NIST Cybersecurity Framework 2.0 reference tool released
Following last week’s release of the public draft of its NIST Cybersecurity Framework (CSF or Framework) 2.0, the National Institute of Standards and Technology (NIST) unveiled Tuesday its new CSF 2.0 Reference Tool. The resource allows users to explore the Draft CSF 2.0 Core (Functions, Categories, Subcategories, Implementation Examples) and offers human and machine-readable versions of the draft Core in JSON and Excel formats. The tool is set to leverage the NIST Cybersecurity and Privacy Reference Tool (CPRT), where users can view information across many of NIST’s cybersecurity and privacy resources.
NIST will continue to add additional features to the CSF 2.0 Reference Tool in the coming months (for example, Informative References will be added once CSF 2.0 is finalized in early 2024, which will help to show the connection between the CSF and other cybersecurity frameworks, standards, guidelines, and resources). Currently, the tool allows users to view and export portions of the Core using key search terms. It also allows users to create their own version of the CSF 2.0 Core with selected Informative References and provides a simple and streamlined way for users to explore different aspects of the CSF Core.
Future versions will enable users to create their own version of the CSF 2.0 Core with selected Informative References. As the CSF is designed to be used with other cybersecurity resources, this planned functionality to downselect Informative References will help organizations in building Profiles to implement the CSF.
NIST encourages feedback on this tool to be sent to [email protected].
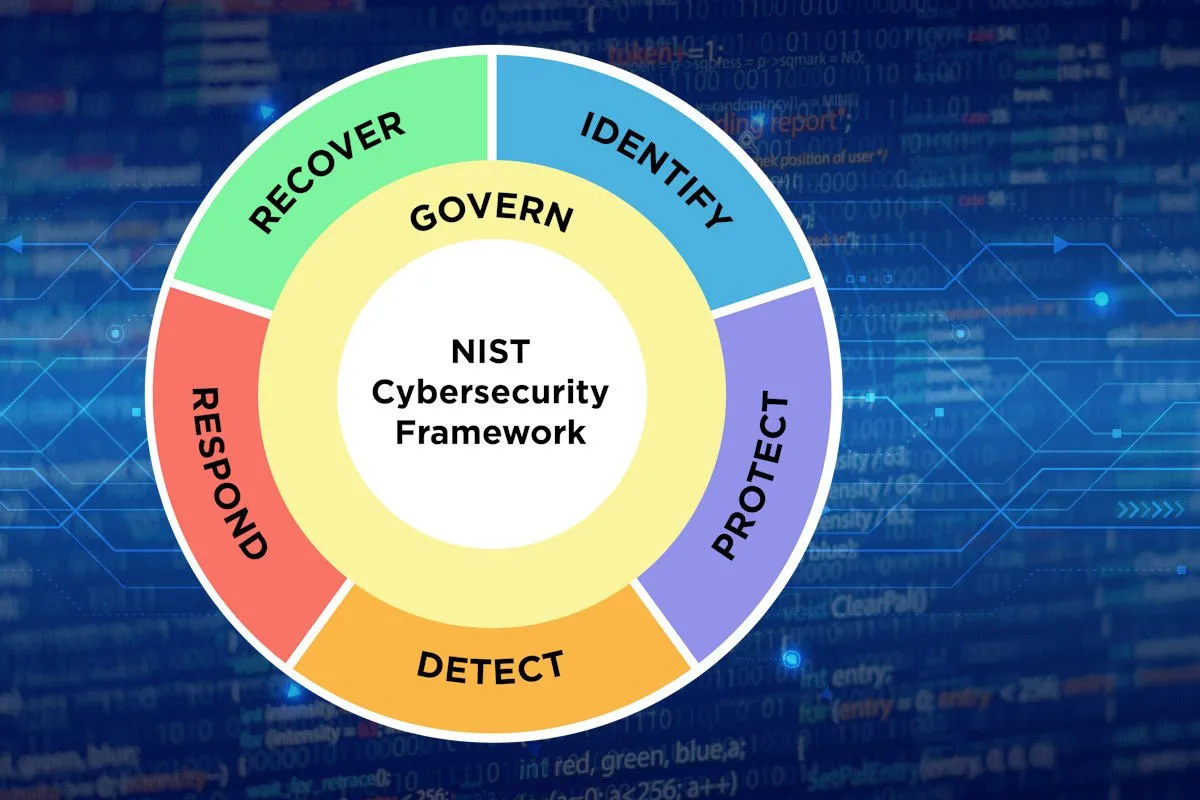
In the draft NIST CSF 2.0 document, the agency added a sixth, the ‘govern’ function to the five main pillars of a successful cybersecurity program. This function has been added to cover organizational context; risk management strategy; cybersecurity supply chain risk management; roles, responsibilities, and authorities; policies, processes, and procedures; and oversight. It focuses on people, processes, and technology expanded throughout the implementation of the framework.
