NIST releases CSF 2.0 focused on governance and supply chain security across sectors
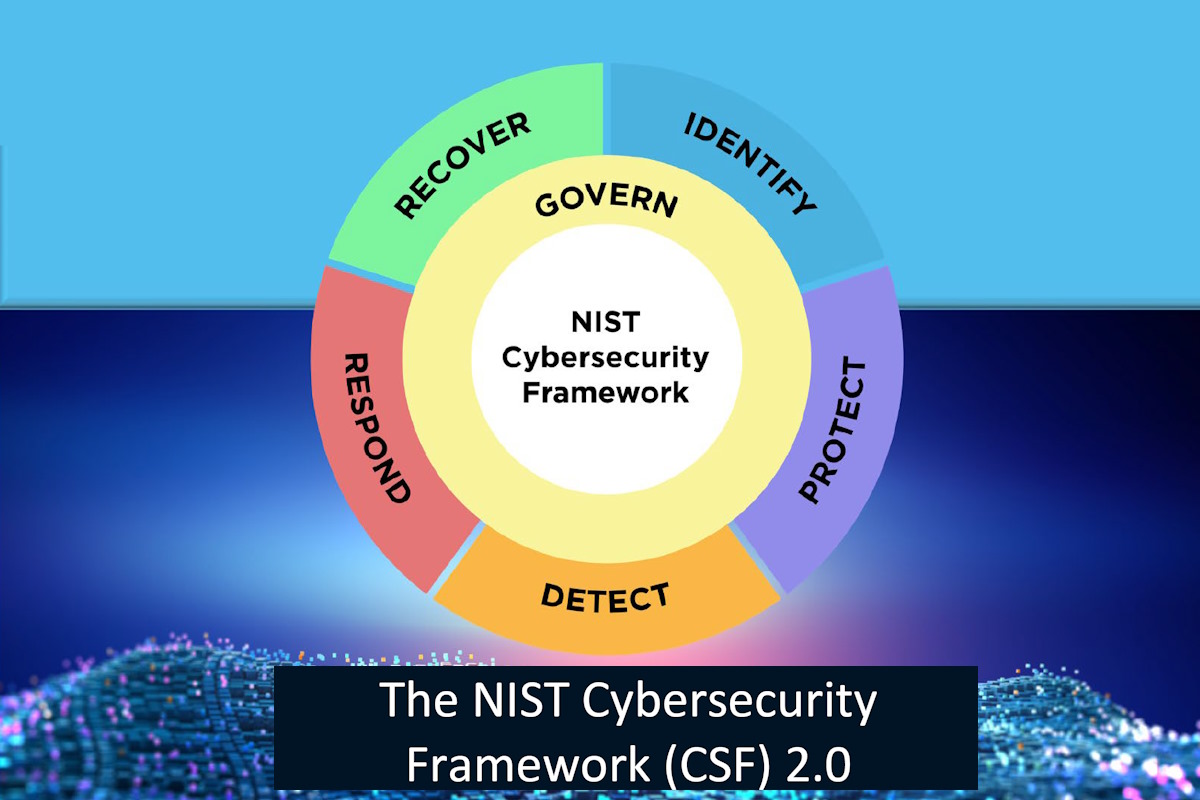
The National Institute of Standards and Technology (NIST) announced on Monday an update to its Cybersecurity Framework (CSF), broadening its scope to assist organizations across all sectors beyond its initial focus on critical infrastructure. The enhanced CSF 2.0 version includes refined core guidance and a comprehensive set of resources designed to support organizations in achieving their cybersecurity objectives. The update places a stronger focus on governance and supply chain security. This revision is the result of an extensive period of dialogue and public feedback, aimed at enhancing the framework’s effectiveness for a wider audience.
The newly released CSF 2.0 edition, crafted to cater to a broad audience, plays a pivotal role in implementing the National Cybersecurity Strategy. Its scope extends beyond the safeguarding of critical infrastructure, like hospitals and power plants, to encompass organizations across all sectors. Additionally, it introduces a novel emphasis on governance, highlighting the processes through which organizations formulate and execute informed cybersecurity strategies. This governance aspect underlines the importance of recognizing cybersecurity as a significant enterprise risk, on par with financial and reputational risks, necessitating attention from senior leadership.
Following a presidential Executive Order (EO) 13636, NIST first released the CSF in 2014 to help organizations understand, reduce, and communicate about cybersecurity risk. The framework’s core is now organized around six key functions: Identify, Protect, Detect, Respond, and Recover, along with CSF 2.0’s newly added Govern function. When considered together, these functions provide a comprehensive view of the life cycle for managing cybersecurity risk. Together, these Functions provide a comprehensive view of managing cybersecurity risk.
The Framework is also made up of CSF Core, a taxonomy of high-level cybersecurity outcomes that can help any organization manage its cybersecurity risks; CSF Organizational Profiles, a mechanism for describing an organization’s current and/or target cybersecurity posture in terms of the CSF Core’s outcomes; and CSF Tiers, an approach that can be applied to CSF Organizational Profiles to characterize the rigor of an organization’s cybersecurity risk management practices.
