FROZENBARENTS group targets energy sector, as Ukraine remains Russia’s biggest cyber focus this year
Google’s Threat Analysis Group (TAG) identified in a report this week that it continues to disrupt campaigns from multiple Russian government-backed attackers who are focused on the war in Ukraine in the first quarter of this year. The Google report also threw light on the FROZENBARENTS aka Sandworm group, attributed to Russian Armed Forces’ Main Directorate of the General Staff (GRU) Unit 74455 which targets the energy sector and continues to hack and leak operations.
Russian government-backed phishing campaigns targeted users in Ukraine the most, with the country accounting for over 60 percent of observed Russian targeting during the period, Billy Leonard, security engineer on Google’s Threat Analysis Group, wrote in a blog post. He added that FROZENBARENTS remains the most versatile GRU cyber actor with offensive capabilities including credential phishing, mobile activity, malware, external exploitation of services, and beyond. “They target sectors of interest for Russian intelligence collection including government, defense, energy, transportation/logistics, education, and humanitarian organizations.”
Leonard outlined that FROZENBARENTS continues to focus heavily on the war in Ukraine with campaigns spanning intelligence collection, IO, and leaking hacked data through Telegram, while it exploits EXIM mail servers globally and uses these compromised hosts as part of its operational network, a trend going back to at least August 2019. “These compromised hosts have been observed accessing victim networks, interacting with victim accounts, sending malicious emails, and engaged in information operations (IO) activity.”
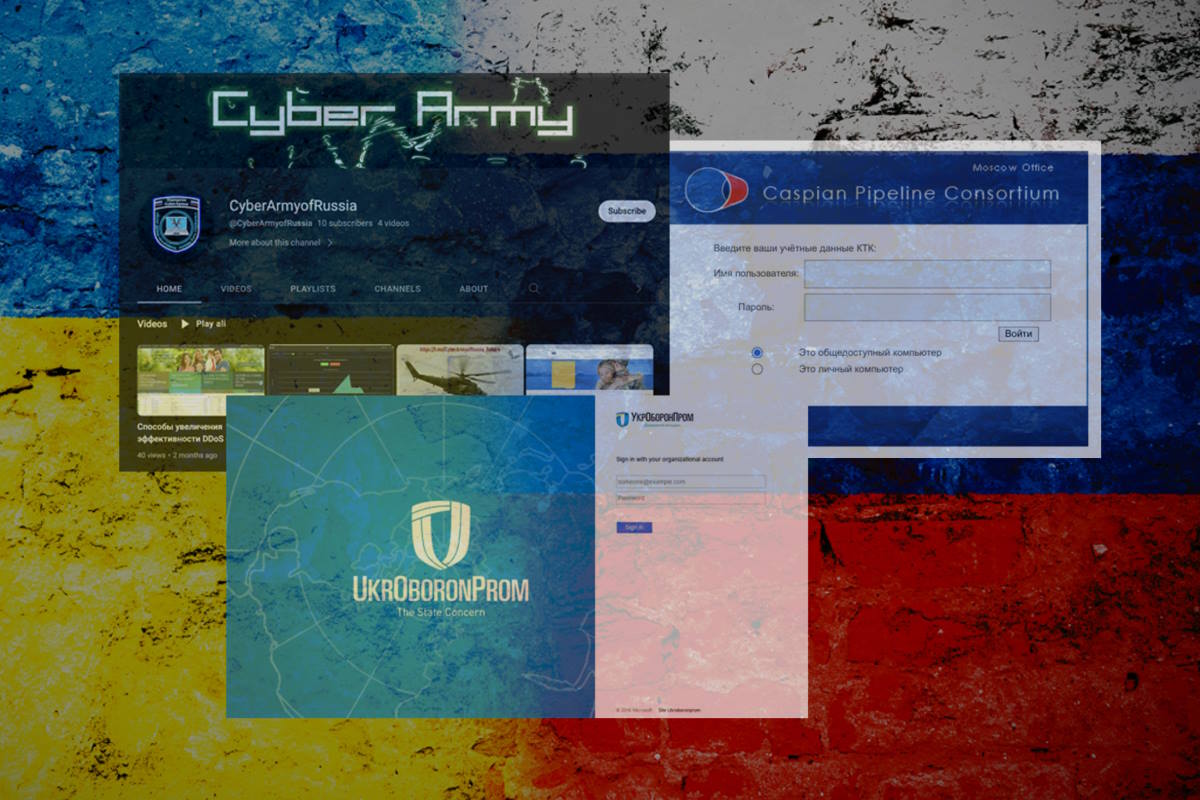
Since last November, FROZENBARENTS has engaged in a sustained effort to target organizations associated with the Caspian Pipeline Consortium (CPC) – which controls one of the world’s largest oil pipelines that transport oil from Kazakhstan to the Black Sea, and other energy sector organizations in Europe. “The first campaign targeted CPC employees, specifically the Moscow office, with phishing links delivered via SMS,” the post added.
