GAO report calls for critical infrastructure agencies to assess adoption of cybersecurity guidance
A report by the U.S. Government Accountability Office (GAO) determined that critical infrastructure agencies need to assess the adoption of cybersecurity guidance. The audit institution also addresses the extent to which sector risk management agencies (SRMAs) have determined framework adoption by entities within their respective critical infrastructure sectors and identified improvements resulting from sector-wide use.
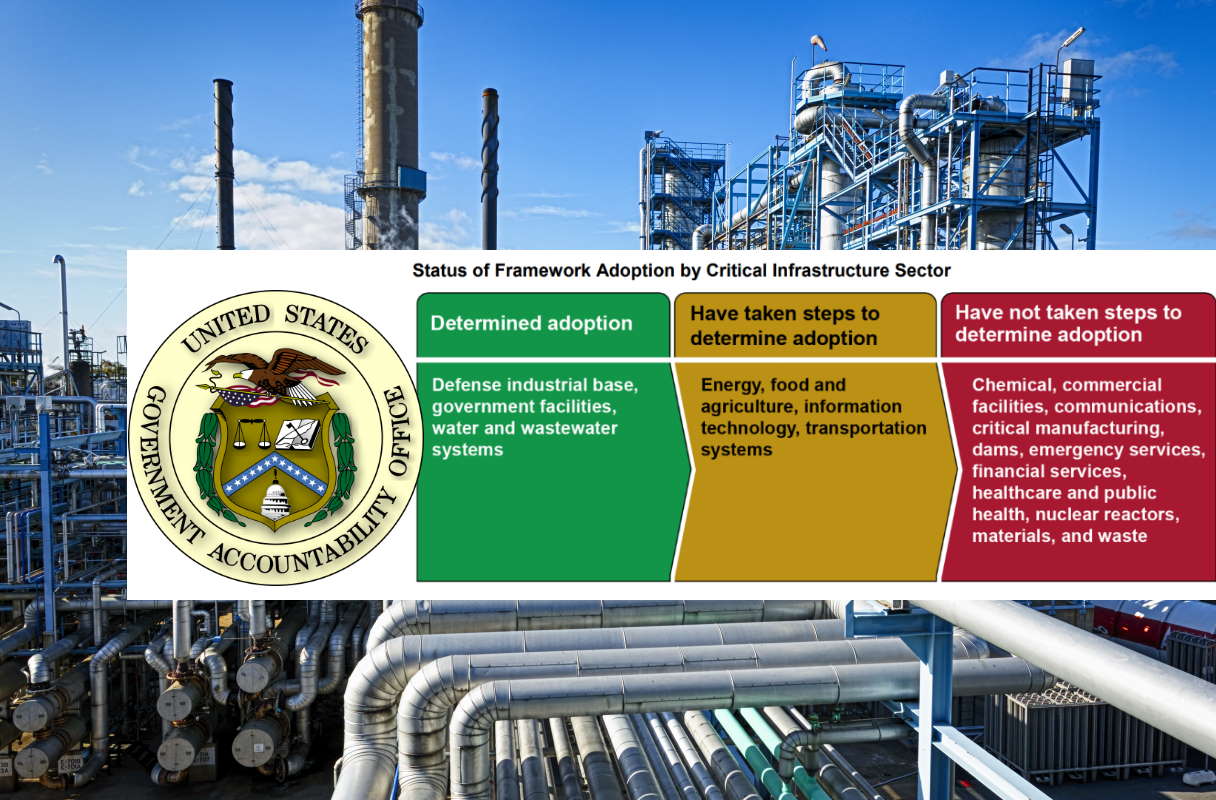
The SRMAs for three of the 16 critical infrastructure sectors have determined the extent of their sector’s adoption of the National Institute of Standards and Technology’s (NIST) framework for improving critical infrastructure cybersecurity, GAO said in its report this week. The agency analyzed documentation, such as requests for information, polls, and survey instruments, and also conducted interviews with agency officials from each SRMA and NIST, it said.
Water and wastewater systems, defense industrial base, and government facilities sectors have ‘determined adoption,’ GAO identified, while the SRMAs for the four sectors of energy, food and agriculture, information technology, and transportation systems have taken only initial steps to ‘determine adoption.’
GAO data showed that the U.S. Environmental Protection Agency (EPA) conducted, on a voluntary basis, technical assessments of water and wastewater utilities and determined whether and how these utilities used the framework. As of October last year, EPA determined that 146 out of 264 water and wastewater utilities that were eligible for the voluntary assessments had adopted the framework and obtained metrics on the utilities’ implementation of the framework’s security controls. In addition, 146 utilities completed both an initial assessment and two follow-up assessments. EPA captured the entities’ progress in an assessment dashboard, it added.
However, lead critical infrastructure agencies across the nine sectors of chemical, commercial facilities, communications, critical manufacturing, dams, emergency services, financial services, healthcare and public health, nuclear reactors, material and waste sectors have not taken steps to determine framework adoption, the GAO report said.
Regarding improvements resulting from sector-wide use, five of the 16 critical infrastructure sectors’ SRMAs have identified or taken steps to identify sector-wide improvements from framework use, as GAO previously recommended, the present report determined. “For example, the Environmental Protection Agency identified an approximately 32 percent overall increase in the use of framework-recommended cybersecurity controls among the 146 water utilities that requested and received voluntary technical assessments,” it added.
In addition, SRMAs for the government facilities sector identified improvements in cybersecurity performance metrics and information standardization resulting from federal agencies’ use of the framework, GAO said. However, SRMAs for the remaining 11 sectors did not identify improvements and were not able to describe potential successes from their sectors’ use of the framework, it added.
The SRMAs reported five challenges in identifying sector-wide improvements related to their use of the framework, including the voluntary nature of the framework, measuring the direct impact of using the framework, developing precise measurements of improvement, lack of centralized information-sharing mechanism, and lack of cybersecurity culture and capacity, GAO said in its report.
“The first four of these challenges have persisted since our prior report, while the last one is a newly identified challenge,” it added.
GAO also said in its report that since 2010, “we have made nearly 80 recommendations in public reports to enhance infrastructure cybersecurity, including measuring the adoption of the NIST framework. However, as of November 2021, a majority of these recommendations (nearly 50) had not been implemented,” it added.
The GAO report comes at an extremely precarious time for U.S. critical infrastructure agencies. Earlier this week, security agencies confirmed in a transnational joint cybersecurity advisory (CSA) this week that ransomware incidents were observed against 14 of the 16 U.S. critical infrastructure sectors, including the defense industrial base, emergency services, food and agriculture, government facilities, and information technology sectors in 2021.
The alert also revealed that “although most ransomware incidents against critical infrastructure affect business information and technology systems, the FBI observed that several ransomware groups have developed code designed to stop critical infrastructure or industrial processes.”
GAO had in December identified the need for the federal government to develop and execute a comprehensive national cyber strategy and strengthen its role in protecting the cybersecurity of critical infrastructure. The agency also said that ensuring the nation’s cybersecurity is on its ‘High-Risk List,’ and GAO urged federal agencies to act on it.