“The CSF has been a vital tool for many organizations, helping them anticipate and deal with cybersecurity threats,” Laurie E. Locascio, under secretary of commerce for standards and technology and NIST director, said in a media statement. “CSF 2.0, which builds on previous versions, is not just about one document. It is about a suite of resources that can be customized and used individually or in combination over time as an organization’s cybersecurity needs change and its capabilities evolve.”
“Developed by working closely with stakeholders and reflecting the most recent cybersecurity challenges and management practices, this update aims to make the framework even more relevant to a wider swath of users in the United States and abroad,” according to Kevin Stine, chief of NIST’s Applied Cybersecurity Division.
The CSF 2.0, along with supplementary resources, can be used by organizations to understand, assess, prioritize, and communicate cybersecurity risks. It is particularly useful for fostering internal and external communication at all levels (including across internal teams, from the C-Suite through middle management—and to those carrying out daily cybersecurity responsibilities). The CSF also seeks to improve communication with suppliers and partners and is intended to help organizations integrate cybersecurity-related issues with broader enterprise risk management strategies.
The updated framework anticipates that organizations will come to the CSF with varying needs and degrees of experience implementing cybersecurity tools. New adopters can learn from other users’ successes and select their topic of interest from a new set of implementation examples and quick-start guides designed for specific types of users, such as small businesses, enterprise risk managers, and organizations seeking to secure their supply chains.
A new CSF 2.0 Reference Tool simplifies the way organizations can implement the CSF, allowing users to browse, search, and export data and details from the CSF’s core guidance in human-consumable and machine-readable formats.
In addition, the CSF 2.0 offers a searchable catalog of informative references that shows how their current actions map onto the CSF. This catalog allows an organization to cross-reference the CSF’s guidance to more than 50 other cybersecurity documents, including others from NIST, such as SP 800-53 Rev. 5, a catalog of tools (called controls) for achieving specific cybersecurity outcomes.
Organizations can also consult the Cybersecurity and Privacy Reference Tool (CPRT), which contains an interrelated, browsable, and downloadable set of NIST guidance documents that contextualizes these NIST resources, including the CSF, with other popular resources. The CPRT offers ways to communicate these ideas to technical experts and the C-suite so that all levels of an organization can stay coordinated.
NIST plans to continue enhancing its resources and making the CSF an even more helpful resource to a broader set of users, Stine said, and feedback from the community will be crucial.
“As users customize the CSF, we hope they will share their examples and successes because that will allow us to amplify their experiences and help others,” he said. “That will help organizations, sectors, and even entire nations better understand and manage their cybersecurity risk.”
The CSF 2.0 improves on prior versions by making key updates, developing new resources and tools, and adjusting guidance based on the existing cybersecurity environment. By offering practical and actionable suggestions, NIST’s resources can help organizations immediately improve their cybersecurity posture because they focus on how the CSF can be implemented.
To better integrate related resources, NIST’s mapping solution demonstrates how users can move from CSF outcome statements to better cybersecurity in practice. New implementation examples enable users to review action-oriented steps to help them get started (or keep going).
The CSF’s use will vary based on an organization’s unique mission and risks. With an understanding of stakeholder expectations, risk appetite, and tolerance, an organization can prioritize cybersecurity activities to make informed decisions about cybersecurity expenditures and actions.
An organization may choose to handle risk in one or more ways — including mitigating, transferring, avoiding, or accepting negative risks and realizing, sharing, enhancing, or accepting positive risks — depending on the potential impacts and likelihoods. Importantly, an organization can use the CSF both internally to manage its cybersecurity capabilities and externally to oversee or communicate with third parties.
Regardless of the CSF’s utilization, an organization may benefit from using the CSF as guidance to help it understand, assess, prioritize, and communicate cybersecurity risks and the actions that will manage those risks. The selected outcomes can be used to focus on and implement strategic decisions to improve cybersecurity postures and maintain continuity of mission-essential functions while taking priorities and available resources into account.
Commenting on the CSF 2.0 release, Padraic O’Reilly, chief innovation officer at CyberSaint said in an emailed statement that the primary difference between 2.0 and the earlier versions (1.0 and 1.1) is the importance of governance.
“In the earlier versions, Governance was a category in Identify (ID.GV). Regulators and practitioners have over the last couple of years realized that the practice of cyber—perennially complex as always—can really be hobbled or advanced depending upon the mandate from above,” according to O’Reilly. “This can be seen most clearly in the elevation of cyber risk management’s profile, both in the Strengthening American Cybersecurity Act and the recent rule-making out of the SEC relating to 10-K disclosures. This covers the strategic aspects of cyber risk management, which really does require buy-in from the top of the organization.”
O’Reilly added that “2.0 also moved Supply Chain Risk Management into Governance out of Identify. There is a similar logic at play here, too, as SCRM (notoriously hard) is more likely to have success if there is an organizational mandate involved. Also, Incident Response has been promoted with two new categories in Respond and Recover. This is a recognition that the effectiveness of incident response directly influences impacts to the organization.”
Last week, the NIST released a summary of feedback on the final public draft of Special Publication (SP) 800-171, Revision 3, along with the initial public draft of SP 800-171A Revision 3. These documents focus on protecting the confidentiality of CUI (Controlled Unclassified Information) and recommend specific security requirements to achieve that objective.










