NIST releases public draft of Cybersecurity Framework 2.0, invites feedback by Nov. 4
The National Institute of Standards and Technology (NIST) released Tuesday a public draft of its NIST Cybersecurity Framework (CSF or Framework) 2.0 that revises the framework to benefit all sectors, apart from the critical infrastructure sector. The document guides industry, government agencies, and other organizations to reduce cybersecurity risks, providing a taxonomy of high-level cybersecurity outcomes that can be used by any organization, regardless of its size, sector, or maturity, to understand, assess, prioritize, and communicate its cybersecurity efforts.
Feedback on the CSF 2.0 public draft, and related implementation examples draft, may be submitted to the NIST by Nov. 4.
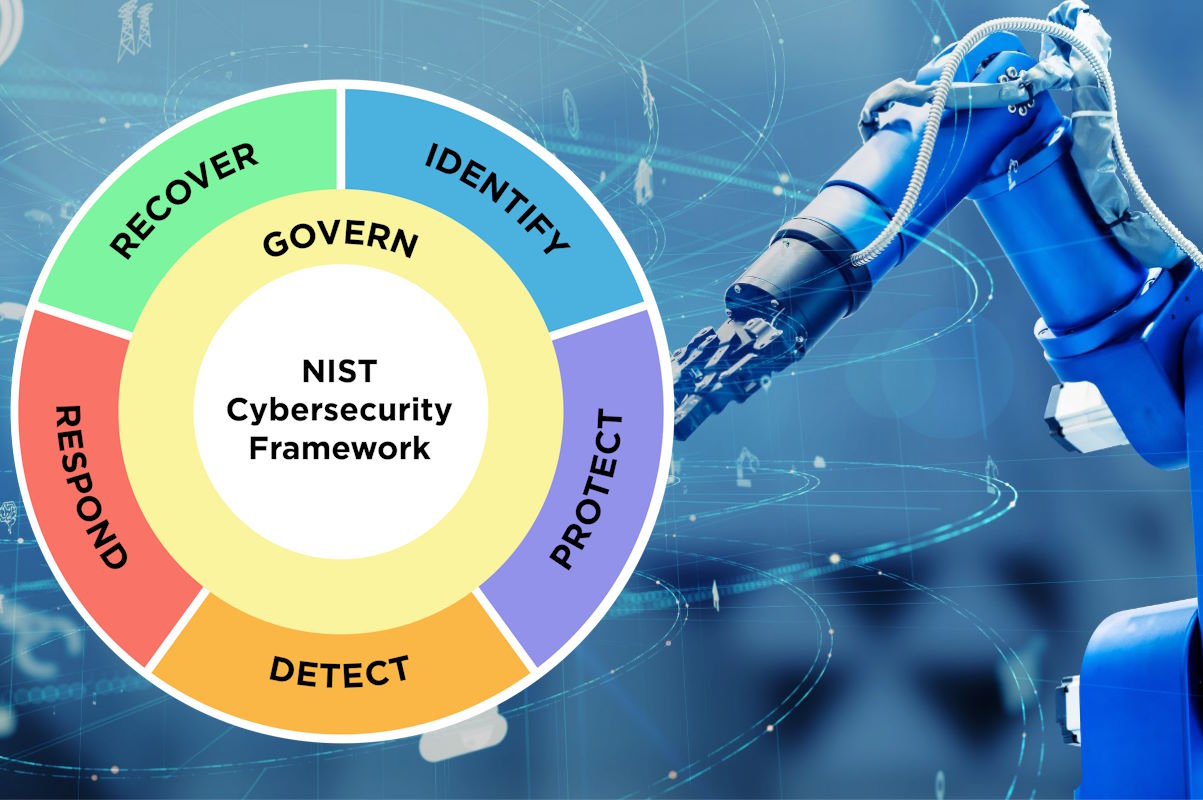
The Framework does not prescribe how the outcomes should be achieved. Rather, it maps to resources that provide additional guidance on practices and controls that could be used to achieve those outcomes. Furthermore, to the five main pillars of a successful cybersecurity program, NIST now has added a sixth, the ‘govern’ function, which emphasizes that cybersecurity is a major source of enterprise risk and a consideration for senior leadership.
