Chinese hackers use Bronze Starlight ransomware to camouflage IP theft, cyber espionage
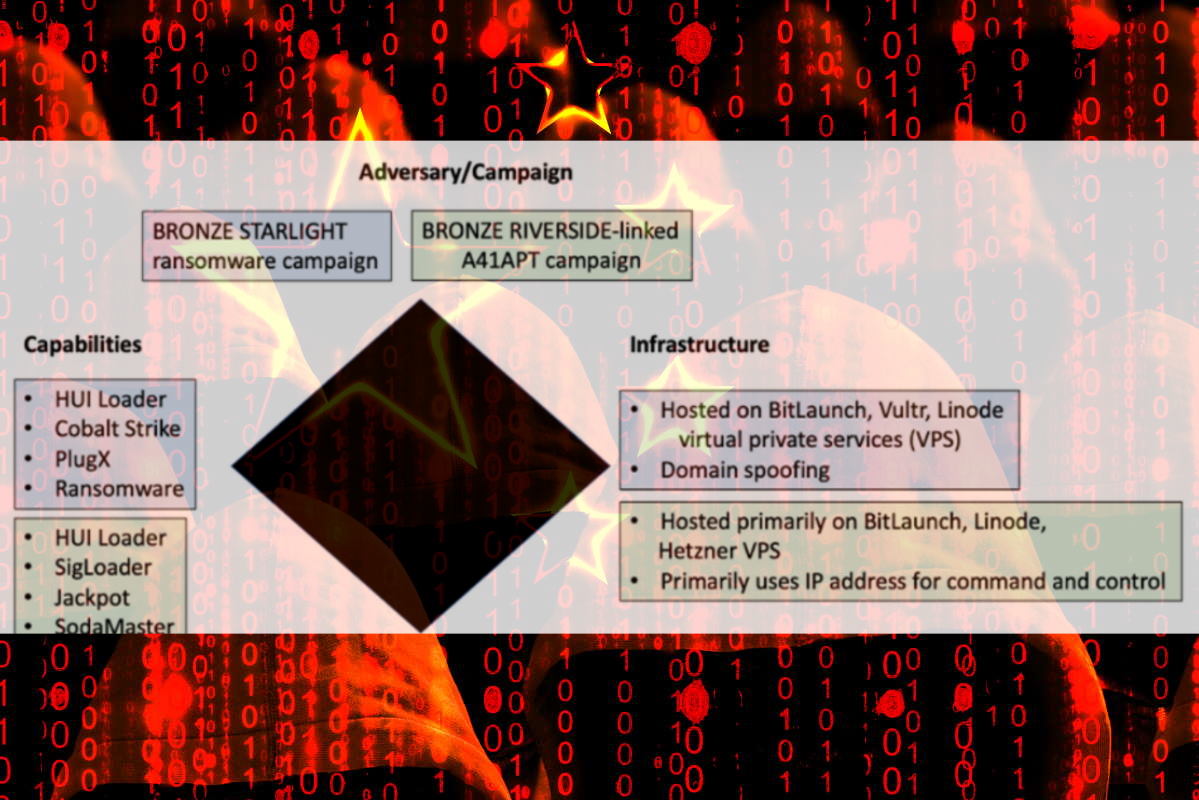
New research from the Secureworks Counter Threat Unit (CTU) team linked two HUI Loader activity clusters exclusively to China-based threat groups. The victimology, short lifespan of each ransomware family, and access to malware used by government-sponsored threat groups suggest that the main motivation behind Bronze Starlight may be intellectual property theft or cyber espionage rather than financial gain.
“The Bronze Riverside threat group is likely responsible for one cluster, which focuses on stealing intellectual property from Japanese organizations,” the CTU team wrote in a research post released Thursday. “The other cluster involves deployment of LockFile, AtomSilo, Rook, Night Sky, and Pandora post-intrusion ransomware. CTU researchers attribute this activity to the Chinese Bronze Starlight threat group,” it added.
The CTU researchers said that the ransomware could also distract incident responders from identifying the hackers’ true intent and reduce the likelihood of attributing the malicious activity to a government-sponsored Chinese threat group.
As of mid-April, 21 victims were listed across the AtomSilo, Rook, Night Sky, and Pandora leak sites. CTU researchers estimate that approximately 75 percent would be of interest to Chinese government-sponsored groups focused on espionage based on the victims’ geographic locations and industry verticals.
The victims include pharmaceutical companies in Brazil and the U.S., a U.S.-based media organization with offices in China and Hong Kong, electronic component designers and manufacturers in Lithuania and Japan, a law firm in the U.S., and an aerospace and defense division of an Indian conglomerate. The five victims not likely targeted for espionage include two real estate companies in the Americas, two small financial institutions in the U.S., and a small interior design company in Europe.
