BlackByte ransomware group still active globally, Cisco Talos researchers reveal
Cisco Talos researchers revealed on Wednesday that they have been monitoring the BlackByte ransomware group and its affiliates for several months, infecting victims globally, from North America to Colombia, Netherlands, China, Mexico, and Vietnam. The researchers confirm they are still active after the FBI released a joint cybersecurity advisory in February. As of November last year, the group is said to have compromised multiple U.S. and foreign businesses, covering entities across at least three U.S. critical infrastructure sectors, including government facilities, financial, and food and agriculture.
Additionally, BlackByte is considered part of the big game ransomware groups, which are targeting large, high-profile targets, looking to exfiltrate internal data, and threatening to publicly release it, Cisco said. Like similar groups, they have their own leak site on the darknet. The actual TOR address of this site is frequently moved, it added.
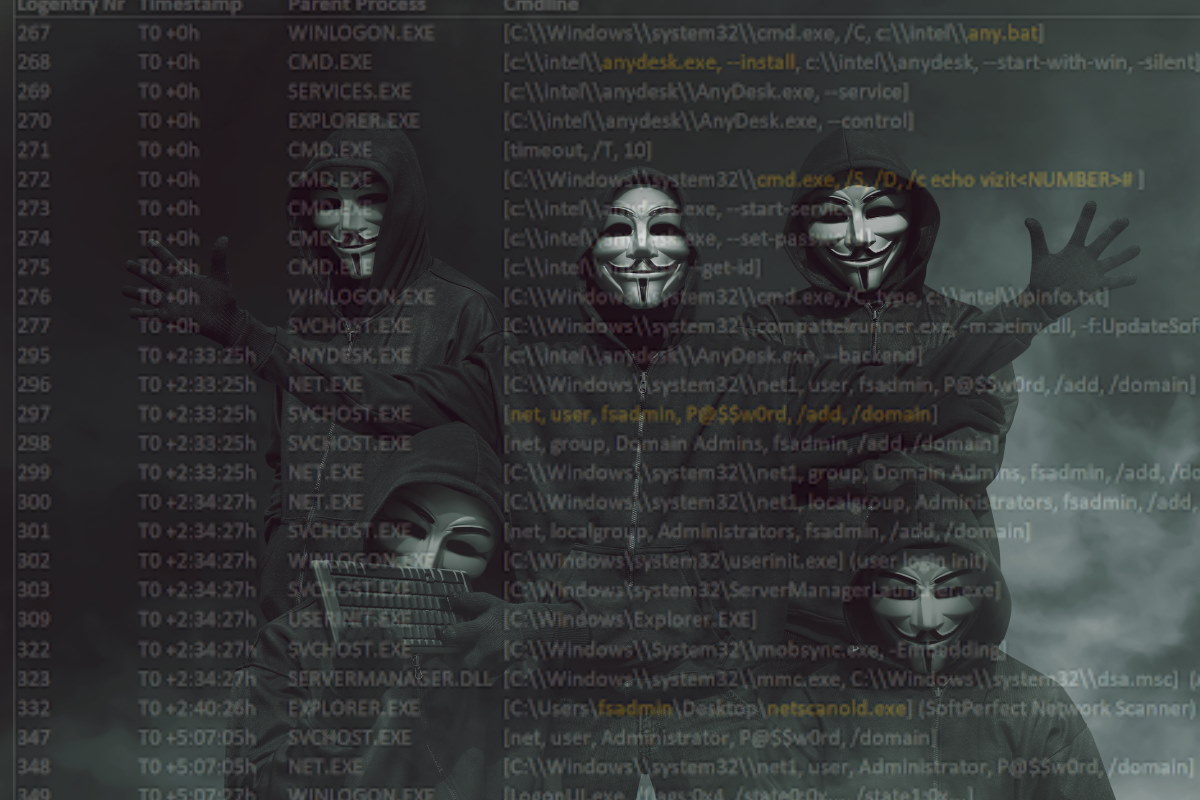
“The attack usually starts with a network entry point, either a previously compromised host or a software vulnerability which is exploitable from the network,” Cisco Talos researchers wrote in a blog post. “The former compromised host elevates local and domain account privileges and moves laterally by using standard penetration testing and legit administrator tools. In most incidents, they like to use the AnyDesk remote management software to control victim machines,” they added.
The BlackByte ransomware group also uses its software for its own goals and as a ransomware-as-a-service (RaaS) offering to other criminals. The RaaS is a business model between ransomware operators and affiliates in which affiliates pay to launch ransomware attacks developed by operators.
Cisco Talos researchers said that the BlackByte gang often uses phishing and/or vulnerable unpatched applications or services like vulnerable versions of SonicWall VPN or the ProxyShell vulnerability in Microsoft Exchange servers to gain access to the victim’s network. “These are usually known public vulnerabilities that the targets haven’t patched in a timely manner. Due to a lack of logs, we could not confirm the initial infection vector in the case below, but we have indicators that a vulnerable Microsoft Exchange Server was compromised, which matches the previously described behavior of the BlackByte actor,” they added.
Cisco analysis shows that the adversaries are installing the AnyDesk remote management software, as the researchers saw in Cisco Talos Incident Response engagements. “BlackByte seems to have a preference for this tool and often uses typical living-off-the-land binaries (LoLBins), besides other publicly available commercial and non-commercial software like ‘netscanold’ or ‘psexec’. These tools are also often used by Administrators for legitimate tasks, so it can be difficult to detect them as a malicious threats. It seems to be that executing the actual ransomware is the last step once they are done with lateral movement and make themselves persistent in the network by adding additional admin accounts,” they added.
“Unfortunately, we could not obtain the RANDOMNAME_n.EXE files, which are likely stages of the ransomware infection,” the researchers wrote. “We also tried to get them via the telemetry of our partners, but the hash was unknown to them, too. This points to the same trend that many big game ransomware groups moved to the tactic of using unique obfuscated files for every victim,” they added.
Talos’ research and other public reports about BlackByte are mainly pointing to vulnerable, outdated systems as the initial infection vector, the researchers said. “This threat shows how important it is to have a proper update strategy in place. If your organization is running a Microsoft Exchange Server or any other internet-facing system, make sure it always has the latest patch in place. The time window between the announcement of a new security vulnerability and its weaponization and used by criminals is getting smaller every year,” they added.
Given the threat landscape, It’s more important now than ever to have a multi-layered security architecture to detect these types of attacks. The adversary is likely to manage to bypass one of the other cybersecurity measures, but it is much harder for them to bypass all of them. These campaigns and the refinement of the TTPs used will likely continue for the foreseeable future.
The Cisco data comes at a time when global organizations have been warned of malicious cyber hackers often exploiting common weak security controls, poor configurations, and poor security practices, which can be used to breach initial access techniques. Last week, organizations were called upon to secure managed service providers (MSPs) and their customers from cyber threats after observing an increase in malicious cyber activity targeting such installations.