The public draft document reflects changes in the cybersecurity landscape and makes it easier to put the CSF into practice for organizations. The update includes the latest version of the CSF Core, reflecting feedback on the April discussion draft. The publication does not contain Implementation Examples or Informative References of the CSF 2.0 Core, given the need to frequently update them. The Draft and initial Implementation Examples have been released under separate cover for public comment.
The agency seeks feedback on whether the draft revision addresses organizations’ current and anticipated future cybersecurity challenges, is aligned with practices and guidance resources, and reflects comments received so far. In addition, NIST requests ideas on the best way to present the modifications from CSF 1.1 to CSF 2.0 to support the transition. NIST also seeks feedback on how often Implementation Examples should be updated, and whether and how to accept Implementation Examples developed by the community.
“With this update, we are trying to reflect current usage of the Cybersecurity Framework, and to anticipate future usage as well,” NIST’s Cherilyn Pascoe, the framework’s lead developer, said in a media statement. “The CSF was developed for critical infrastructure like the banking and energy industries, but it has proved useful everywhere from schools and small businesses to local and foreign governments. We want to make sure that it is a tool that’s useful to all sectors, not just those designated as critical.”
The CSF 2.0 public draft reflects several major changes, including the framework’s scope has expanded, explicitly from protecting critical infrastructure, such as hospitals and power plants, to providing cybersecurity for all organizations regardless of type or size. This difference is reflected in the CSF’s official title, which has changed to ‘The Cybersecurity Framework,’ its colloquial name, from the more limiting ‘Framework for Improving Critical Infrastructure Cybersecurity.’
Until now, the CSF has described the main pillars of a successful and holistic cybersecurity program using five main functions: identify, protect, detect, respond, and recover. To these, NIST has added a sixth, the govern function, which covers how an organization can make and execute its own internal decisions to support its cybersecurity strategy. It emphasizes that cybersecurity is a major source of enterprise risk, ranking alongside legal, financial, and other risks as considerations for senior leadership.
Addressing the Govern function, NIST lays down establishing and monitoring the organization’s cybersecurity risk management strategy, expectations, and policy. Governance activities are critical for incorporating cybersecurity into an organization’s broader enterprise risk management strategy. It directs an understanding of organizational context; establishment of cybersecurity strategy and cybersecurity supply chain risk management; roles, responsibilities, and authorities; policies, processes, and procedures; and the oversight of cybersecurity strategy.
The Identity function helps determine the current cybersecurity risk to the organization. Understanding its assets and the related cybersecurity risks enables an organization to focus and prioritize its efforts consistently with its risk management strategy and the mission needs identified under Govern. This function also includes the detection of improvements needed for the organization’s policies, processes, procedures, and practices supporting cybersecurity risk management to inform efforts under all six functions.
The Protect function uses safeguards to prevent or reduce cybersecurity risk. Once assets and risks are identified and prioritized, Protect supports the ability to secure those assets to prevent or lower the likelihood and impact of adverse cybersecurity events. Outcomes covered by this function include awareness and training; data security; identity management, authentication, and access control; platform security (i.e., securing the hardware, software, and services of physical and virtual platforms); and the resilience of technology infrastructure.
The Detect function focuses on finding and analyzing possible cybersecurity attacks and compromises. It enables timely discovery and analysis of anomalies, indicators of compromise, and other potentially adverse cybersecurity events that may indicate that cybersecurity attacks and incidents are occurring.
The Respond function takes action regarding a detected cybersecurity incident. It supports the ability to contain the impact of cybersecurity incidents. Outcomes within this function cover incident management, analysis, mitigation, reporting, and communication.
