ICS Cyber Risk, Security and Framework
Though awareness of ICS cyber security has increased dramatically over the past years there is still much to do
A survey by Automation World late last year stated that while progress has been made on the ICS cyber front, there great deal of work remains to be done to ensure the safety of automation systems from internal and external cyber threats.
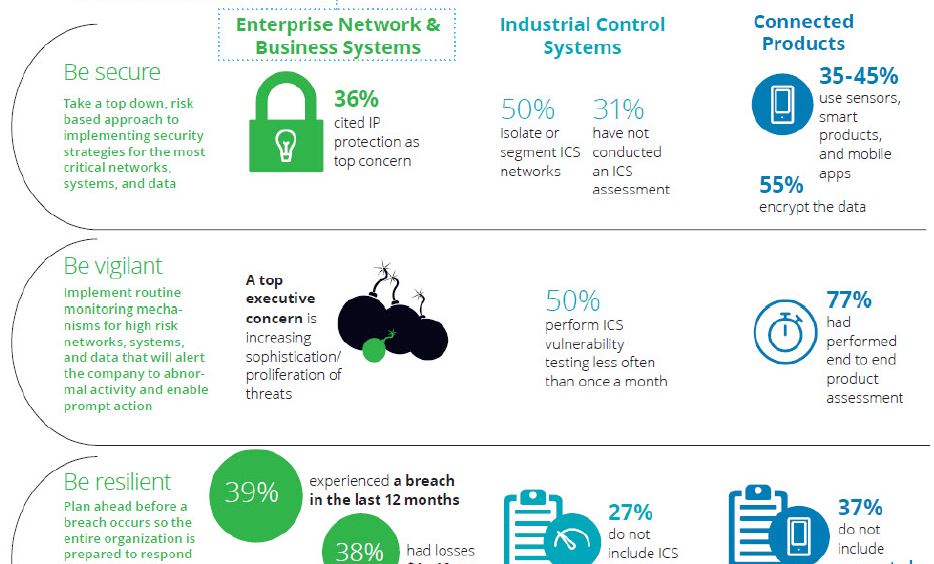
According to a recent study conducted by Deloitte and the Manufacturers Alliance for Productivity and Innovation (MAPI), two-thirds of manufacturers have conducted a risk assessment of their ICS security. That seems to be the good news.
The not so good news: Nearly one-third of manufacturers have not performed any cyber risk assessments of their ICS. Potentially more concerning is the fact that nearly two-thirds of the manufacturers responding to the Deloitte/MAPI survey indicating that they had performed ICS cyber risk assessments, did so by using internal resources. This leaves their assessments open to an array of internal biases.
The results of the Deloitte/MAPI survey are worthy of notice considering that the results are based on responses from 225 cyber risk executives at manufacturing firms ranging from industrial equipment, computer hardware and electronics manufacturers to suppliers of automation technology and consumer appliances. In addition, 39 percent of respondents had experienced a cyber incident in the last 12 months—meaning that cybersecurity issues are not an abstract threat for many of them.

According to Deloitte, the Top 10 questions for boards with ICS cyber security concerns
- How do we demonstrate due diligence, ownership, and effective management of cyber risk? Are risk maps developed to show the current risk profile, as well as timely identifying emerging risks we should get ahead of?
- Do we have the right leadership and organizational talent? Beyond enterprise systems, who is leading key cyber initiatives related to ICS and connected products?
- Have we established an appropriate ICS cyber risk escalation framework that includes our risk appetite and reporting thresholds?
- Are we focused on, and investing in, the right things? And, if so, how do we evaluate and measure the results of our decisions?
- How do our cyber risk program and capabilities align to industry standards and peer organizations?
- How do our awareness programs create cyber-focused mindset and cyber-conscious culture organization wide? Are awareness programs tailored to address special considerations for high-risk employee groups handling sensitive intellectual property, ICS, or connected products?
- What have we done to protect the organization against third-party cyber risks?
- Can we rapidly contain damages and mobilize response resources when a cyber incident occurs? How is our cyber incident response plan tailored to address the unique risks in ICS and connected products?
- How do we evaluate the effectiveness of our organization’s cyber risk program?
- Are we a strong and secure link in the highly connected ecosystems in which we operate?
[optin-monster-shortcode id=”dv4jqlr9fih8giagcylw”]










