Kaspersky details common industrial TTPs, focuses on implants for gathering data
Researchers from the Kaspersky ICS CERT team published Monday the second part of its research based on an investigation of a series of attacks against industrial organizations. Covering the second-stage malware used to gather data, the research identified two types of implants used for gathering data on infected systems. Implants of the first type are designed to collect and archive various data on the local machine, while implants of the second type were used to collect information about removable drives, shadow copy their contents, and infect them with a worm, which was then used to exfiltrate data from air-gapped networks.
“Based on similarities found between these campaigns and previously researched campaigns (e.g., ExCone, DexCone), including the use of FourteenHi variants, specific TTPs, and the scope of the attack, we have medium to high confidence that a threat actor called APT31, also known as Judgment Panda and Zirconium, is behind the activities described in this report,” Kaspersky researchers wrote in their latest report. “In the campaign, the attackers aimed to establish a permanent channel for data exfiltration, including data stored on air-gapped systems. In total, we have identified over 15 implants and their variants planted by the threat actor(s) in various combinations.”
Earlier this month, Kaspersky announced that it investigated a series of attacks against industrial organizations in Eastern Europe in 2022. In the campaigns, the attackers aimed to establish a permanent channel for data exfiltration, including data stored on air-gapped systems.
The team identified over 15 implants and their variants planted by the threat actor(s) in various combinations, which were categorized into three stages: first-stage for persistent remote access and initial data gathering, second-stage for data gathering, and third-stage implants and tools used to upload data to C2.
The latest Kaspersky post revealed that in May 2022, a dedicated implant for gathering local files was discovered. “The implant uses a loading scheme based on the DLL hijacking technique, where the malicious DLL loader ensures persistence by creating a service named ‘WinSystemHost,’ decrypting and injecting the payload stored as binary data in a separate file into the memory of a legitimate process,” it added.
First, the implant creates a folder, then it creates a subfolder for temporary file storage and one subfolder for archived data storage. It then searches for an existing ‘WinRar.exe’ application in %ProgramFiles% and C:\Windows\SysWow64 subdirectories. If no ‘WinRar.exe’ is found, the implant terminates.
“The loop part of the main function starts with internal string decryption. Then the implant checks its config file, ‘C:\ProgramData\NetWorks\gfc,’ and if it doesn’t exist the implant removes all previously created folders and then terminates,” according to the researchers. “This indicates that the implant was designed to run in an environment prepared in advance, where a configuration file was already present.”
The config is encrypted with RC4 with the key ‘bGkds&sy6$^3gsa’ and is used to store another RC4 key, an IP filter, and a list of file extensions by which files to be copied to the subfolder for temporary file storage should be filtered. The implant also writes all paths to the file ‘1.log.’ Right after reading the config, the implant starts searching for files on all drives connected to the infected machine.
The researchers added that all files that have extensions matching the filter are copied to the subfolder for temporary file storage. Then ‘WinRar.exe’ is called to create an archive in ‘C:\ProgramData\NetWorks\ZZ.’ The archive file name is composed of the current date and time. Once an archive is created, the implant uses SHFileOperationW to remove files located in the subfolder for temporary file storage. In the last step of the loop, the implant goes to sleep for 10 minutes. In order to exfiltrate the data collected, the threat actor uses a stack of implants to upload the archives to Dropbox.