One Rook ransomware victim was a Kazakhstan bank, which strongly suggests that the threat actors are not based in the Commonwealth of Independent States (CIS). There is an unspoken universal agreement among Russian-speaking ransomware groups not to target entities in those jurisdictions.
The number and nature of LockFile victims are unclear. Third-party reporting suggests that victims represented verticals such as manufacturing, financial services, legal, and engineering and that most were located in the U.S. and Asia. CTU researchers identified two victims that are consistent with targeting a Chinese government-sponsored espionage-focused threat group: a financial services organization in India and a local government entity in the U.S.
CTU researchers said that victimology does not provide conclusive attribution. Chinese government-sponsored threat groups have broad targeting so that any ransomware operation could include victims of potential Chinese interest. Conversely, Chinese government-sponsored groups using ransomware as a distraction would likely make the activity resemble financially motivated ransomware deployments.
Though, the combination of victimology and overlap of infrastructure and tooling associated with government-sponsored threat group activity indicate that Bronze Starlight may deploy ransomware to hide its cyber espionage activity.
Secureworks said that the HUI Loader is a custom DLL loader whose name is derived from a string in the loader. “The malware is loaded by legitimate programs that are vulnerable to DLL search order hijacking. HUI Loader decrypts and loads a third file containing an encrypted payload that is also deployed to the compromised host. CTU researchers have observed HUI Loader loading RATs such as SodaMaster, PlugX, Cobalt Strike, and QuasarRAT,” it added.
Since early 2021, CTU researchers observed threat actors deploying HUI Loader in a cluster of activities associated with intellectual property theft. “This A41APT campaign primarily targets Japanese organizations and uses HUI Loader to load the SodaMaster RAT. The victimology and tactics, techniques, and procedures (TTPs) in this campaign align with BRONZE RIVERSIDE activity,” it added.
In mid-2021, CTU researchers began tracking the second cluster of activity that uses HUI Loader to load Cobalt Strike Beacon and deploy ransomware. CTU researchers attribute this second cluster of activity to the Bronze Starlight threat group.
In March this year, CTU researchers analyzed an updated version of HUI Loader that uses the RC4 cipher to decrypt the payload. The malware sample also attempts to circumvent host-based detection and protection measures by disabling Windows Event Tracing for Windows (ETW), disabling Antimalware Scan Interface (AMSI) functions, and hooking Windows API calls. Furthermore, the researchers identified code overlap between the updated HUI Loader samples and the Pandora ransomware.
Analysis of the Cobalt Strike Beacon samples loaded by HUI Loader revealed a link between AtomSilo, Night Sky, and Pandora ransomware. The Cobalt Strike Beacons were configured with a unique HTTP POST URI beginning with /rest/2/meetings and a watermark value of 0. “As of this publication, CTU researchers have only observed this configuration in Cobalt Strike Beacons associated with these ransomware families,” the researchers added.
The CTU researchers said that the operational cadence and victimology of LockFile, AtomSilo, Rook, Night Sky, and Pandora deployments do not align with conventional financially motivated cybercrime operations. In each case, the ransomware targets a small number of victims over a relatively brief period before it ceases operations, apparently permanently. The number of victims is unclear, as leak sites often do not list victims who pay ransoms early.
While Chinese government-sponsored groups have not historically used ransomware, the researchers said there is precedent in other countries. “For example, North Korea deployed WCry (also known as WannaCry) for financial gain, the Russian IRON VIKING threat group used NotPetya for its destructive capabilities, and the Iranian COBALT FOXGLOVE threat group used Pay2Key and N3tw0rm ransomware as a destructive wiper against entities in Israel,” they added.
CTU researchers assessed that Bronze Starlight likely uses ransomware to achieve tactical objectives, including destroying evidence, distracting investigators, and exfiltrating data. “Bronze Starlight compromises networks by exploiting vulnerabilities in network perimeter devices, including known vulnerabilities for which patches are available. The threat actors deploy HUI Loader to decrypt and execute a Cobalt Strike Beacon for command and control. They then deploy ransomware and exfiltrate sensitive data from the victim’s environment,” they added.
According to the SecureWorks researchers, the exploitation of known vulnerabilities and the use of the Cobalt Strike for command and control provide opportunities to detect and prevent Bronze Starlight intrusion activity before exfiltration or ransomware deployment.
The CTU team called upon network defenders to promptly implement a robust patch management process to address network perimeter vulnerabilities. However, breaches can occur even with preventative measures in place. Therefore, reactive measures such as a robust and tested incident response plan, real-time network monitoring and alerting, and an extended detection and response (XDR) solution are crucial for minimizing the impact of ransomware and other malicious activity.
In April, CTU researchers revealed that the China-based Bronze President threat group had targeted Russian speakers with updated PlugX. The shift in targeting could reflect a change in China’s intelligence collection requirements due to the war in Ukraine.