The latest addition ‘govern’ function helps establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy while emphasizing that cybersecurity is a major source of enterprise risk and a consideration for senior leadership. The tool covers organizational context covering circumstances – mission, stakeholder expectations, and legal, regulatory, and contractual requirements – surrounding the organization’s cybersecurity risk management decisions are understood. Its risk management strategy aligns the organization’s priorities, constraints, risk tolerance, and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions.
It also includes cybersecurity supply chain risk management so that processes are identified, established, managed, monitored, and improved by organizational stakeholders. It also covers cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated, and organizational cybersecurity policies, processes, and procedures are established, communicated, and enforced. Furthermore, it covers results of organization-wide cybersecurity risk management activities and performance that are used to inform, improve, and adjust the risk management strategy.
The ‘identify’ function is used to help determine the current cybersecurity risk to the organization. Here, the CSF 2.0 Reference Tool will address asset management enabling the organization to achieve business purposes that are identified and managed consistent with their relative importance to organizational objectives and the organization’s risk strategy. The organization understands the cybersecurity risk to the organization, assets, and individuals, with improvements to organizational cybersecurity risk management processes, procedures and activities identified across all Framework Functions.
The ‘protect’ function uses safeguards to prevent or reduce cybersecurity risk. The tool addresses identity management, authentication, and access control to physical and logical assets limited to authorized users, services, and hardware, and managed commensurate with the assessed risk of unauthorized access. It also covers awareness and training, so that the organization’s personnel are provided cybersecurity awareness and training to perform their cybersecurity-related tasks. It also includes data security, where data is managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.
The tool also looks into platform security covering hardware, software, and services of physical and virtual platforms that are managed consistent with the organization’s risk strategy to protect their confidentiality, integrity, and availability. It also deals with technology infrastructure resilience where security architectures are managed with the organization’s risk strategy to protect asset confidentiality, integrity, and availability, and organizational resilience.
The ‘detect’ function finds and analyzes possible cybersecurity attacks and compromises. The tool analyzes continuous monitoring so that assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events, and delivers adverse event analysis covering anomalies, indicators of compromise, and other potentially adverse events that are analyzed to characterize the events and detect cybersecurity incidents.
The ‘respond’ function takes action regarding a detected cybersecurity incident. Here, the tool offers incident management enabling responses to detected cybersecurity incidents to be managed; incident analysis investigation is conducted to ensure effective response and support forensics and recovery activities; and incident response reporting and communication so that response activities are coordinated with internal and external stakeholders as required by laws, regulations, or policies. It also delivers incident mitigation activities which are performed to prevent the expansion of an event and mitigate its effects.
The ‘recover’ function restores assets and operations that were impacted by a cybersecurity incident. The tool identifies incident recovery plan execution and delivers restoration activities which are performed to ensure the operational availability of systems and services affected by cybersecurity incidents. It also offers incident recovery communication so that restoration activities are coordinated with internal and external parties.
Earlier this month, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) published its Cybersecurity Strategic Plan FY2024-2026 which outlines the agency’s central role in advancing toward a future where robust collaboration is the norm. It also works on rebalancing the responsibility for cybersecurity to be more effective and more equitable. The agency yet again highlighted the need to change how technology products are designed and developed so that exploitable conditions are uncommon and secure controls are enabled before products reach the market.










