Global law enforcement agencies crack down on LockBit group, as Operation Cronos dismantles ransomware site
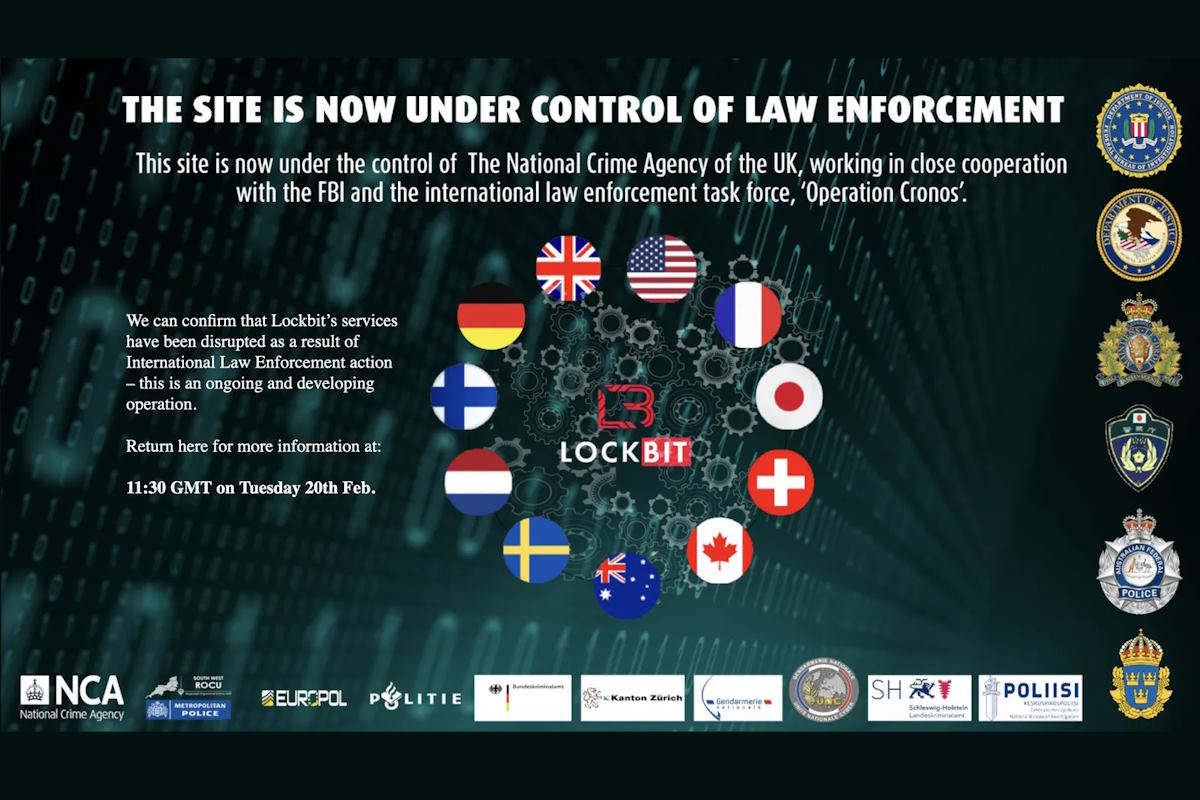
Global law enforcement agencies, including Europol, the U.S. Federal Bureau of Investigation (FBI), and the U.K.’s National Crime Agency, have dismantled a dark web site linked to the notorious LockBit ransomware group. Executed as ‘Operation Cronos,’ the action is part of an ongoing international effort to combat cybercrime. The dark web site, which LockBit used to publicly reveal the identities of victims refusing to pay a ransom for the release of their encrypted systems, was replaced with a law enforcement notice on Monday.
A post on the gang’s extortion website said “This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos.” The post also named other international police organizations from France, Japan, Switzerland, Canada, Australia, Sweden, the Netherlands, Finland and Germany.
The full scale of Operation Cronos is expected to also include a handful of arrests, sanctions, or further takedowns of key web infrastructure, including servers that LockBit ran on. Given that the operators behind the LockBit hacker group are thought to be located in Russia, arresting them is considered both unlikely and challenging to execute.
According to cybersecurity research website vx-underground, LockBit said in a statement in Russian and shared on X, formerly known as Twitter, that the FBI hit its servers that run on the programming language PHP, adding that “backup servers without PHP are not touched.”
In a separate Twitter message, the company disclosed that “every single known Lockbit ransomware group website is either offline or displaying a seized by EUROPOL page. It appears law enforcement has seized and/or taken down, at minimum, 22 Tor sites, in what is labeled ‘Operation Cronos’.”
It also shared a screenshot revealing what LockBit affiliates encounter when attempting to log into the LockBit panel.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) identified that the LockBit ransomware operation functions as a Ransomware-as-a-Service (RaaS) model where affiliates are recruited to conduct ransomware attacks using LockBit ransomware tools and infrastructure.
Due to the large number of unconnected affiliates in the operation, LockBit ransomware attacks vary significantly in observed tactics, techniques, and procedures (TTPs). This variance in observed ransomware TTPs presents a notable challenge for organizations working to maintain network security and protect against a ransomware threat.
Additionally, the FBI reports that since 2020, there have been approximately 1,700 instances of LockBit ransomware attacks within the U.S. Since the initial detection of LockBit’s activities in the U.S. on Jan. 5, 2020, the total sum of ransoms paid to LockBit by U.S. entities is estimated to be around $91 million. At the time, the LockBit-named ransomware was first seen on Russian-language based cybercrime forums.