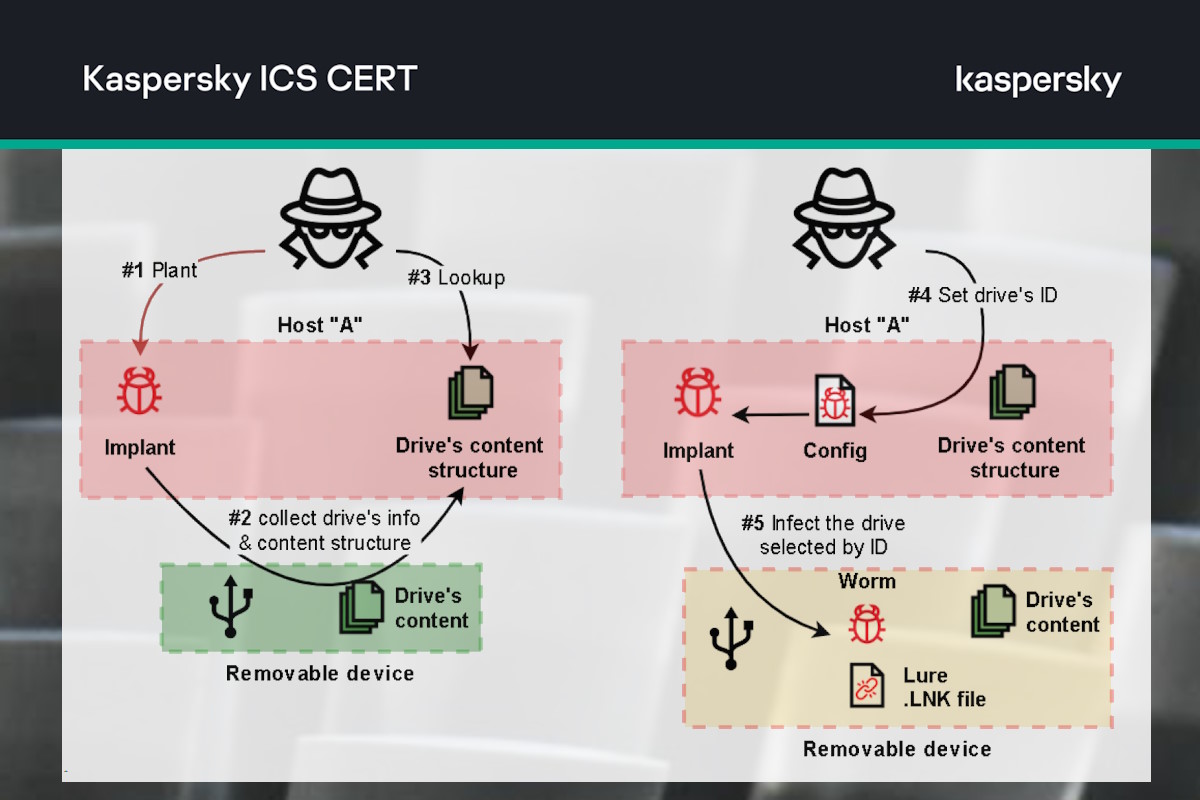
Last April, Kaspersky discovered malware designed to exfiltrate data from air-gapped systems by infecting removable drives. The malware discovered consists of at least three modules.
The researchers said that the first (main) module is responsible for handling removable drives, including collecting information about a drive, cloning each drive’s file system structure to a local temporary folder, and keeping the structure up to date. It also collects stolen files from a drive and plants second-step malware on newly connected drives, as well as capturing screenshots and window titles on the infected machine.
They added that first, the main module creates a folder in ‘%TEMP%,’ where it will store logs, info on connected drives, and the drives’ contents. The exact name of the folder is hard-coded into the module and, with this in mind, we can state that at least four variants of this implant have been deployed, based on the number of unique folder names found.
To infect a removable drive, the main module simply copies two files, ‘mcods.exe’ and ‘McVsoCfg.dll,’ to the drive’s root directory and sets the ‘Hidden’ attribute for both files, according to the researchers. “In addition, a fourth-step payload file named “89485416” or “89485418” may exist. If it exists, it will also be copied to the removable drive together with the second-step implant.”
The researchers identified that the third-step implant, ‘msguid[dot]exe,’ is quite small and simple – it is designed to execute a batch script with ‘cmd[dot]exe” to collect data and save the output to the drive’s ‘$RECYCLE[dot]BIN’ folder so that it can be collected by the main module of the malware (when connected to the originally infected host). “Then it looks for any fourth-step file to be executed and then deleted (if it exists).”
The fourth-step malware consists of two files – a simple dropper of the payload (similar to that used by second-step malware); and the payload, which is, in fact, a modified version of the first-step module and is also designed to collect information about a drive, collect files, capture screenshots and keystrokes, but without the routine responsible for infecting a removable drive. The fourth-step code is quite small and implements two main routines – collect and archive files, and capture keystrokes, the window title, and a screenshot.
The researchers added that the routine for gathering files is compiled from the same sources as the relevant routine used by the main module, while the code for capturing screenshots and the window title is new and so is the code for capturing keystrokes. Both modules (first-step and fourth-step) have similar configurations and data-saving routines.
Kaspersky concluded that the hacker attempted to make detecting and analyzing the threat more challenging by hiding the payload in encrypted form in a separate binary data file and by hiding malicious code in the memory of legitimate applications via DLL hijacking and a chain of memory injections. “The exfiltration of data from air-gapped networks is a common routine for many APTs and targeted cyberespionage campaigns. And, despite the existence of a broad variety of exfiltration methods, in most cases threat actors choose TTPs based on infecting removable media,” it added.










