NIST releases SP 800-61r3 draft on cybersecurity incident response recommendations for public comment
The National Institute of Standards and Technology (NIST) released an initial public draft of Special Publication (SP) 800-61r3 (Revision 3) for public comment. The draft intends to assist organizations with incorporating cybersecurity incident response recommendations and considerations throughout their cybersecurity risk management activities, as described by its Cybersecurity Framework (CSF) 2.0. Doing so can help organizations prepare for incident responses, reduce the number and impact of incidents that occur, and improve the efficiency and effectiveness of their incident detection, response, and recovery activities.
The public comment period is open through May 20.
Entitled ‘Incident Response Recommendations and Considerations for Cybersecurity Risk Management: A CSF 2.0 Community Profile,’ the SP 800-61r3 draft acknowledges the dynamic nature of incident response activities, which evolve frequently and differ significantly across technologies, environments, and organizations. Recognizing the impracticality of capturing and maintaining such information in a static publication, this version emphasizes enhancing cybersecurity risk management for all NIST CSF 2.0 functions to bolster an organization’s incident response capabilities.
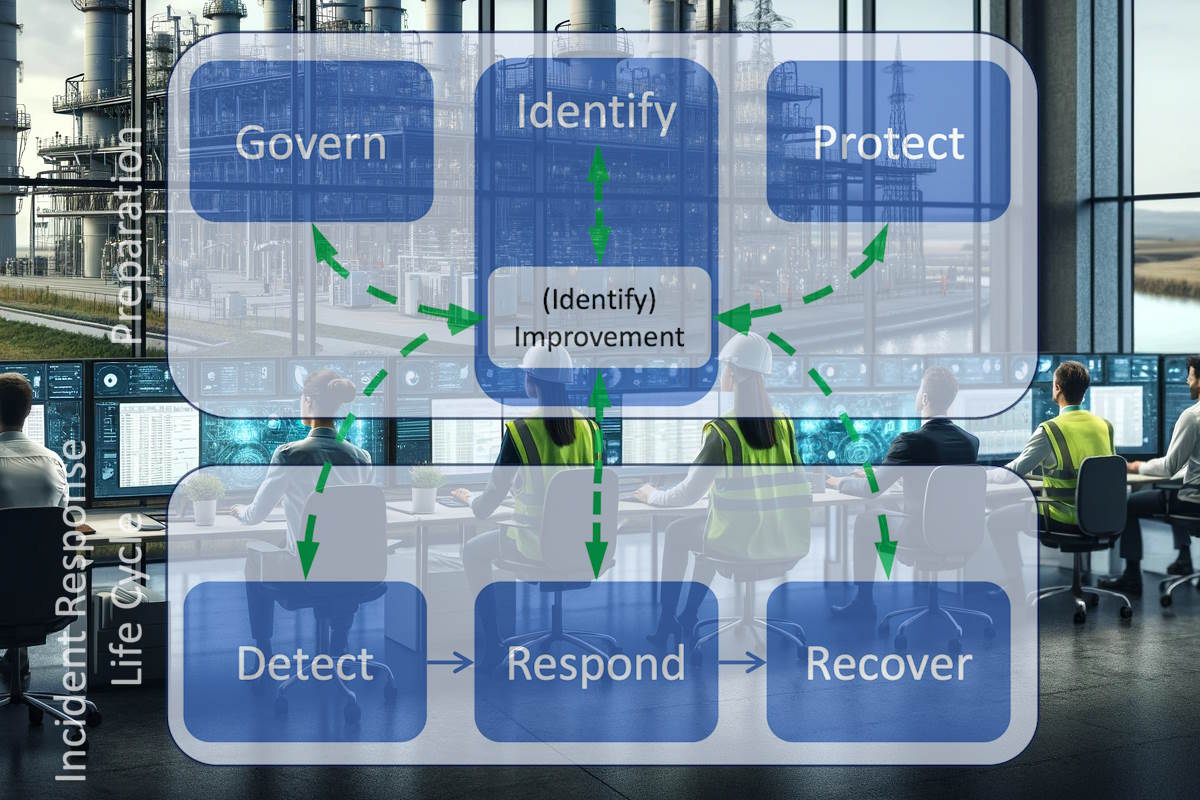
The CSF 2.0 Functions categorize cybersecurity outcomes at their highest level:
– ‘Govern’ focuses on establishing, communicating, and monitoring the organization’s cybersecurity risk management strategy, expectations, and policies.
– ‘Identify’ ensures a clear understanding of the organization’s current cybersecurity risks.
– ‘Protect’ involves utilizing safeguards to manage the organization’s cybersecurity risks.
– ‘Detect’ helps identify potential cybersecurity attacks and compromises for analysis.
