EclecticIQ details Operation FlightNight targeting Indian government entities, energy sector
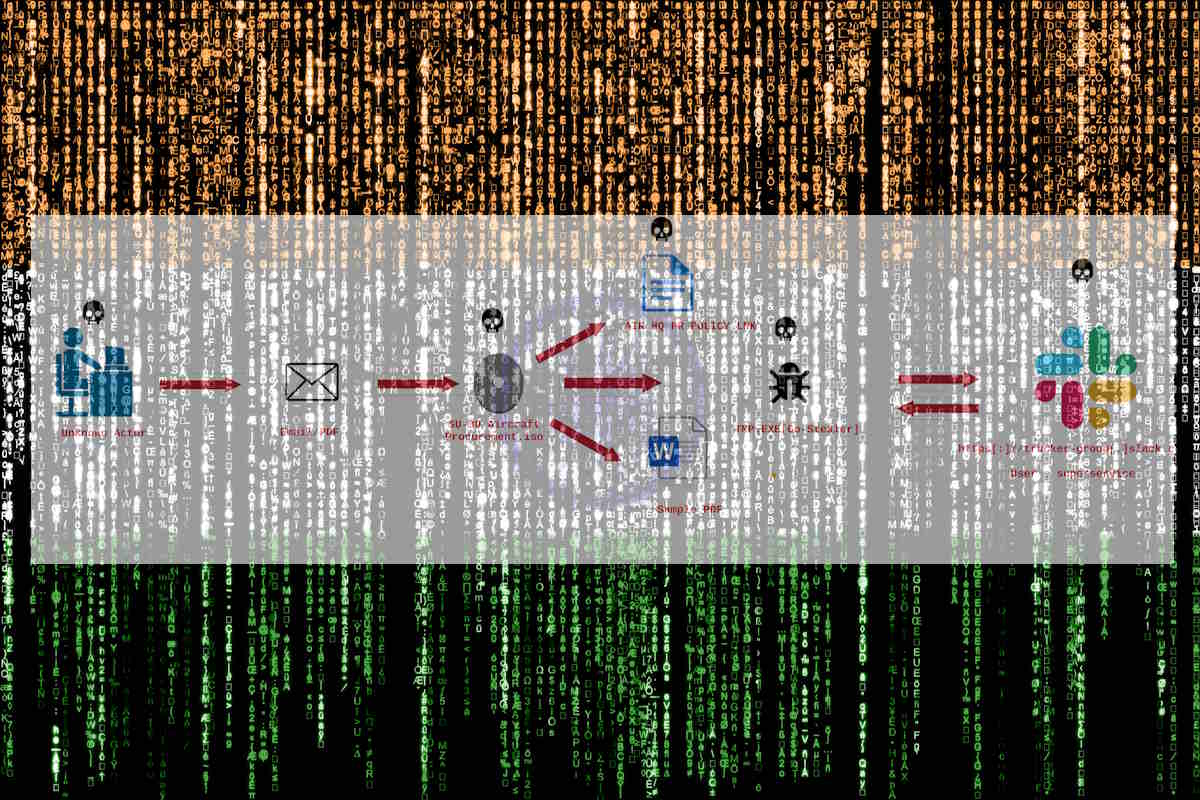
EclecticIQ analysts have uncovered an unidentified threat actor, known as Operation FlightNight, utilizing a customized version of the open-source information stealer HackBrowserData to target Indian government entities and the energy sector since March 7th, 2024. The analysis revealed that multiple government entities in India were affected, including agencies overseeing electronic communications, IT governance, and national defense.
Additionally, private Indian energy companies were targeted, resulting in the exfiltration of financial documents, employee personal information, and details on oil and gas drilling activities. The Operation FlightNight hackers managed to exfiltrate a total of 8.81 GB of data, prompting analysts to assess with medium confidence that this data could facilitate further intrusions into the Indian government’s infrastructure.
“The information stealer was delivered via a phishing email, masquerading as an invitation letter from the Indian Air Force,” Arda Büyükkaya, senior cyber threat intelligence analyst at EclecticIQ, wrote in a company blog post. “The attacker utilized Slack channels as exfiltration points to upload confidential internal documents, private email messages, and cached web browser data after the malware’s execution. EclecticIQ analysts dubbed the intrusion ‘Operation FlightNight’ because each of the attacker-operated Slack channels was named ‘FlightNight.’”
