats and the damage an attacker can do inside an organization,” he added.
Hager said that OT and ICS systems in the future should be designed with cybersecurity considerations built in from the start rather than bolted on at a later stage. It is the goal of CIE & CCE to ultimately ensure the alignment with 62443, 800-82, and other guidelines while a new system is designed or upgraded, he added.
From this perspective, CCE is generating tremendous attention in those sectors with ‘cyber-poor’ organizations that lack the budgets and resources (water & wastewater, smaller rural electric cooperatives, or small-scale renewable installations in the US), according to Hager. “That combined with service offerings that provide compliance guidance with proven technology solutions for a monthly subscription fee seems to provide a way for smaller organizations to address cybersecurity compliance and protection. It is still early, but the CIE and CCE guidelines should give the smaller, less sophisticated, and under-funded organizations a significant boost towards closing known cyber threat vectors and gaps in their ICS and OT networks more efficiently,” he added.
“Hopefully, organizations have the people (internal or consultants) who can effectively and efficiently work the NIST or ISA/IEC frameworks and standards to identify and start to remediate the gaps in the ICS cyber defenses around the OT infrastructure,” Securitygate.io’s Lawrence said. “This is hard work, requiring knowledgeable and trained people who know what the standards require and can make the necessary improvements to defenses. Hopefully, nobody turns to spreadsheets and email as their tools to take on these labors. There are much better ways to reduce OT security risk these days,” he concluded.