– ‘Respond’ involves taking necessary actions once a cybersecurity incident is detected. – ‘Recover’ focuses on restoring assets and operations impacted by a cybersecurity incident.
The SP 800-61r3 draft identified that all six functions have vital roles in incident response. Govern, Identify, and Protect help organizations prevent some incidents, prepare to handle incidents that do occur, reduce the impact of those incidents, and improve incident response and cybersecurity risk management practices based on lessons learned. Detect, Respond, and Recover help organizations discover, manage, prioritize, contain, eradicate, and recover from cybersecurity incidents, as well as perform incident reporting, notification, and other incident-related communications.
It detailed that organizations should use the incident response life cycle framework or model that suits them best. “The model in this document is based on CSF 2.0 to take advantage of the wealth of resources available for CSF 2.0 and aid organizations that are already using the CSF. Regardless of the incident response life cycle framework or model used, every organization should take incident response into consideration throughout their cybersecurity risk management activities.”
Earlier, incident response activities were performed almost exclusively by incident handlers from the organization’s incident response team. Currently, while incident handlers are still critically important, most organizations increasingly recognize that the success of their incident response efforts depends on the participation of many internal and external parties who hold various roles and responsibilities and may be spread around the world.
Many organizations use more than one of these approaches, such as internally performing basic incident response and engaging third-party resources for assistance with certain incidents, the draft identified. Larger organizations may have multiple incident response teams, with each team responsible for a particular logical or physical segment of the organization. When this model is employed, the teams should be part of a single coordinated entity (e.g., a federation) to ensure that incident response processes, procedures, and training are consistent across the organization and that information is shared among teams.
Third parties may be contracted by an organization to perform incident response activities, with some filling a primary role and others involved in specific types. This shared responsibility model transfers some responsibilities to the provider, with clear responsibilities defined in a contract.
The incident response team should be aware of these responsibilities and restrictions. These responsibilities should be clearly defined in a contract, and the incident response team should be aware of the division of responsibilities, including information flows and coordination and the authority to act on behalf of the organization. This also includes restrictions on what the service provider can do, such as sharing sanitized incident information with other customers or making and implementing operational decisions.
Organizations should have policies that govern their cybersecurity incident response. While a policy is highly individualized to the organization, most incident response policies include a statement of management commitment; the purpose and objectives of the policy; the scope of the policy; and the definition of events, cybersecurity incidents, investigations, and related terms. It also includes roles, responsibilities, and authorities, such as which roles have the authority to confiscate, disconnect, or shut down technology assets; guidelines for prioritizing incidents, estimating their severity, initiating recovery processes, maintaining or restoring operations, and other key actions; and performance measures.
“Processes and procedures should be based on the incident response policy and plan,” the NIST SP 800-61r3 draft identified. “Documented procedures should explain how technical processes and other operating procedures should be performed. Procedures can be tested or exercised periodically to verify their accuracy and can be used to help train new personnel. While it is impossible to have detailed procedures for every possible situation, organizations should consider documenting procedures for responding to the most common types of incidents and threats.”
It added that organizations should also develop and maintain procedures for particularly important processes that may be urgently needed during emergencies, like redeploying the organization’s primary authentication platform.
The NIST SP 800-61r3 draft detailed a CSF Community Profile is a baseline of CSF outcomes that is created and published to address shared interests and goals for reducing cybersecurity risk among several organizations. A Community Profile is typically developed for a particular sector, subsector, technology, threat type, or other use case [CSF2.0].
The NIST’s CSF 2.0 Community Profile for incident response uses the CSF Core as the basis for highlighting and prioritizing cybersecurity outcomes that are important for incident response, making recommendations, and providing other supporting information for certain CSF outcomes within the context of incident response. The Community Profile is split into two tables – one addressing Preparation (Govern, Identify, and Protect), while another covering the Incident Response Life Cycle (Detect, Respond, and Recover).
Each CSF 2.0 Function, Category, and Subcategory has its row in one of the two tables. Each row’s relative priority within the context of incident response is indicated by either ‘High’ representing functions as a core incident response activity for most organizations; Medium which directly supports incident response activities for most organizations; and Low which indirectly supports incident response activities for most organizations.
Earlier this month, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) unveiled a proposed rule under the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA), aimed at enhancing the cybersecurity posture of critical infrastructure owners and operators to better defend against increasing threats and attacks. The move helps develop and implement regulations requiring covered entities to report covered cyber incidents and ransomware payments to CISA, enabling the agency to rapidly deploy resources and assist victims suffering attacks, analyze incoming reporting across sectors to spot trends, and quickly share that information with network defenders to warn other potential victims.