EclecticIQ shared its findings with Indian authorities to assist in identifying the victims and helping the incident response process, Büyükkaya wrote. “Behavioral similarities in the malware and the delivery technique’s metadata strongly indicate a connection with an attack reported on January 17, 2024. EclecticIQ analysts assess with high confidence that the motive behind these actions is very likely cyber espionage,” he added.
The Operation FlightNight hackers used a decoy PDF document, pretending it was an invitation letter from the Indian Air Force. This document was delivered inside an ISO file, which contained the malware in an executable form. Additionally, a shortcut file (LNK) was included to trick recipients into activating the malware.
“After victims mounted the ISO file, they encountered the LNK file invitation letter,” Büyükkaya detailed. “It appeared to be a harmless PDF document due to its misleading PDF icon. Upon executing the LNK file, victims inadvertently executed a shortcut link that activated the hidden malware. The malware immediately began exfiltrating documents and cached web browser data from the victim’s device to Slack channels.”
The post also displays the decoy document (Indian Air Force invitation) opened after the execution of the LNK file. “This strategy aims to deceive individuals into believing they are accessing a genuine document, while allowing the malware to operate covertly. EclecticIQ analysts observed the same PDF document in an attacker-controlled Slack channel where the stolen data was stored. Analysts assess with high confidence that the PDF document was very likely stolen during a previous intrusion and was repurposed by the attacker.”
Büyükkaya shows five different overlaps between Operation FlightNight and the Go-Stealer campaign that was previously observed by researcher ElementalX2 on January 17, 2024. “This comparison highlights specific areas of overlap between the two different incidents, offering strong evidence that both campaigns are likely the work of the same threat actor targeting Indian government entities,” he added.
During data exfiltration the malware is designed to target only specific file extensions, such as Microsoft Office documents (Word, PowerPoint, Excel), PDF files, and SQL database files on victim devices, very likely to increase the speed of the data theft. The malware starts to upload identified documents to Slack channels and finalize data exfiltration.
Operation FlightNight and the Go-Stealer campaign highlight a simple yet effective approach by threat actors to use open-source tools for cyber espionage. This underscores the evolving landscape of cyber threats, wherein actors abuse widely used open-source offensive tools and platforms to achieve their objectives with minimal risk of detection and investment.
The post also provided a breakdown of the key elements and their implications, including modified open-source offensive tools, utilization of Slack servers for data exfiltration, reduction of development time and cost, and implications for cybersecurity.
“The tactics used in Operation FlightNight and the Go-Stealer campaign highlight the importance of intelligence sharing and developing strategies to counteract these evolving threats. Organizations should enhance their security posture through continuous monitoring, adopting behavior-based detection mechanisms, and educating employees about phishing attacks,” it added.
Büyükkaya highlighted several detection and mitigation strategies that organizations can implement to safeguard from Operation FlightNight hackers. These measures include disabling password caching and auto-completion of usernames in web browsers through the Windows Group Policy. Additionally, enabling two-factor authentication (2FA) can help prevent unauthorized access in case of potential password exposure.
Detection of ISO mounting events can be achieved by monitoring Event ID 12 in the Microsoft-Windows-VHDMP-Operational logs or utilizing the SIGMA rule ‘file_event_win_iso_file_recent.’ Organizations can leverage Windows Group Policy to block ISO mounting events on specific devices, enable Command-Line Process Auditing to detect LNK file executions, and include repetitive or large numbers of outbound network traffic to unknown Slack channels should be considered a network anomaly, affected devices and users should be contained from the network to avoid further data exfiltration.
Last February, ThreatMon researchers provided details of SideCopy, a Pakistani threat group, having targeted Indian government entities using a spear-phishing email containing a macro-enabled Word document. The malware used is a new version of ReverseRAT, which has enhanced obfuscation and sleep calls to avoid detection. Recorded Future said in April 2022 that it observed in recent months likely network intrusions targeting at least seven Indian State Load Despatch Centres (SLDCs) responsible for carrying out real-time operations for grid control and electricity dispatch within these respective states.