The Recover function restores assets and operations that were impacted by a cybersecurity incident. It supports the timely restoration of normal operations to reduce the impact of cybersecurity incidents and enable appropriate communication during recovery efforts.
The public draft provides improved and expanded guidance on implementing the CSF, especially for creating profiles, which tailor the CSF for particular situations. The cybersecurity community has requested assistance in using it for specific economic sectors and use cases, where profiles can help. Importantly, the draft now includes implementation examples for each function’s subcategories to help organizations, especially smaller firms, to use the framework effectively.
A major goal of the CSF 2.0 public draft is to explain how organizations can leverage other technology frameworks, standards, and guidelines, from NIST and elsewhere, to implement the CSF. Bolstering this last effort will be the launch of a CSF 2.0 reference tool, which NIST plans to release in a few weeks. This online resource will allow users to browse, search and export the CSF Core data in human-consumable and machine-readable formats. In the future, this tool will provide ‘Informative References’ to show the relationships between the CSF and other resources to make it easier to use the framework with other guidance to manage cybersecurity risk.
While responses to NIST’s February 2022 request for information about the CSF indicated that the framework remains an effective tool for reducing cybersecurity risk, many respondents also suggested that an update could help users adjust to technological innovation, as well as a rapidly evolving threat landscape.
“Many commenters said that we should maintain and build on the key attributes of the CSF, including its flexible and voluntary nature,” Pascoe said. “At the same time, a lot of them requested more guidance on implementing the CSF and making sure it could address emerging cybersecurity issues, such as supply chain risks and the widespread threat of ransomware. Because these issues affect lots of organizations, including small businesses, we realized we had to up our game.”
NIST encourages concrete suggestions for improvements to the draft, including revisions to the narrative and Core. Feedback on the CSF 2.0 public draft, and related implementation examples draft, may be submitted to the NIST by Friday, Nov. 4, 2023. All relevant comments, including attachments and other supporting material, will be made publicly available on the NIST CSF 2.0 website.
The NIST CSF 2.0 public draft guides reducing cybersecurity risks by helping organizations to understand, assess, prioritize, and communicate about those risks and the actions that will reduce them. Those actions are intended to address cybersecurity outcomes described within the CSF Core. These high-level outcomes can be understood by a broad audience, including executives, government officials, and others who may not be cybersecurity professionals.
The outcomes are sector- and technology-neutral so that they provide organizations with the flexibility needed to address their unique risk, technology, and mission considerations. These outcomes can be used to focus on and implement strategic decisions that improve cybersecurity postures (or state) while also considering organizational priorities and available resources.
The NIST public draft identified that whether an organization is using the CSF for the first time or if it has used the framework previously, it is important to remember that the framework is designed to be used in conjunction with other cybersecurity frameworks, standards, and guidance. The agency provides other resources that are specific to the framework and its use on the CSF website, as well as hundreds of cybersecurity publications and other resources hosted on the NIST Computer Security Resource Center (CSRC) website and the NIST National Cybersecurity Center of Excellence (NCCoE) website.
It added that while these resources are not part of the Framework Core, they provide detailed information on cybersecurity risk management that supports the use of the framework. “Since the Framework is technology-neutral, organizations should also look for resources that are specific to their technologies, such as NIST Artificial Intelligence Risk Management Framework (AI RMF); SP 800-207, Zero Trust Architecture; and the NCCoE’s Implementing a Zero Trust Architecture project; and NIST Cybersecurity for IoT Program.
Last month, the NIST said that international engagement plays a crucial role in several of its ongoing efforts which include the update of the ‘Journey to the Cybersecurity Framework (CSF 2.0),’ revision of digital identity guidelines, and boosting awareness on the NIST Privacy Framework and IoT cybersecurity work. The agency has also undertaken several meetings and held workshops with international participants.