Throughout the first quarter, Leonard confirmed that FROZENBARENTS conducted multiple campaigns against energy sector organizations in Eastern Europe, delivering links to fake Windows update packages hosted on a domain spoofing CPC. “If executed, the fake update would run a variant of the Rhadamanthys stealer to exfiltrate stored credentials, including browser cookies,” he added.
Leonard also revealed that beginning in early December 2022, FROZENBARENTS launched multiple waves of credential phishing campaigns targeting the Ukrainian defense industry, military, and Ukr[dot]net webmail users. “These phishing emails spoofed security and other system administrator-type notifications and in some cases were sent through third-party email campaign management services,” he added.
Active in the IO space, “FROZENBARENTS actors create online personas to create and disseminate news content as well as leak stolen data. These actors promote narratives that are pro-Russia, and against Ukraine, NATO, and the West,” Leonard said. “One persona, which TAG assesses is created and controlled by FROZENBARENTS actors, is ‘CyberArmyofRussia’ or ‘CyberArmyofRussia_Reborn’, which has a presence on Telegram, Instagram, and YouTube. Both the YouTube channel, terminated upon identification, and Instagram account received minimal engagement with a negligible number of subscribers or followers.”
Early this year, Leonard outlined another Russian GRU actor TAG tracks as FROZENLAKE (aka APT28) was especially focused on Ukraine. “In February and March, they sent multiple large waves of phishing emails to hundreds of users in Ukraine, continuing the group’s 2022 focus on targeting webmail users in Eastern Europe.”
Starting in early February 2023, “we saw FROZENLAKE using reflected cross-site scripting (XSS) on multiple Ukrainian government websites to redirect users to phishing pages – a new TTP for the group,” Leonard added. “The majority of observed phishing domains were created on free services and used for a short time, often a single campaign. When a user submitted their credentials on the phishing sites, they were sent via HTTP POST request to a remote IP address, which TAG analysis identified as compromised Ubiquiti network devices.”
The post also detailed PUSHCHA, a Belarusian threat actor, which has consistently targeted users in Ukraine and neighboring countries throughout the war. “Their campaigns typically target regional webmail providers such as i.ua, meta.ua and similar services. The phishing campaigns are targeted, focused on small numbers of users in Ukraine,” it added.
In the first quarter of 2023, Leonard said that TAG observed a coordinated IO campaign from actors affiliated with the Internet Research Agency (IRA) creating content on Google products such as YouTube, including commenting and upvoting each other’s videos. “The group has focused particularly on narratives supportive of Russia and the business interests of Russian oligarch Yevgeny Prigozhin, especially the Wagner Group,” he added.
CERT-UA previously reported on campaigns using RomCom malware to target government and military officials in Ukraine by the group behind Cuba ransomware, Leonard said. “This represents a large shift from this actor’s traditional ransomware operations, behaving more similarly to an actor conducting operations for intelligence collection.”
Additionally, TAG also observed campaigns from this actor targeting attendees of the Munich Security Conference and the Masters of Digital conference. “The attackers are using phishing URLs with spoofed domain names related to ChatGPT and OpenAI. The campaigns have been relatively small in volume, sent from spoofed domains, and targeting users’ Gmail accounts,” the post added.
Last Saturday, the State Service of Special Communications and Information Protection of Ukraine published its cyber incidents report for the first quarter of this year, showing a decrease in the number of attacks by pro-Russian groups targeting the commercial and financial sectors, the government and local authorities, and at the security and defense sectors. At the same time, the intensity of attacks on the energy sector and the mass media remains at the same level.
The U.K.’s National Cyber Security Centre (NCSC) issued an alert this week to critical national infrastructure (CNI) organizations warning of an emerging threat from state-aligned groups. The threat comes particularly from state-aligned groups sympathetic to Russia’s invasion of Ukraine and has emerged over the past 18 months.
Apart from this, lead security agencies in the U.S. and U.K. published a joint Cybersecurity Advisory (CSA) report on the tactics, techniques, and procedures (TTPs) associated with APT28’s exploitation of Cisco routers. The agencies assess that the APT28 group exploits a known vulnerability to carry out reconnaissance of routers and deploy malware, while also accessing poorly maintained Cisco routers and deploying malware on unpatched devices using CVE-2017-6742.










